Whether you’re running a small business website, a complex enterprise application, or a cloud-based service, your users expect seamless, uninterrupted access. This is where load balancers come into play, and among the most trusted names in this domain is F5 Networks.
But manual certificate management on an F5 device can be pretty hectic, considering the lifespans of SSL/TLS certificates were a couple of years long, until recently. The SSL/TLS certificate life is getting shorter and shorter. With the CA/Browser Forum mandating certificate lifecycles of just 47 days, organizations must adapt to this dramatically accelerated renewal cycle to maintain continuous security and compliance. The burden of this drastic change on manual management is substantial. Consider the amount of effort an IT team would have to put into managing hundreds of certificates that are quickly coming up for expiration. Missed renewals run the ongoing risk of causing additional disruptions.
Automating Certificate Management for F5
To fully automate certificate issuance and deployment for BIG-IP F5, you need to deploy the F5 Renewal Agent, which can be downloaded from the CertSecure Manager frontend. The agent must be installed on a Windows machine (Server 2019 / Windows 11 or later) with port 22 enabled. Follow the installation steps mentioned in the readme file that comes bundled with the downloadable zip. Once the agent is configured, you can manage it from the Windows Services console.
Once the renewal agent is configured and running, visit the CertSecure Manager frontend and follow the mentioned steps to renew a certificate.
- Log in to CertSecure Manager, and go to “Utilities” and then “Agents”. Here, you can confirm the status of the F5 Renewal Agent, then right-click and click on the “Update Cert” button.
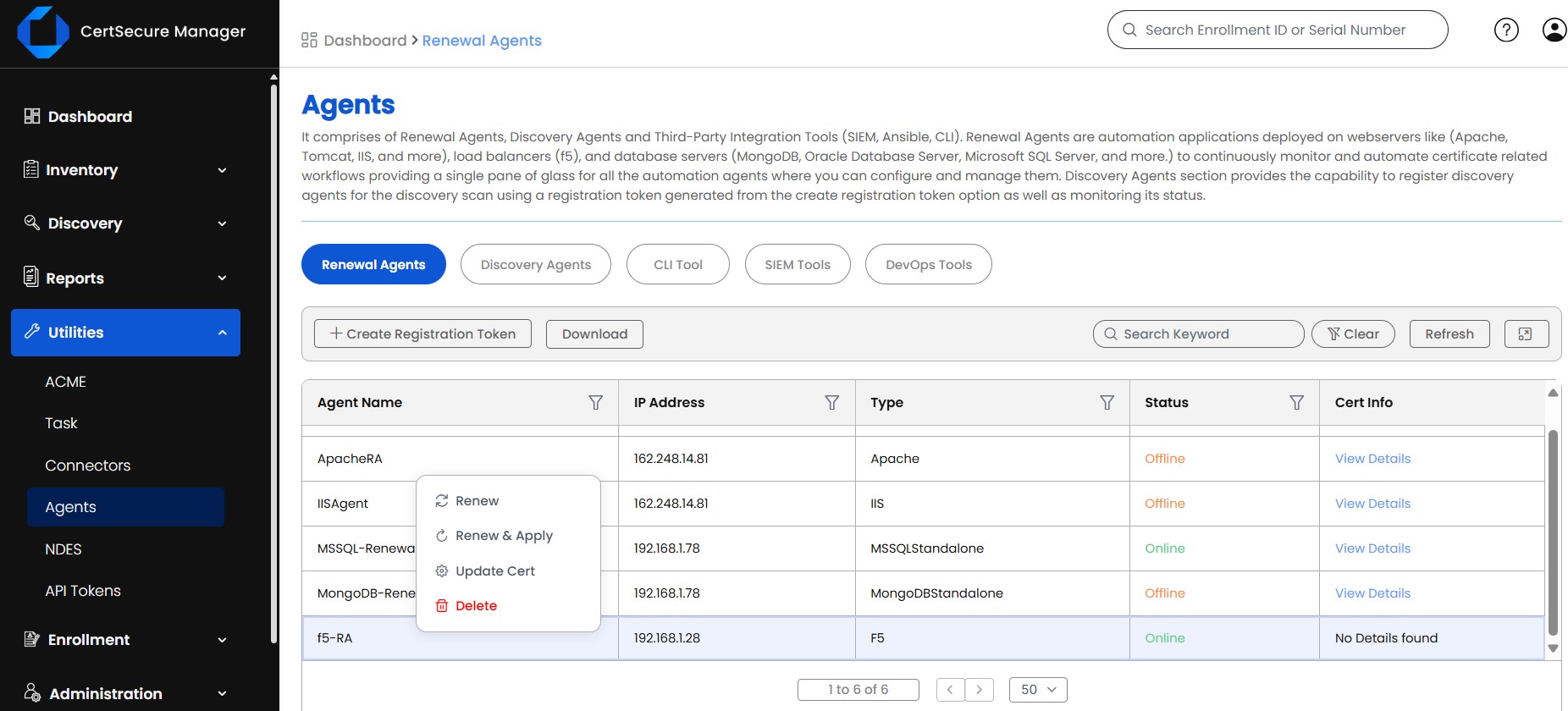
-
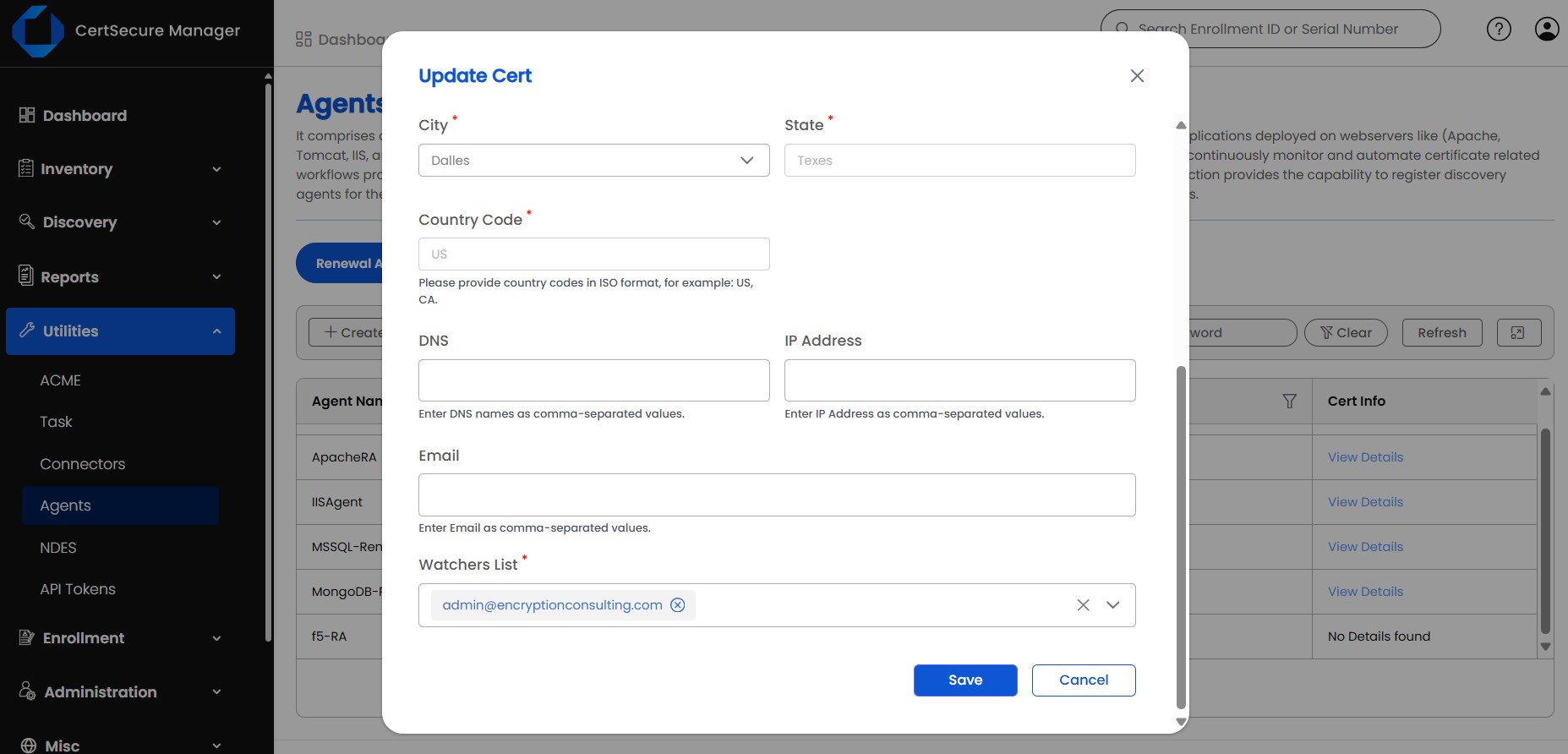
Choose the certificate authority, the certificate template, and mention all other required information. Click on “Save” to save the information.
- Now, right-click again and click on the “Renew and Apply” button, and further confirm it to trigger the renewal. You can also click on “Renew” to just push the certificate to the common partition if you don’t want to bind the certificate to any SSL profile currently.
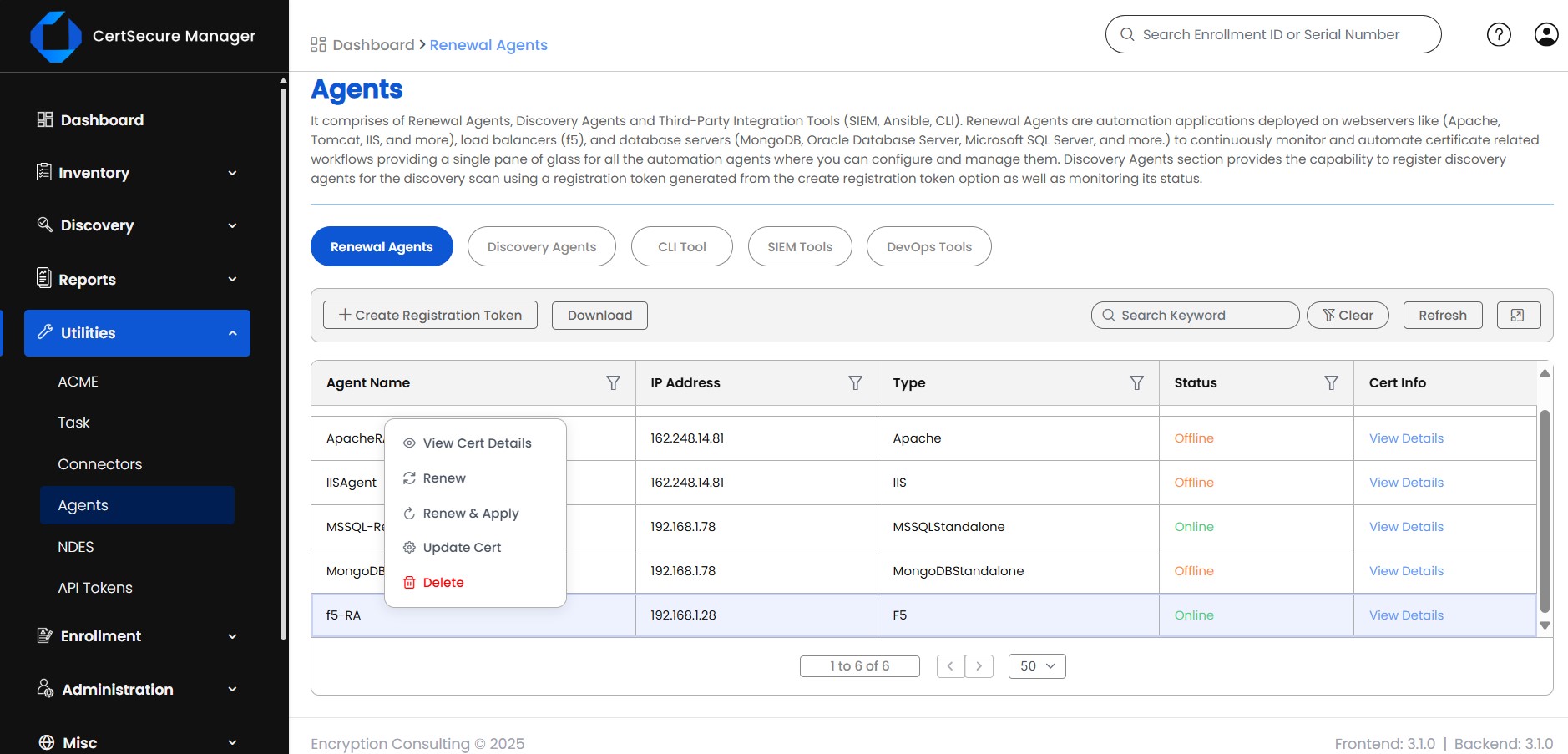
-
Go to “Utilities” and then “Tasks” to monitor the renewal process.
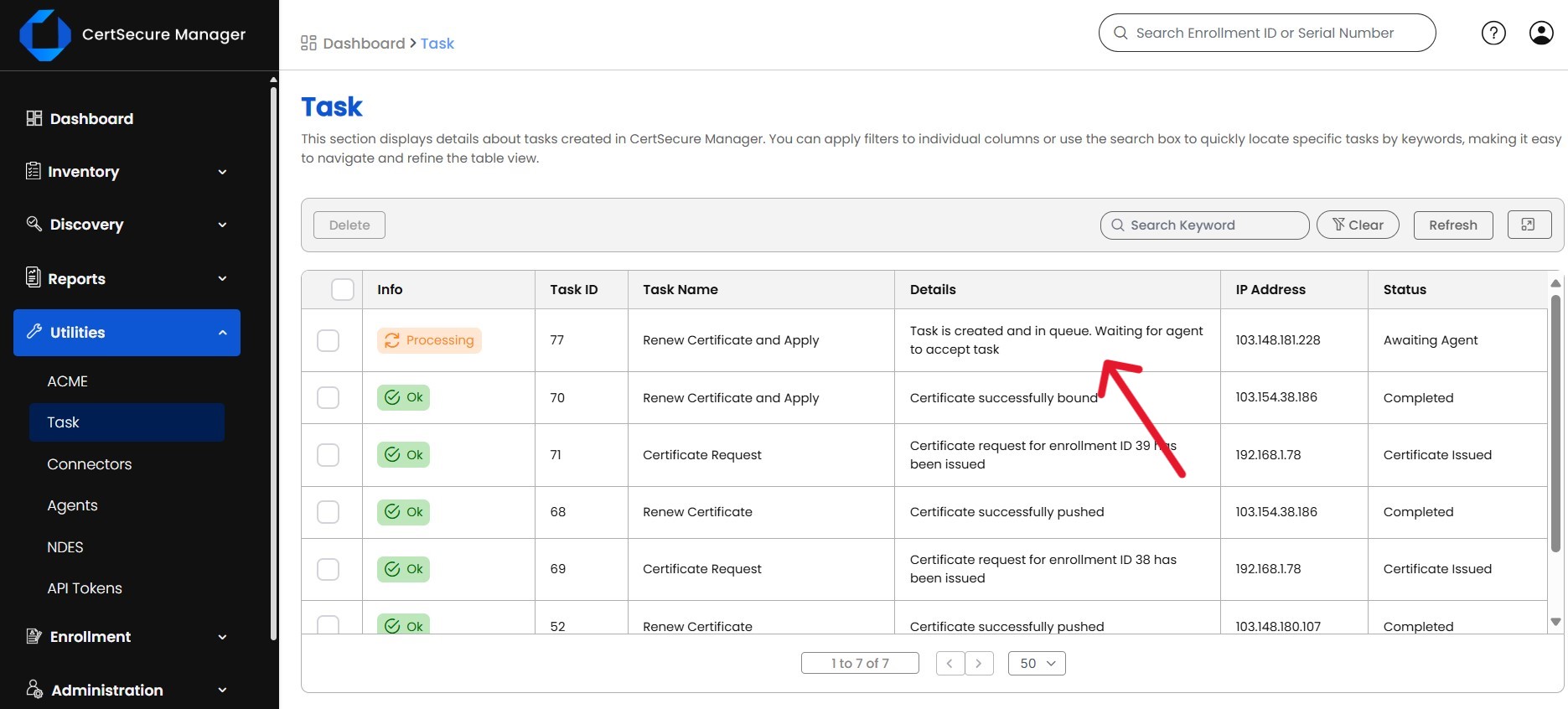
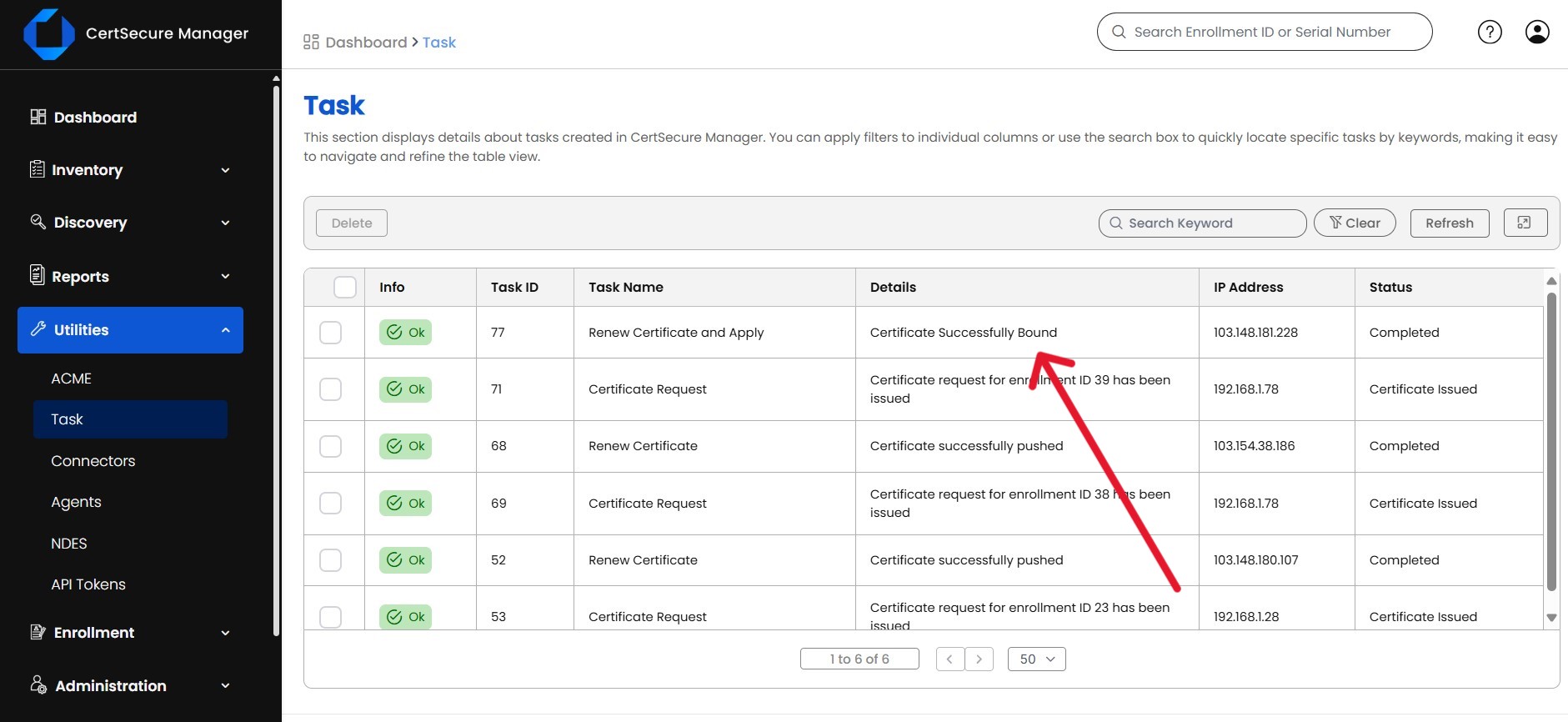
-
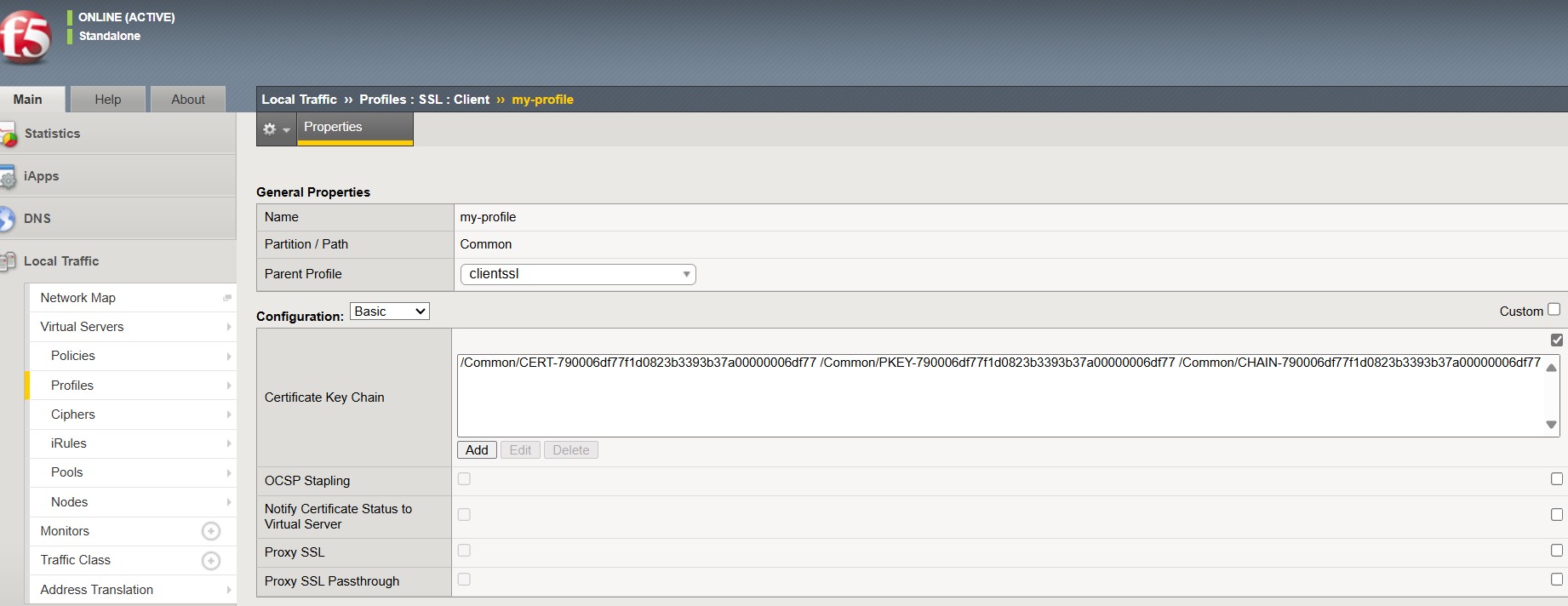
Once renewal has succeeded, visit the BIG-IP F5 web interface to validate that the certificate is successfully bound. In case of any failures, you can check the renewal agent log file located in “C:\CertSecure\logs\EC_F5_RenewalAgent.log” by default.
How Can Encryption Consulting Help?
Encryption Consulting extends the power of CertSecure Manager by offering automated certificate renewal not just for F5, but also for NGINX, Apache, and IIS environments. This reduces manual effort, eliminates configuration errors, and ensures secure certificate deployment across your infrastructure. With the CA/Browser Forum mandating certificate lifecycles of just 47 days, automation is no longer optional; it’s essential for maintaining continuous operations. CertSecure Manager’s renewal agents help you stay compliant and avoid downtime caused by expired certificates in this dramatically shortened renewal cycle.
Beyond automation, Encryption Consulting provides PKI-as-a-Service (PKIaaS) and expert PKI consulting to build, manage, and optimize secure, scalable PKI environments tailored to your needs: on-prem, hybrid, or cloud.
Conclusion
With certificate lifespans shrinking and the renewal cycle becoming increasingly demanding, manual certificate management on F5 devices is no longer sustainable. Deploying the F5 Renewal Agent through CertSecure Manager enables full automation of the issuance, renewal, and deployment process, significantly reducing the risk of human error and service disruption. By taking advantage of this agent-based automation, your organization can stay ahead of compliance requirements, improve operational efficiency, and ensure uninterrupted, secure access to your services.