Pretty Good Privacy or PGP is a cryptographic method for communicating privately over the Internet. It encrypts data and provides cryptographic privacy and authentication for online communication. It is frequently used to encrypt documents, emails, and files to improve email security. Data compression, hashing, and public-key cryptography are all used in PGP encryption. PGP also verifies the sender’s identity and ensures that the message was not tampered with while in transit.
It also encrypts data being exchanged across networks using symmetric and asymmetric keys. It combines both private and public-key cryptography features. It uses a different encryption algorithm at every step, and a username and email are associated with each public key.
Working of PGP Encryption
PGP is a type of hybrid cryptography. PGP combines the best features of both symmetric and public-key cryptography in one bundle. When a user encrypts plaintext with PGP, the plaintext is compressed first. Data compression reduces transmission time and disc space use while also improving cryptographic security. Most cryptanalysis techniques use patterns present in plaintext to exploit the cipher. Compression increases cryptanalysis resistance by reducing the patterns in plaintext (Files with very small sizes are not compressed).
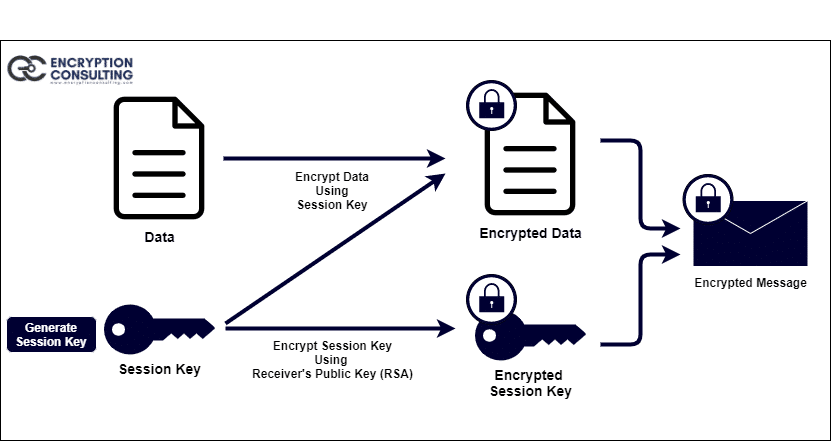
PGP generates a session key, which is a secret key and is generated only once. This key generates a random number from the movement of your cursor and the keystrokes you type. This session key is used to encrypt the plaintext with a very secure and fast symmetric encryption algorithm, and the output is ciphertext. The session key is then encrypted with the recipient’s public key after the data has been encrypted.
The decryption of encrypted data works in reverse. The temporary session key can be recovered using the recipient’s private key, which is then used to decrypt the ciphertext encrypted with symmetric cryptography.
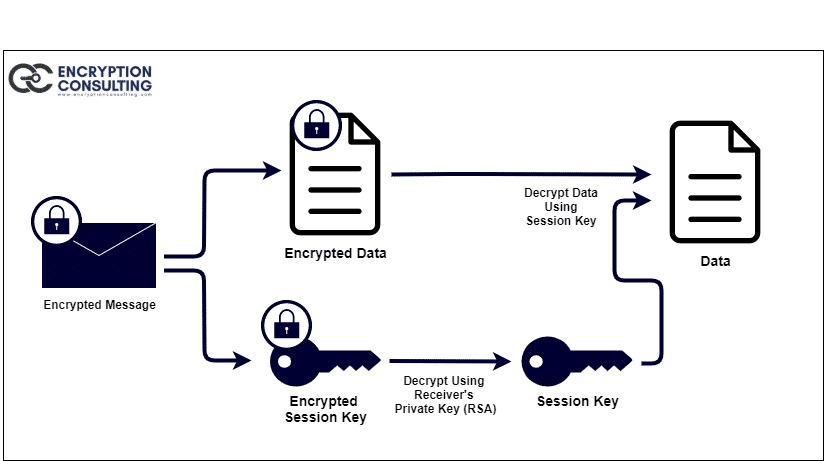
The two encryption methods are combined to give you the convenience of public-key encryption with the speed of symmetric encryption. Public key encryption is much faster than conventional encryption. In turn, public-key encryption solves key distribution and data transfer issues. When both are used in combination, performance and key distribution improve without compromising security.
Use Cases of PGP Encryption
The major uses of PGP encryption are:
- To encrypt data.
- To send and receive encrypted emails.
- To verify the sender’s identity.
Encrypt Data: PGP can be used to encrypt files. PGP offers a highly secure solution of encrypting data at rest, especially when combined with a Threat Detection and Response Solution. The algorithm used by PGP – typically the RSA algorithm – is nearly unbreakable. This technique is so safe as it has been employed in high-profile malware like the CryptoLocker virus.
Encrypt Emails: PGP is mainly used to send encrypted emails. Activists, journalists, and others who deal with sensitive data were the primary users of PGP in its early years. PGP’s popularity has grown at a rapid pace. As more individuals become aware of how much data corporations and governments collect, many people are now using the standard to keep their personal information private.
Identity Verification: PGP can also be used for email verification. For example, if a person is doubtful about the identity of someone sending them a message, they can use a Digital Signature in combination with PGP to authenticate it.
Digital signatures work by combining the sender’s public key with the data they send via an algorithm. A hash function is generated using another algorithm that converts a message to a fixed-size data block which is then encrypted with the sender’s private key.
The data is then decrypted by the recipient using the sender’s public key. The recipient will be informed if even one character of the message has been altered in transit.
Pros of PGP Encryption
Benefits of using PGP encryption are:
- It is extremely secure and nearly unbreakable.
- It improves cloud security.
- Easy to learn and use.
Cons of PGP Encryption
Some limitations of PGP Encryption are:
- There is no recovery process if passwords are forgotten or deleted.
- The information will either not be decrypted or decoded by only one party unless both the sender and the receiver have compatible versions of PGP software.
How to Create PGP Key Pair
Prerequisite: In this article, we discuss how PGP key pair can be generated using GnuPG. You can download GnuPG from the given link: https://gpg4win.org/get-gpg4win.html
Follow the steps below to generate PGP key pair:
- Open the Command Prompt (cmd) as Administrator.
-
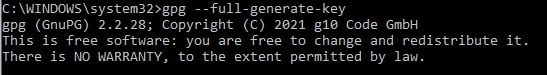
Execute the command below to create a key pair:
$ gpg -full-generate-key
-
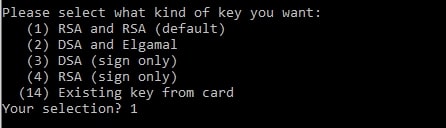
Now, It prompts with the below configurations based on the information provided by the requestor:
-
Select key type that you want to create: We have selected RSA and RSA (default).
-
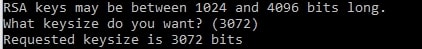
Now, it prompts for the size of the key between 1024 and 4096. 3072 is the default key length. You can hit enter to select 3072.
-
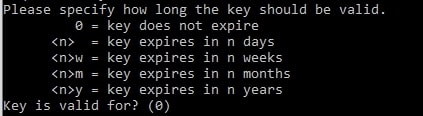
Now, it will prompt for the validity of the key. Zero (0) is the default. You can hit enter to select 0.
-
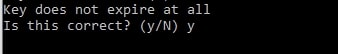
It will prompt you to confirm that the key does not expire at all.
-
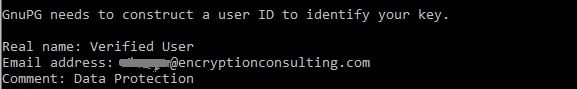
Now, enter the Real name, Email address, and Comment. Real name can be the name of a person, product, or company. You can leave the comment blank.
-
Validate the Name, Email, and comment.
Type O for Okay.
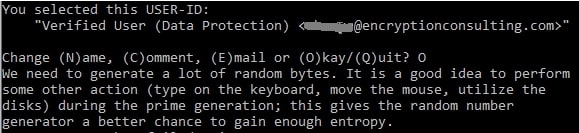
- Now, a prompt will open for the passphrase, enter the passphrase, and hit enter.
-
Copy the Public Key ID from the output.
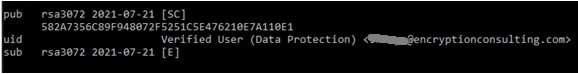
-
-
Export the Public and Private Keys:
-
To export the Public Key, enter the command below:
$ gpg -export -a keyid > publickeyname.key
-
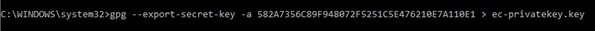
To export the Private Key, enter the command below:
$ gpg -export-secret-key -a keyid > privatekeyname.key

-
It will prompt for the password that you enter in Step 3.g.
Enter the passphrase and hit enter.
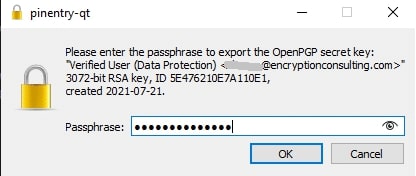
Note: Both Public and Private keys will be saved in the directory where the export commands are executed.




