Internet Security Research Group originally developed an Automated Certificate Management Environment (ACME) protocol for their Public CA, Let’s Encrypt. ACME is what drives Let’s Encrypt’s entire business model, which allows them to issue 90-day, domain validated SSL certificates, which can be renewed and replaced without the website owner’s intervention.
The objective is to set up an HTTPS server that will automatically obtain trusted certificates without any human intervention.
Overview
IETF developed an Automated Certificate Management Environment (ACME) for Automatic Certificate Management. ACME protocol provides an efficient way to validate that a certificate requester is authorized for the requested domain and automatically installs the certificates.
This validation is performed by requiring the requester to place a random string (provided by the CA or certificate manager) on the server for verification via HTTP or in a text record of the server’s Domain Name System (DNS) entry. Client programs, such as Certbot, can automatically perform all of the operations needed to request a certificate—minimizing the manual work. Let’s Encrypt, and several other public CAs support public-facing certificates’ automated management by using the ACME protocol. However, public CAs cannot perform ACME validation for certificates installed on systems inside organizational networks. External entities cannot make HTTP or DNS connections to internal systems. The certificate manager can make internal HTTP and DNS connections and be used for ACME-based certificate management on internal networks. A variety of CAs, certificate managers, and clients across a broad set of TLS servers and operating systems support the ACME protocol, which gives it an advantage. A disadvantage of ACME is that there is no primary method for triggering a certificate replacement in response to a certificate event (e.g., CA compromise).
ACME defines an extensible framework for automating the issuance and validation process of these certificates. The servers are allowed to obtain certificates without any human intervention.
ACME Protocol Model
ACME uses HTTPS as a transport for JavaScript Object Notation (JSON) Web Signature (JWS) objects. These are also called REST API.
ACME servers run on Certificate Authorities (CA) and respond to the client’s action if they are authorized. The client uses ACME protocol to request certificate management actions. ACME Clients are represented by “account key pairs.” A private key is used to sign all messages to the server, and the ACME server uses public access to verify the authenticity of the messages and ensure integrity.
How ACME Protocol Works
Setting Up
An ACME server needs to be appropriately configured before it can receive requests and install certificates. Steps to set up ACME servers are:
- Setting up a CA: ACME will be installed in a CA, so we would need to choose a CA on the domain we want ACME to be available.
- Enter the domain where ACME will be installed
- Choose on which CA it will be installed
- Authorization
- The client contacts the CA and generates an authorized key pair
- CA issues DNS or HTTPS challenges that the client responds to and solves to prove authority and control.
- CA also sends a nonce, a random number, which is signed using the client’s private key and sent back for verification to the CA.
This concludes the setting up of ACME. Post-installation, the automation would begin to work. There are a few steps that ACME takes:
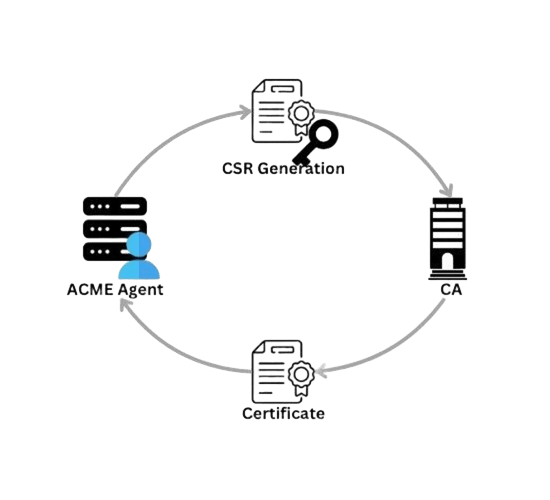
- Issuing/Renewing Certificates: ACME has the authority to issue or renew certificates to authorized users. At first, the client (or agent) generates a Certificate Signing Request (CSR), sent to the CA. The CSR is signed by the agent, which the CA can confirm is genuine and comes from the agent. The CA, after verification, issues the certificate for the domain and returns it to the agent.
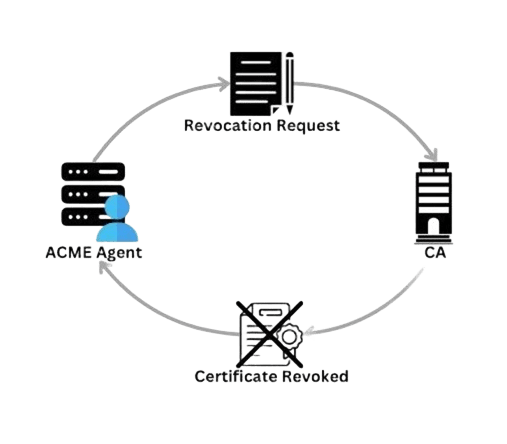
- Revocation: Like the previous process, the agent signs a revocation request sent to the CA. The CA again confirms the request’s authenticity and then revokes the certificate, publishing on CRL, OCSP, etc., for the PKI infrastructure.
ACME Protocol Functions
ACME uses various URLs and resources for different management functions it can provide. Some functions include:
- New Nonce
- New Registration
- New Application
- New Authorization
- Revoke Certificate
- Key change
Advantages
ACME provides an automated way to give certificates and revoke them quickly, without human error. Apart from these, there are a few advantages to look out for…
- ACME is free, which lets any domain owner get a trusted certificate at no cost.
- As previously stated, the ACME automates the certificate lifecycle with no human error.
- ACME can be used by anyone, which supports uniform protocols for all functions instead of separate APIs.
- They are supported by open-source, which helps to impact the whole community and grow more impactful projects, enhancing security.
- In case of a compromise, ACME can help quickly mitigate the issue, replace the old certificates with new ones, and switch to a new CA.
Conclusion
The ACME framework provides an effective and efficient way to manage SSL/TLS certificates, reducing the need for manual intervention and minimizing human error Great benefits offered to ACME domain owners due to capabilities issuing and cutting certificates quickly and free of charge. Encryption consulting can help implement and execute ACME-based certificate management solutions, ensuring seamless and secure certificate lifecycle management.

