- Why is Traditional Single-Factor Authentication Falling Short?
- Why is Multi-Factor Authentication (MFA) Essential?
- How to Integrate a centralized MFA to Organization Access?
- Is just a Centralized MFA integration enough?
- How to improve the MFA’s strengths and management?
- Creating a Multi-Layered Authentication Framework
- Balancing Security and User Experience to avoid the MFA Fatigue
- Conclusion
Data breaches are happening more frequently than ever before, making organizations’ security defenses weaker and requiring continuous updates in their strategic planning and security measures to keep the constantly advancing threats at bay. In just 2023, there were an estimated 2,814 incidents of data breaches, according to IT Governance. A study by the Harvard Business Review shows that these incidents of data breaches increased by 20% from 2022 to 2023.
Several vulnerabilities in the contemporary authentication infrastructure have resulted in a large number of cases of exploits. The several instances pointed out were the Cloud Misconfiguration, like improperly secured S3 buckets exposing sensitive data, evolved ransomware attacks like Ryuk ransomware attacks targeting healthcare institutions, and increased exploitation of vendor systems such as SolarWinds supply chain attacks compromising widely used software.
In most cases, the reasons behind these malicious actions involved an absence of a strong authentication layer, which resulted in vulnerabilities that were easy to exploit. The lack of proper monitoring only makes the situation worse by causing the organizations’ security defenses to become weaker leading to compromised systems staying undetected for far too long. These incidents highlight the critical need for a strong and secure authentication process that can protect organizations from even the most sophisticated attacks.
Why is Traditional Single-Factor Authentication Falling Short?
As we know, the traditional authentication system uses single-factor username and password matching. This was reliable for a very long time, but with the rapid advancement of technologies, there has been an unprecedented need for organizations to do more to protect their data. In recent decades, we have seen significant breakthroughs in computational power and technologies, including artificial intelligence (AI) and high-performance computational units such as GPUs, DPUs, and more.
These advancements have made single-factor systems increasingly vulnerable to various exploit strategies, including GPU-accelerated Brute-force attacks, credential stuffing by AI-powered bots, and social engineering or phishing attacks. This leads to an increased likelihood of attackers succeeding in cracking a password, giving them complete access to all accounts for which the user has reused the credentials. And the recent news highlights the dangers that organizations are facing:
- In June 2024, cloud vendor Snowflake reported a cyber threat targeting customers who relied on single-factor authentication. While the exact details are still emerging, it is clear that organizations need stronger authentication measures to prevent compromise.
- CISA (Cybersecurity and Infrastructure Security Agency) in the US added single-factor authentication to its list of “Bad Practices” in August 2021. It clearly highlights the growing consensus among security experts that single-factor authentication is no longer sufficient for online security.
Why is Multi-Factor Authentication (MFA) Essential?
Multi-factor authentication (MFA) serves as a security measure that emphasizes user identity verification through more than one authentication method. These extra methods include a fingerprint or a one-time code sent to the user’s phone to log in to an account or system. The idea fundamentally focuses on identifying the user from multiple authenticated sources before giving them access to the resource they are trying to log into.
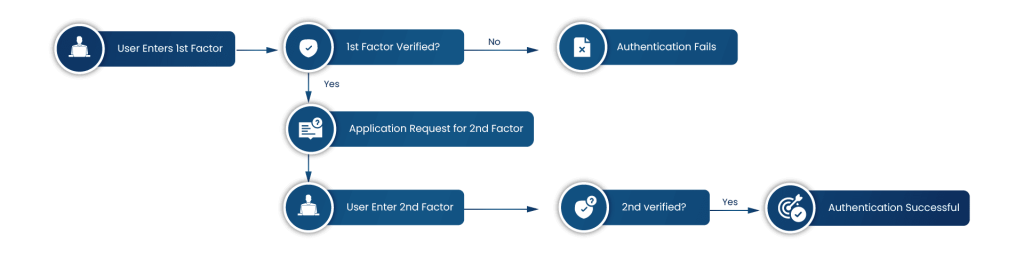
In a simple single-factor authentication, there is only a single criterion for authentication, but MFA adds multiple layers of security to the authentication, making it an ideal choice for organizations. However, the important question is how organizations can secure their resources with MFA. To answer this, we can take the example of these situations:
-
We all know of scenarios in our organizations where sometimes employees leave on less-than-amicable terms. With a single password authentication system, a discontented ex-employee could potentially wreak havoc on the organization’s systems if they still possess the login credentials.
MFA throws up a roadblock to this issue, requiring an extra verification step (like a machine identity or geo-location matching). Now, even if the credentials are leaked, they still won’t have access to the company’s sensitive data.
-
Another scenario involves, if a corporate system or device is compromised, the company’s sensitive files, services, and resources are exposed to outside threats. A simple authentication method will fail in cases where the password is saved. But, for an MFA-enabled system, logging into the resources would need more than just one authentication, making it a lot more difficult to gain access to the compromised system.
There are several reasons why we consider MFA as the most powerful solution that organizations currently require to prevent attackers from gaining unauthorized access to the systems, even if the credentials are forged. So, what are the considerations to integrate a centralized MFA into an organization’s Access Management? Let’s find out next.
How to Integrate a centralized MFA to Organization Access?
Well, it can be a challenging task to identify the correct MFA design and criteria. If we have a proper understanding of requirements and planning, integration of MFA with organizational access management becomes easy. We will be discovering the key steps and strategies that you need to follow for the seamless integration of MFA:
Step 1: Understanding Your Security Posture
Firstly, it is important to know what you are working with and that starts with evaluating your current systems. Here we are looking for potential vulnerabilities in existing login protocols and overall security posture. This assessment will help you to identify areas where stronger authentication measures like MFA can be most beneficial.
Step 2: Choosing the Right MFA Method
There are various MFA methods available, each with its advantages and considerations.
- Two-Factor Authentication (2FA): The system requires the user to enter their password and one additional form of identification, such as a verification code sent to their phone or email.
- Third-Party Authenticator App: Instead of the system itself, a third-party application (authenticator app) verifies the user’s identity by generating a passcode that the user has to enter to confirm the identity of the system.
- Biometric Authentication: Biometric Information, such as scanning a fingerprint, retina, or other unique physiological features, serves as the system’s authentication.
- Device Recognition: The system prompts for multiple authentications only when accessing it for the first time on a new device. Subsequent access from recognized devices requires only the user’s password, as the system remembers the device’s identity.
We recommend that you consider several parameters while opting for an MFA option, including ease of use, security strength, and compatibility with the existing organization’s infrastructure. Based on the identified security requirements, multiple MFA options can also be a good decision.
Step 3: Identity Management System Integration
After the MFA solution option is selected, it needs to be integrated with the existing identity management system (e.g., Active Directory, Azure AD). It is better to have centralized user management from a single point of control. It enables consistent enforcement of MFA policies across the organization.
Step 4: Testing and Refinement
Additionally, it should also be necessary to conduct thorough testing of the MFA implementation to identify and address any potential issues with the deployment.
Is just a Centralized MFA integration enough?
Unquestionably, a centralized multi-factor authentication system offers robust security for the organization’s priceless assets. It simplifies the user management procedure and has many benefits while implementing uniform security guidelines across the entire company. However, a number of restrictions need extra security precautions into account:
-
Conditions for Static Authentication
Typically, pre-established authentication factors like one-time passcodes sent by SMS or authenticator apps are used by Centralized MFA solutions. Although these techniques are a big improvement over using passwords alone, they are not flexible enough to counteract advanced security threats.
A stronger MFA element, like a hardware token or biometric verification, is necessary for a higher-risk login attempt, such as one made from an unusual place, time, or device, while low-risk logins, such as a regular user coming in from their typical office network, don’t.
-
Limited Access Control Granularity
We recommend against using a one-size-fits-all MFA policy that applies to all organization units, as this ignores the differences in access requirements between departments or user roles. We can use privileged users who manage extremely sensitive data, such as bank records or intellectual property, as an example.
When it comes to regular internal programs like email or collaboration tools, they ought to demand more stringent authentication procedures than those associated with basic user logins.
-
Human Element Vulnerability
Although multi-factor authentication (MFA) methods are supposed to provide robust security, users who are not sufficiently taught in security best practices may fall prey to social engineering and phishing schemes. Users may fall victim to a deceptive email that poses as a reliable source (such as a manager or IT help) and deceive them into disclosing their MFA credentials or clicking on a malicious link that compromises their machine.
These restrictions allow room for development even though they do not directly present a serious security hazard. We will examine ways to close these holes and improve our company’s security posture in the following part.
How to improve the MFA’s strengths and management?
We’ve already talked about the drawbacks of MFA-enforced security solutions. We will investigate many cutting-edge approaches that go beyond static criteria and offer a granular and risk-based strategy to address such difficulties. Let’s examine these tactics and the situations in which they are applied:
-
Adaptive Authentication
Using contextual data that is updated in real time, an adaptive authentication system dynamically modifies the MFA requirements.
-
Risk-Based Authentication
This technique assesses the possible danger involved in every attempt to log in.
-
Biometric Authentication
A strong layer of security is provided by biometric authentication techniques, such as fingerprint, iris scan, or facial recognition, especially for privileged user accounts or access to extremely sensitive data. Each person possesses these distinct biometric characteristics, which greatly lessen the likelihood of password theft or token abuse.
By using facial recognition software or fingerprint scanners for biometric authentication, the dangers associated with popular attacks like credential stuffing and password spraying are reduced. Numerous businesses, like as Suprema and HID Global, offer biometric solutions to businesses.
Regulating biometric authentication varies by region, and it’s crucial to recognize that biometric data collection and storage present privacy concerns. It is advisable that you thoroughly evaluate the ethical and legal ramifications prior to implementing biometric authentication systems.
-
Security Awareness Training
An effective security awareness program can have a long-term positive impact on the firm by teaching staff members about cybersecurity best practices. It is advisable for firms to conduct employee training and awareness campaigns regarding the best practices and functionalities of secure MFA login procedures.
-
Geo-fencing
A user’s usual geo-location, such as their home or office, is tracked by the system. Attempts to log in from outside this zone use more robust MFA, such as a hardware token or fingerprint scan, than logins from known locations made during regular business hours. For this, you can use tools like Azure Active Directory Geofencing with Azure Maps or Google Maps Platform.
-
Device Recognition
Attempts to log in from known devices, such as a business laptop or a personal phone, are recognized and trusted by the system. Additional verification steps are necessary for logins from unidentified devices, such as a public computer or a new phone. Device management and identification are aided by mobile device management (MDM) programs such as VMware Workspace ONE and Microsoft Intune.
-
Time-based Factors
Repeated attempts to log in by a single person in a short amount of time, particularly unsuccessful attempts, point to suspicious activity and need to prompt more robust multi-factor authentication.
-
Historical Behavior
Repeated attempts to log in by a single person in a short amount of time, particularly unsuccessful attempts, point to suspicious activity and need to prompt more robust multi-factor authentication.
-
Monitoring
An ongoing method for monitoring the MFA system needs to be implemented. This will help expose usage and examine login attempts for unusual activity. The information obtained by this approach will help generate reports identifying possible security breaches and areas for improvement.
-
Threat Intelligence Feeds
Real-time information on new threats and attack vectors is available through services like Palo Alto Networks Threat Intelligence and Cisco Talos. In order to dynamically modify authentication requirements based on the most recent threats, this data can be connected with MFA regulations.
-
Anomaly Detection
Login attempts originating from suspicious locations, known malware sources, or involving unusual access times are flagged as high-risk and trigger additional MFA steps. Security Information and Event Management (SIEM) systems, like Splunk, Palo Alto Cortex, or Elastic SIEM, can analyze security logs from various sources (firewalls, endpoints, MFA systems) to identify unusual patterns.
-
Identify Phishing Attempts
Phishing emails frequently aim to deceive recipients into disclosing login information or clicking on harmful links. Users can spot warning signs such as generic greetings, dubious sender addresses, or misspelled URLs with the aid of appropriate education and awareness.
-
Maintain Strong Password Hygiene
Users can drastically lower the risk of password compromise by creating complex passwords (using a combination of capital and lowercase letters, numbers, and symbols) and not reusing them across platforms. Tools for managing passwords, such as 1Password or LastPass, are beneficial.
-
Avoid Social Engineering Tactics
Social engineering involves manipulating users into giving away sensitive information or taking actions that compromise security. Training can help employees identify these tactics and avoid falling victim to them.
-
Report Suspicious Activity
Procedures for managing anticipated security breaches involving compromised MFA credentials should be clearly outlined in an incident response plan. It is advisable to motivate staff members to swiftly notify the IT security team of any questionable activities, including phishing scams or odd attempts at login.
-
Compliance Management
Organizations should be required to guarantee that the MFA solution they have installed complies with all applicable security legislation and compliance standards, such as PCI DSS and HIPAA.
Creating a Multi-Layered Authentication Framework
Even while legacy MFA provides an essential security layer, not all risks can be addressed by it. Even the more traditional multi-factor authentication (MFA) methods need to be strengthened against more complex cyberattacks. We’re going to learn how to integrate the current centralized MFA system with a multi-layered authentication framework:
-
Integration with Security Information and Event Management (SIEM) systems
Important insights into possible threats and suspicious activities may be gained via a centralized procedure for the logging and analysis of authentication events from many sources (MFA logs, firewall logs, and endpoint security logs).
SIEM systems provide the ability to detect abnormalities, correlate login attempts with other network activity, and send out notifications for any security problems.
-
Endpoint Security Integration
Organizations can improve authentication by integrating multi-factor authentication (MFA) with endpoint security solutions such as Microsoft Defender for Endpoint or CrowdStrike Falcon. This allows for the verification of access attempts based not only on user credentials but also on the security posture of the device. Before providing access, this entails assessing elements, including device health, the availability of security software upgrades, and compliance with corporate security rules.
-
Contextual Authentication Policies
To customize MFA requirements depending on certain factors like user roles, the sensitivity of the data being accessed, or the location from which access is sought, we suggest enterprises create contextual authentication rules. With less user friction in everyday circumstances, our modular approach guarantees that stronger authentication mechanisms are deployed when they are most needed.
-
Continuous Monitoring and Response
In order to identify suspicious activity (such as repeated unsuccessful login attempts from a banned IP address) or abnormalities during the authentication process in real-time, continuous monitoring capabilities must be used. Automatic countermeasures can also be initiated to mitigate any security breaches quickly. These could include tightening authentication requirements or preventing access until more verification is received.
-
Advanced Threat Intelligence Integration
We also recommend taking into account feed services for advanced threat intelligence. Giving real-time information about new risks and attack pathways improves MFA security. Organizations may respond dynamically to sophisticated security risks by adjusting their authentication tactics through the integration of threat intelligence with MFA rules.
-
Regular Security Audits and Penetration Testing
To find weaknesses in the authentication infrastructure, regular security audits and penetration testing must be carried out. By simulating actual cyberattacks, these vulnerability evaluations find flaws and holes and confirm that MFA rules and processes are effective. Organizations may effectively enhance their authentication procedures against more sophisticated and hazardous potential attacks by conducting regular audits.
Balancing Security and User Experience to avoid the MFA Fatigue
We have spoken about how crucial MFA is to obtaining organizational resources. Additionally, we now know the approaches and procedures for putting robust authentication into practice. Prioritizing the authorization process’s user experience to make it simpler for employees to utilize is equally critical as maintaining security standards. Users that experience MFA fatigue due to the excessive steps needed to access the resources they need can be caused by an overly complicated authentication workflow.
MFA fatigue has a negative impact on output and the completion time of tasks that require urgency. Choosing weaker passwords or breaking security procedures are two dangerous behaviors that frequently result from this dissatisfaction. We can think about the following suggestions to avoid such problems in the future:
-
Balancing Security and Usability
We think it’s critical to strike a balance between robust security and an easy-to-use interface. Context-aware authentication, in which the MFA technique adjusts according to risk factors, can be used to do this. Routine login attempts from known devices or networks, for example, require less complex authentication techniques, but suspicious activity necessitates more thorough verification procedures.
-
Usability Testing
To detect and reduce any friction points or complications in the authentication process, we also suggest regular usability testing as a way to help you prevent MFA fatigue. User input is a key component of this approach. By improving workflows, organizations can optimize authentication procedures and improve user experience and security at the same time. By using an iterative process, security protections are maintained without sacrificing usability.
-
Education and Awareness
Users must always be made aware of the dangers of compromising security for convenience, as well as the significance of using strong authentication procedures. It is imperative for organizations to prioritize raising knowledge of the advantages of a centralized multi-factor authentication system, discussing potential risks, and offering unambiguous guidance on navigating authentication procedures.
Conclusion
Centralized MFA is an important security measure, but we recommend that it should not be your only line of defense. Companies need to take a multi-layered approach and acknowledge its limitations. Always keep in mind that maintaining security is a continuous process. We can establish a more robust security environment for our organizations by combining the layered authentication approach with security awareness training and continuous threat monitoring.
Multi-factor authentication implementation and migration may be difficult processes that cannot afford to go wrong. Even the smallest of errors during the execution or implementation phase can open a backdoor for attackers. We at Encryption Consulting LLC, have extensive experience in the implementation of MFA solutions for our clients across the world. Our services go beyond basic password protection.
We have worked with leading Fortune 500 companies to implement and manage MFA solutions, including the deployment of Windows Hello for Business. This uses convenient biometrics like facial recognition or fingerprints as a second factor for user logins.
To further strengthen your MFA environment, we also offer seamless integration of Microsoft PKI with Intune. With extensive experience in the domain, we ensure a successful and secure implementation of MFA into your organization and customize it to the unique requirements of our clients.
- Why is Traditional Single-Factor Authentication Falling Short?
- Why is Multi-Factor Authentication (MFA) Essential?
- How to Integrate a centralized MFA to Organization Access?
- Is just a Centralized MFA integration enough?
- How to improve the MFA’s strengths and management?
- Creating a Multi-Layered Authentication Framework
- Balancing Security and User Experience to avoid the MFA Fatigue
- Conclusion