What is PCI DSS?
The Payment Card Industry Data Security Standard, known as PCI DSS, is a set of guidelines that describes how to keep both you and your clients safe when accepting payments. Given that this is an industry-wide obligation, every provider that processes payments on your behalf will expect you to treat the PCI DSS seriously. The PCI Security Standards Council (PCI SSC) is an independent organization that is in charge of maintaining the PCI DSS, which aims to increase the security of payment card transactions and decrease credit card fraud.
Service providers and merchants are the two types of organizations that must file PCI reports. The requirements for PCI DSS compliance differ based on how many card payments a merchant handles annually. Higher payment volumes necessitate stricter regulations since they are associated with an increased risk of security problems. These thresholds are often set by the acquiring bank of a service provider or merchant. The card brands determine the transaction volumes, which vary slightly among them.
PCI DSS 4.0
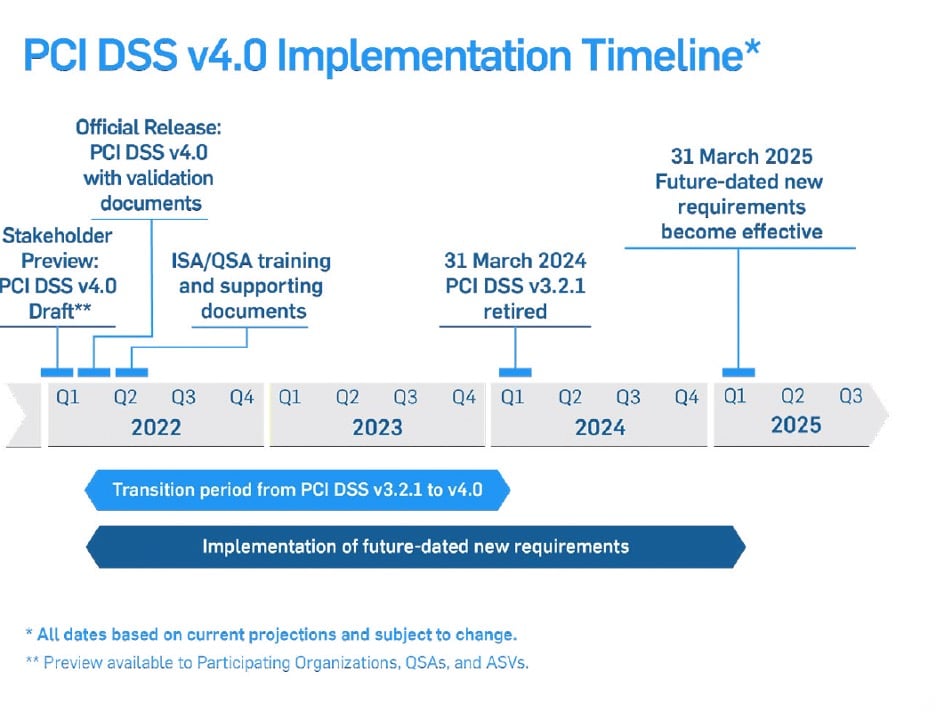
The PCI SSC recently released version 4.0 of the PCI DSS. Since the PCI DSS was first released eighteen years ago, this most recent edition represents the most substantial change. The work necessary to comply with PCI DSS 4.0 shouldn’t be overlooked since it involves modifications, such as requiring authenticated vulnerability scans, requiring multifactor authentication for all access to card data environments (CDE), and requiring more regular scope validation for particular sectors. Even though March 31, 2024, the day when PCI DSS will be implemented, may seem far off, corporate executives, IT security professionals, and compliance officials must start preparing today.
It’s essential to assess your compliance status, identify any obstacles to upholding compliance, and inform staff members—particularly those seated at the boardroom table—of the PCI-DSS 4.0 revisions. The main shift is that PCI DSS 4.0 now prioritizes security more heavily, encouraging flexible data practices that are incorporated into an organization’s overall security posture. The updated standard adds additional flexibility to compliance through its customized approach, acknowledging that new technologies don’t necessarily fit into a strict, prescriptive control structure.
Requirements
Significant changes in PCI DSS 4.0 include:
-
Stronger authentication measures
Merchants need to adopt stronger authentication requirements as the payments sector rapidly transitions to cloud platforms. The most recent version of PCI DSS is now more closely connected with the National Institute of Standards and Technology (NIST) strategy to utilize digital identity verification and life cycle management, enhancing a merchant’s defence against emerging risks. Identity and Access Management (IAM) is the main emphasis of Version 4.0, and it is recognised as being essential to thwarting emerging risks to cardholder data.
-
Scope Validation and Data Discovery
Mandating that service providers identify all sites where cardholder data is stored, reissue their scope every six months, and assign organisations to carry out quarterly data discovery operations.
-
Additional Customized approach
Version upgrade provides a customised approach to PCI DSS implementation and validation, which is one of the biggest modifications. The security results associated with every requirement will be explicitly defined by the new, tailored validation technique. Following that, organisations will have the option of implementing the control according to specifications or in a customised manner.
- A new sub-requirement confirms that all merchants must document, track, and inventory all SSL and TLS certificates in use across public domains in order to strengthen their validity.
- Organizations are no longer allowed to manually review their logs. The process is deemed too time-consuming and prone to error. Merchants must therefore implement automated review tools.
- Organizations must have a web application firewall in place for any web applications exposed to the Internet.
Where You Need to Focus
To shift to PCI DSS 4.0, there are a few things you need to focus on
- Make sure you adhere to PCI DSS 3.2.1. If you haven’t complied yet, identify the obstacles preventing you from complying. A common cause of noncompliance is ignorance about the location of all your cardholder data. Frequent data discovery checks the locations of your card data’s storage and its network path.
- Try your best to adhere to the specified strategy when you transition to PCI DSS 4.0. The customized approach does not remove the need to adhere to controls; rather, it provides flexibility in their satisfaction.
- Reading one article won’t give you all the required knowledge on the new standard since it’s complicated. Get assistance from an expert to navigate PCI DSS 4.0 and hold frequent staff training sessions.
- The number of Chief Data Officers (CDOs) in the workforce has significantly increased, particularly in major businesses. This is hardly surprising, given CDOs frequently have extensive knowledge of numerous compliance requirements. Assign a CDO or provide authority to internal data specialists.
- Larger businesses usually use a variety of security solutions, many of which are unused, incorrectly configured, and useless. Knowing how to make the most of the features of already available products will help you avoid making needless investments in order to implement PCI DSS 4.0.
Conclusion
Stringent requirements for using TLS/SSL protocols to secure credit card data are outlined in PCI DSS 4.0. Respecting these guidelines is essential for both preserving compliance and safeguarding private client data.
Organizations may make sure that their TLS/SSL environments satisfy the high requirements established by PCI DSS 4.0 by concentrating on moving away from insecure protocols, putting strong cryptographic controls in place, and maintaining a strong security posture. Payment card data protection is critical in today’s cybersecurity environment. A vital first step in reaching PCI DSS 4.0 compliance and protecting sensitive client data is comprehending and putting these TLS/SSL security priority areas into practice.
To secure these machine identities throughout your infrastructure, CertSecure Manager can assist in locating all of your TLS certificates supporting private keys. Automating the renewal of expired certificates can help you prevent disruptions and react fast to problems, vulnerabilities, and CA compromise. Please visit our website encryptionconsulting.com for more information. You can also reach out to us for a demo or poc.