All you need to know about DevSecOps scaling


Nowadays, DevSecOps is crucial as your organization grows and adopts more complex and cloud-based applications. As you know, DevSecOps integrates development, security, and operations teams, and scaling DevSecOps helps to maintain speed, security, and compliance without slowing down innovation. A well-scaled DevSecOps approach empowers involved teams to detect and address vulnerabilities early, automate security tasks, and adopt a culture of shared responsibility. Here, you’ll explore key strategies to expand your DevSecOps practices, ensuring that security remains robust and agile as your organization scales.
The evolution of DevSecOps is a story of adapting to the growing need for security in software development. Its roots can be traced back to the 1970s. At that time, the focus was on defining software quality. In 1976, a seminal paper outlined attributes of quality, followed by another in 1978 that identified eleven key quality factors. However, security was barely mentioned, as threats like hacking were rare, and the technical world was far less complex.
In the 1990s, as the internet gained prominence, security started becoming a concern. The introduction of the Secure Software Development Lifecycle (SSDLC) by Microsoft in the early 2000s marked a significant step forward. It emphasized integrating security into software development and highlighted the need for proactive measures against emerging cyber threats.
By the 2010s, the rise of Agile and DevOps improved software delivery. However, lagging security can be seen as a bottleneck in fast-paced development cycles. Shannon Lietz, a pioneer in this field and Founder of the DevSecOps Foundation, recognized this gap and championed the integration of security into DevOps workflows. Around this time, organizations started adopting the “shift-left” approach and embedded security earlier in the development lifecycle.
The movement grew as three major technological trends reshaped the industry: the shift from Waterfall to Agile and DevOps, the transition from monolithic systems to microservices, and the migration from traditional data centers to the cloud. These changes demanded a robust approach to ensure security without slowing innovation.
DevOps emerged in 2009 as a concept that fills the gap between development and operations teams and collaborates to deliver high-quality applications rapidly and efficiently. It is often represented as an infinity loop, which represents its continuous and iterative nature. The loop comprises eight stages- Plan, Develop, Build, Test, Release, Deploy, Operate, and Monitor. Each stage flows seamlessly into the next by creating a streamlined pipeline where feedback and improvements are integrated continuously to ensure agility and reliability.
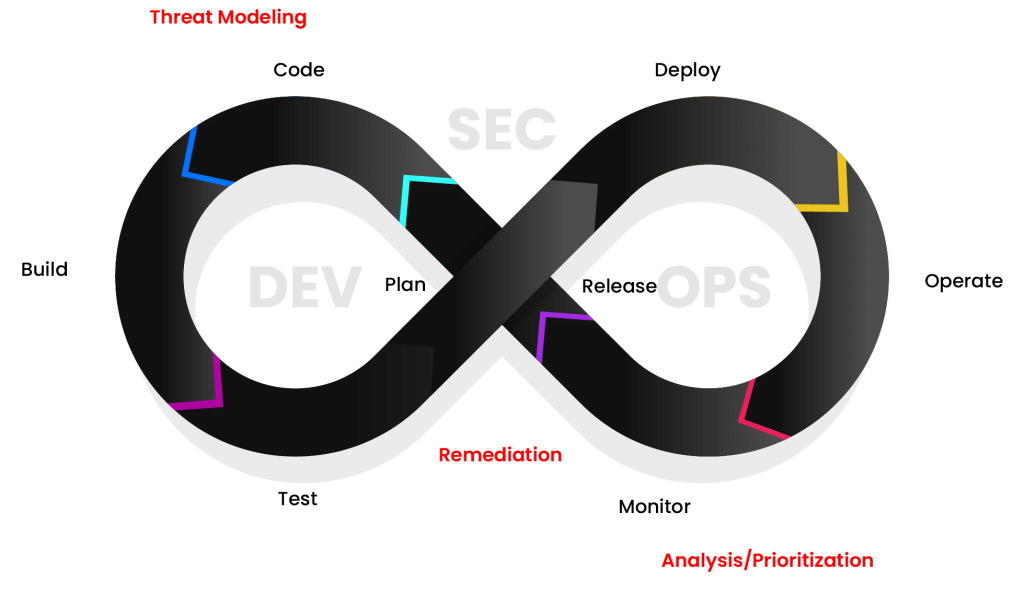
Building on DevOps principles, DevSecOps was introduced to embed security as a foundational element across every stage of the DevOps lifecycle. The term gained direction as security professionals recognized the need to address vulnerabilities early in the development process rather than treating security as a separate final step. DevSecOps ensures robust and secure applications without compromising speed or agility. It is done by integrating automated security tools such as code scanning, vulnerability assessments, and compliance checks into CI/CD pipelines. The idea is to “shift left,” meaning security is prioritized from the earliest stages of design, development, and testing all the way through to deployment and maintenance. Some DevSecOps tools are aqua security, checkmarx, snyk, and sonarQube.
Scaling DevSecOps refers to the process of shrinking and expanding DevSecOps practices across your organization according to the needs. Expanding and shrinking refer to the dynamic adjustment of resources and infrastructure in response to fluctuations in workload, security needs, or project size. Expanding occurs when there is an increase in demand, such as a rise in the volume of software deployments, higher security requirements, or the need for more automated tools and tests. This could involve adding more computing power, storage, or security tools to ensure that the system can handle the growth without compromising performance or security.
Organizations have an increased number of applications, microservices, cloud deployment, and development teams to manage when they evolve, which can be one of the major causes of scaling up DevSecOps. For instance, in a cloud environment, resources like virtual machines or containers can be dynamically allocated to meet the increased demand and ensure that the infrastructure remains efficient and secure.
On the other hand, shrinking takes place when the demand decreases, like after a major release or project is completed. This process involves scaling down resources that are no longer necessary and also reduces expenditure. Shrinking can involve shutting down unused servers or containers, downgrading security services, or reducing the scope of automated tasks. The aim is to maintain efficiency by releasing unneeded resources.
The relationship between expanding and shrinking in DevSecOps is seamless, especially in cloud environments where resources can automatically adjust based on the current needs. This flexibility ensures that DevSecOps remains both cost effective and efficient while providing the necessary resources during peak demand and scaling back when the load subsides. Ultimately, this adaptive approach allows for a balance between performance, security, and cost-efficiency.
Scaling DevSecOps means ensuring that security is consistently integrated into each phase of development across all these elements without compromising speed or efficiency. This approach not only mitigates risks but also aligns with the dynamic needs of modern software while allowing systems to expand automatically under high loads and shrink when resources are no longer needed.
Lots of technical advantages can be derived from scaling DevSecOps. This includes more security integration, faster development rates, and uniform compliance among expanding teams and applications.
While scaling DevSecOps, security measures are added to each stage of the development process, which helps control security risks in the early stages rather than incurring costs due to extensive changes in the later stages. There is the possibility of implementing security processes like static code checks, code push with the help of bots, code signing in the CI/CD pipelines, and other such activities concerning time.
It allows teams to adapt quickly to changing demands and maintain compliance with industry standards such as HIPAA, GDPR, PCI DSS, and ISO 27001. It also handles increased development processes without compromising security.
Fixing security issues early in the development process is significantly less expensive than addressing them post-deployment. Scaling DevSecOps reduces the costs associated with data breaches, downtime, and non-compliance penalties.
Scaling DevSecOps ensures the smart use of resources by adapting to the workload. In simpler terms, scaling DevSecOps ensures that security and performance stay intact as projects grow and allows teams to deliver faster, safer, and more reliable software.
Automating security checks through tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) allows teams to address issues without slowing down development. It enables faster feedback loops and reduces delays caused by traditional security gatekeeping.
A real-world example is Netflix, which successfully scaled its DevSecOps practices to support its global streaming platform. Netflix automated security testing and integrated it into its CI/CD pipelines. They used tools like Lemur for certificate management and in-house solutions to detect vulnerabilities in real time. With respect to security concerns and compliance issues, Netflix was constantly able to push new software version updates even several times a day. This helped them to protect users’ trust and, more importantly, user-related data in their online content streaming business, which challenged the rage of other players.
Twilio’s report says that COVID-19 has significantly sped up digital transformation, with 97% of organizations reporting an increased pace in their digital initiatives. This rapid shift underscores the growing importance of DevOps practices.
Over 80% of organizations are now adopting DevOps, and this figure is projected to reach 94% soon. The global DevOps market is expected to grow from $10.4 billion in 2023 to $25.5 billion by 2028, which shows a compound annual growth rate (CAGR) of 19.7%. Organizations face mounting security challenges as they scale their DevOps practices.
A survey by Contrast Security revealed that
99% of organizations have experienced the average application in production containing at least four vulnerabilities.
79% of organizations report that their DevOps teams are experiencing heightened pressure to reduce release cycles, and it shows the ongoing tension between rapid development and strong security measures. These compromises can lead to real problems.
61% of organizations have experienced three or more successful exploitative attacks, and only 5% have managed to avoid any incidents altogether.
The impact is serious, as 72% of organizations report losing critical data, while 67% face operational disruptions and 62% experience brand degradation.
According to a GitLab developer survey, the adoption of DevSecOps practices has seen remarkable growth in recent years. 60% of rapid development teams embedded these practices in 2021, and it is a significant rise from just 20% in 2019. By 2021, 56% of operations teams reported that their processes were either fully or mostly automated.
Along with the importance of scaling DevSecOps for organizations, it should be noted that it also presents certain difficulties that ought to be addressed. As teams grow, the complexity of integrating new tools, maintaining coherent processes in various departments, and collaborating with other teams also grows.
Conflicts of codes occur when two or more developers upload conflicting changes to the same code at the same time, and this may cause a delay in the deployment of the application. Proper management of version control, which includes setting up strong code review policies and procedures, should be implemented to avoid such conflicts and support deployment.
Automation is one of the main principles of DevSecOps, and it can be difficult to achieve. You must ensure that all processes are automated, requiring substantial investment in time and resources and reducing manual tasks.
For any enhancement to be sustained, it is important to use adequate monitoring solutions alongside feedback loops. As systems expand, achieving performance visibility and collecting meaningful operational information becomes more challenging.
With an increasing number of microservices, cloud instances, and environments to secure, scaling DevSecOps requires careful integration of security practices into the pipeline. Getting compliant with the industry regulations makes it even more complicated as applications grow. It can also be very challenging to incorporate security tools into CI/CD pipelines since these tools must interface with the current development tools with ease. There is also a risk of too many overlapping tools, such that the teams get overwhelmed, which is called tool fatigue.
Scaling DevSecOps is about scaling skills. One must make sure that there are enough professionals in areas like automation, CI/CD, containerization, security, etc. This involves continuous training and, in some cases, hiring. Otherwise, without the needed expertise, scaling can lead to inconsistent practices and slower productivity.
Understanding when it is appropriate to scale up or down the DevSecOps is critical as it allows you to insert more security practices into the operations. Security should not be an afterthought but a fundamental step of software application development. This proactive approach mitigates risks and leads to more resilient and secure applications.
Organizations that suffer more cyberattacks, such as supply chain attacks, code tampering, ransomware, insider threats, credential theft, and API exploitation, should go ahead and scale up DevSecOps to better mitigate risks.
If you notice an upsurge in error rates in production code, it then means that you need to scale up the DevSecOps.
Increased workload on security teams can make it necessary to scale DevSecOps, as integrating security into CI/CD pipelines enhances workflows, optimizes resource utilization, and alleviates pressure on security teams.
The implementation of time-consuming and resourceful manual security checks or audits more often signifies the need to scale DevSecOps and, in such cases, automate these processes for efficiency.
If your company is even adopting DevOps, then extending DevSecOps will be a prerequisite to incorporate security into those new processes.
If your team is doing several deployments within one day, then there is a high chance that you will have to scale DevSecOps and incorporate security controls in such deployments.
You must follow the practices mentioned below to obtain the desired results.

You should start by evaluating your existing development and security processes. Then, you should identify gaps in security coverage, bottlenecks, and areas where manual processes are slowing down the workflow. This assessment will help you to understand the specific needs of your organization.
You must recognize specific challenges and requirements of your organization. You must ask yourself what would happen if the workload increased without resolving these issues. These weak points can include error-prone code, high cognitive load, less secure systems, or delayed deployments. Early addressing these issues prepares teams for a better tomorrow.
You must align scaling efforts with your organization’s priorities. These priorities can include rapid QA, deploying new features, maintaining deployment frequency, and accelerating delivery speed. You must assess how DevSecOps scaling can directly support each objective.
You should define clear, measurable goals. For example – reducing the time for pull requests to reach production or limiting weekly code deployment numbers. Metrics keep your team focused, provide insight into progress, and adjust strategies based on results.
You should scale DevSecOps incrementally by adapting one change at a time. This approach minimizes disruption and allows internal teams to provide feedback. It also helps in uncovering any unseen challenges. You should use this feedback to guide and prioritize future improvements.
You should select DevSecOps tools designed to scale and support team growth. It must take care of your organization’s evolving needs. Scalable tools should allow seamless integration across teams and minimize manual adjustments by paving the way for efficient growth.
| Tool | Category | Strengths |
|---|---|---|
| SonarQube | Source Code Analysis | Multi-language support, strong community, CI/CD integration. |
| Snyk | Dependency Scanning | Real-time vulnerability updates, seamless integration with CI/CD pipelines. |
| Aqua | Container Security | Container runtime security, Kubernetes integration. |
| Terraform Sentinel | Infrastructure as Code (IaC) Security | Policy-as-code, tightly integrated with Terraform, advanced policy controls. |
| OWASP ZAP | Dynamic Application Security Testing (DAST) | Free, open-source, dynamic analysis. |
| HashiCorp Vault | Secrets Management | Robust secret storage, access controls, and auditing capabilities. |
| Splunk Phantom | Security Orchestration, Automation and Response (SOAR) | Playbook automation, scalable for large teams. |
This structured approach ensures that scaling DevSecOps is aligned with organizational goals and executed sustainably.
Code signing is a critical component in scaling DevSecOps to ensure authentication, integration, and non-repudiation. The digital signature ensures that the code has not been tampered with or altered since it was signed, and it confirms that the software comes from a trusted source. By incorporating code signing into the CI/CD pipeline, organizations can enhance security without compromising speed.
Encryption Consulting’s CodeSign Secure is a tool designed to enhance the security of your software development process by automating the code signing process. Our solution easily integrates with popular DevOps CI/CD pipelines like GitHub Actions, Azure DevOps, TeamCity, Bamboo, Jenkins, and many more. This integration aligns with the principles of DevSecOps and ensures that security is built into the development workflow from the start.
CodeSign Secure also has a reproducible build feature with pre and post-hash validation processes. In pre-hash validation, the hash is first verified, and then the signature is attached, whereas in post-hash validation, the verification of the hash is done after the signature is attached to the file and is generally used in the development environment. This ensures the authenticity of the build while maintaining consistency and security throughout the entire software development and release process.
CodeSign Secure provides robust vulnerability scanning features like Static Application Security Testing (SAST) and Software Composition Analysis (SCA). These tools thoroughly scan your codebase for vulnerabilities and analyze all dependencies used in your project. Your files are only signed when no vulnerabilities are detected. This preventive approach ensures that only secure, trusted code is pushed to the repository.
Also, CodeSign Secure seamlessly integrates with SonarQube, which is a leading platform for continuous code quality inspection. SonarQube adds an extra layer of security by identifying security bugs and potential vulnerabilities in real-time and ensures that your code is secure throughout its lifecycle. This combination of vulnerability scanning and SonarQube integration ensures a proactive security posture within the DevSecOps pipeline while minimizing risks and maintaining high code quality standards.
Scaling DevSecOps is important for organizations aiming to maintain robust security while keeping up with rapid development and growing technological demands. By adopting a structured approach to scaling, such as automating security processes, adopting a culture of shared responsibility, and integrating DevSecOps tools, you can ensure that security measures evolve alongside your applications. Encryption Consulting’s CodeSign Secure provides the tools and expertise needed to seamlessly incorporate security into your DevSecOps workflows, making security a foundational part of your development process. With scalable solutions, enhanced governance, and real-time protection, we empower organizations to stay secure, compliant, and agile as they scale their operations.