The present world sees more and more organizations migrating to Cloud Service Providers to get the advantages associated with cloud computing, such as cost saving, security, flexibility, mobility, and sustainability. Out of those, Security is a critical aspect of any Cloud Service model, as it is applicable to any Cloud Service offerings that involve sensitive data.
Today we will discuss the Microsoft Azure’s Key Vault service in the above context.
Now, let us understand the actual meaning of vault – it is a treasury, which is used to store your valuable items. When we comprehend this meaning in reference to the Azure Cloud world, it gives the correct impression i.e. a treasury of my keys and secrets. It acts as central storage for all sensitive information that can be stored secretly via encryption and can be retrieved/used based on permissions.
To elaborate further, the Microsoft Azure Key Vault service focuses on the security of the below subjects:
- Secret Management The Azure Key Vault service can be used to securely store and control access of secrets, such as authentication keys, storage account keys, passwords, tokens, API keys, .pfx files, and other secrets.
- Key Management The Azure Key Vault service can be used to manage the encryption keys for data encryption.
- Certificate Management The Azure Key Vault service enables you to provision, manage, and deploy SSL/TLS certificates seamlessly for use with Azure integrated services.
Security being the primary driving force of Azure Key Vault’s existence, Microsoft offers the following tiers based on key protection:
- Standard Tier Uses Software vaults for storing and managing cryptographic keys, secrets, certificates and storage account keys. This is compliant with FIPS 140-2 level 2 (vaults).
- Premium Tier Uses a Managed HSM Pool for storing and managing HSM-backed cryptographic keys. This is compliant with FIPS 140-2 level 3 (managed HSM pools).
Terminology used in Azure Key Vault:
Secret
A Secret is a small data blob (up to 10 KB in size) used in the authorization of users/applications with the help of a Key Vault. In a nutshell, Key Vault helps in mitigating the risk associated with the storage of secrets in a non-secure location.
Keys
Keys are also used in the authorization of users/applications to perform any operation while invoking the cryptographic functions of the Key Vault. Unlike secrets, Keys doesn’t leave the secure boundaries of the Key Vault.
Key Vault Owner
An administrator who creates the Key Vault and authorizes the users/applications for various authentication specific operations.
Key Owner/Secret Owner/Vault Consumer
An administrator who owns the Key/Secret for the specific user/application and is responsible for Key/Secret creation in the Key Vault.Kindly note that Key Vault owner and Key/Secret owner roles might be handled by the same administrator, but it’s not necessary.
Service Principal
Identity created (user group/application) for use with applications to access Azure resources.
Application Owner
An administrator who handles the application configuration, including authentication against the Azure Active Directory in the form of URI using Key Vault.
Application
An application authenticates itself from the Key Vault with the help of Keys/Secrets.
Access Policy
Statements that grant access to service principal permissions to perform various operations on keys/secrets in Key Vault.
Ways to access Keys and Secrets in a Key Vault:
- To access the keys/secrets, users/applications must have the valid Azure Active Directory token representing the Security Principal with the appropriate permissions of the target Key Vault.
- Users/applications can use REST-based APIs or Windows PowerShell to retrieve secrets and Keys (public keys only) from the Key Vault.
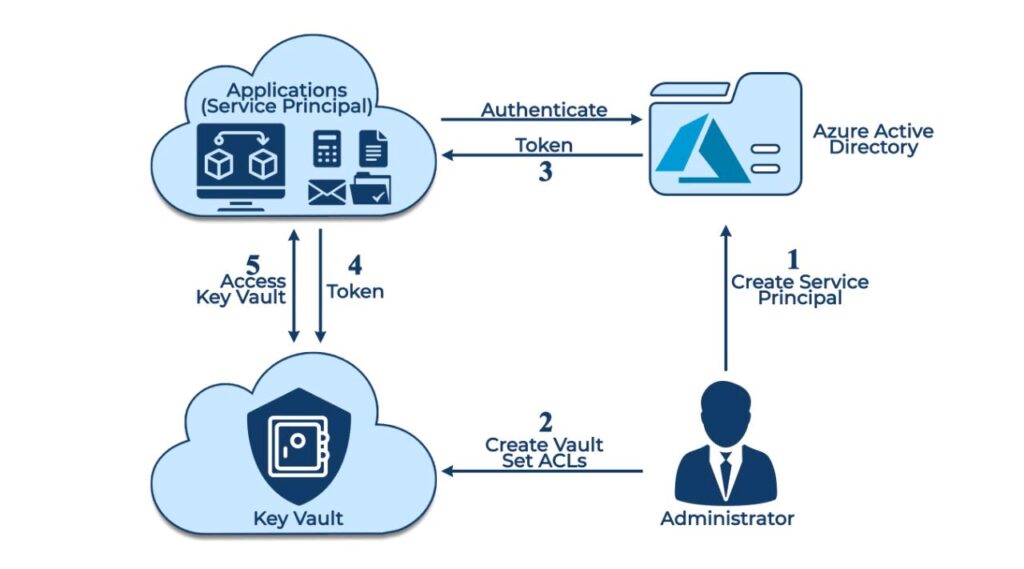
Steps to authenticate an application with the Key Vault:
- The application which needs authentication is registered with Azure Active Directory as a Service Principal.
- The key Vault Owner/Administrator will then create a Key Vault and then attaches the ACLs (Access Control Lists) to the Vault so that the Application can access it.
- The application initiates the connection and authenticates itself against the Azure Active Directory to get the token successfully.
- The application then presents this token to the Key Vault to get access.
- The Vault validates the token and grants access to the application based on successful token verification.
At last, let’s discuss some of the benefits of using Azure Key Vault.
Benefits of using Azure Key Vault:
- As the keys saved in vault will be served via URIs, this avoids the risk of accidental exposure and storage of keys in non-secure locations.
- By design, even the vendor (Microsoft) can’t extract or see customer keys, hence, its fully protected at the vendor level too.
- If your organization needs security compliance while requiring the Key Vault, Azure Key Vault is a good option, as the Key Vault service is FIPS 140-2 Level 2 (Vault) / FIPS 140-2 Level 3 (Managed HSM Pools) compliant.
- Key usage details are logged, so the log data can be used for audit purpose in case of any key compromise situation.
Conclusion
Azure Key Vault streamlines the secret, key, and certificate management process and enables you to maintain strict control over secrets/keys that access and encrypt your data. This expedites the overall project delivery by having developers create keys quickly for development and testing, and then seamlessly migrate them to production keys.