CDP and AIA Points can sometimes be confusing but are the most important pillars of a functional PKI environment. Configuration of proper CDP and AIA points can result in a better and healthy PKI environment, and debugging those issues can be equally tricky. This article intends to be a way to stop any CDP/AIA issues that one may face during the PKI configuration and debugging stages.
Configuration of CDP/AIA Points
Proper configuration of CDP and AIA points can be tricky. It involves proper permission of where CRL needs to be published and where they would be accessed.
Improper configuration of CDP can result in two scenarios
- CRL fails to be published, or
- CRLs cannot be accessed
Similarly, if AIA is not configured properly, then certificates of root and issuing CAs cannot be accessed.
In both of the scenarios, PKI fails to function properly.
Configuration of AIA
AIA is the easiest to configure. If OCSP is used, the AIA decimal point may include 34; otherwise, it’s always 2.
| Display Name | Decimal Value |
|---|---|
| Publish at this location | 1 |
| Include in the AIA extension of issued certificates | 2 |
| Include in the Online Certificate Status Protocol (OCSP) extension | 32 |
Decimal Value 1 is included when publishing in the %windir%\System32\certsrv\CertEnroll location. It can also be included to publish directly onto the AIA location if proper permissions are provided.
[Note: If the location is behind a load balancer, the CA cannot access both servers and may cause failure. Please do not publish on those locations; instead manual copy is recommended]
Decimal Value 2 is included when the URL is to be added to the issued certificates. These URLs act as the AIA points from where the certificates can be extracted.
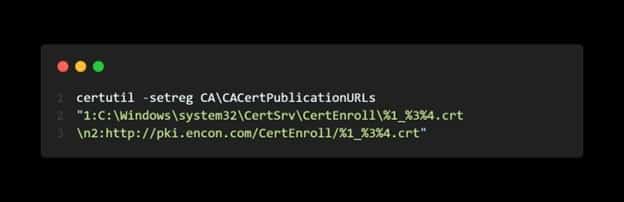
Example:
Here, we provide a local CertEnroll folder with decimal value 1, as it is where the AIA would be published. The HTTP location has a decimal value of 2, where we won’t publish the certificates, but it will act as an AIA location from where other clients can access its certificate.
Configuration of CDP
Configuration of CDP can depend on how the CA is configured, how the CRLs are published and accessed, and if Delta CRLs are published.
| Display Name | Description | Decimal Value |
|---|---|---|
| Publish CRLs at this location | Used by the CA to determine whether to publish base CRLs to this location | 1 |
| Include in the CRL Distribution Point (CDP) of issued certificates | Used by clients during revocation checking to find base CRL Location | 2 |
| Include in [base] CRLs | Used by clients during revocation checking to find delta CRL location from base CRLs | 4 |
| Include in all CRLs | An offline CA can use it to specify the LDAP URL for manual publishing CRLs. You must also set the explicit configuration container in the URL or the DSConfigDN value in the registry. certutil -setreg CA\DSConfigDN CN= |
8 |
| 16 | ||
| 32 | ||
| Publish Delta CRLs to this location | Used by the CA to determine whether to publish Delta CRLs to this location | 64 |
Decimal values are used accordingly based on how the CDP needs to be configured.
Decimal Value 1 is mostly used to publish CRLs to %windir%\System32\certsrv\CertEnroll location or to those locations where CA has proper permissions to access. If Delta CRLs are also published, 65 (1+64) is used.
[Note: If the location is behind a load balancer, the CA cannot access both servers and may cause failure. Please do not publish on those locations; instead manual copy is recommended]
Decimal Value 2 includes the URL or location and lets it act as a CDP location from where base or delta CRLs are accessed.
Example
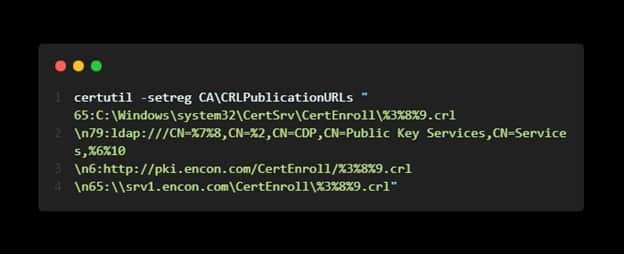
Decimal Value 79 = CRLs are published at that location (1) + Location is added to CDP (2) + Delta CRL location (4) + Include in all CRLs (8) + Publish Delta CRL at this location (64)
Decimal Value 65 = Publish CRL at this location (1) + Publish Delta CRL at this location (64)
Decimal Value 6 = Location is added to CDP (2) + Delta CRL location (4)
CRL Replacement Tokens
In the above examples, you may have noticed %1, %3, %4, %8, and %9. This represents how the CA is configured and what the file’s name should be. If the files are renamed, the AIA and CDP points may fail as the naming convention doesn’t match.
| Token Name | Description | Map Value |
|---|---|---|
| ServerDNSName | The DNS name of the CA Server | %1 |
| ServerShortName | The NetBIOS name of the server | %2 |
| CAName | The name of the CA | %3 |
| Cert_Suffix | The renewal extension of the CA | %4 (as per Windows 2000 mapping) |
| CertificateName | %4 (as per Windows 2003 mapping | |
| ConfigurationContainer | The location of the Configuration container in AD | %6 |
| CATruncatedName | The “sanitized” name of the CA | %7 |
| CRLNameSuffix | The renewal extension of the CRL | %8 |
| DeltaCRLAllowed | If Delta CRL is allowed, + is added at the end of the file to indicate a delta crl | %9 |
| CDPObjectClass | %10 | |
| CAObjectClass | %11 |
Based on the mapping value, the AIA and CDP points are given a naming convention to find the correct file from those locations.
Debugging CDP/AIA location issues
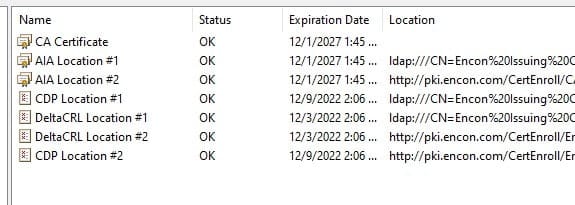
If the CDP/AIA locations are properly configured, these steps will temporarily help resolve the issues. For example, we will use AIA issues, which will also work for CDP issues.
After we open and check PKIView.msc, we can see where the issue is. We can copy the URL to a notepad for further investigation.
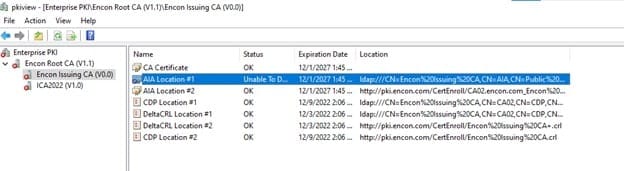
The AD doesn’t have our certificate if the issue is on the LDAP location. This is quite an easy fix.
Certificates retrieved via LDAP are retrieved from Domain Controller. If we open Domain Controller and ADSIEdit.msc, then we can navigate to Services > Public Key Services > AIA and check the present certificates. Since our Issuing CA Certificate is absent, the PKI environment cannot retrieve the certificate from that location.
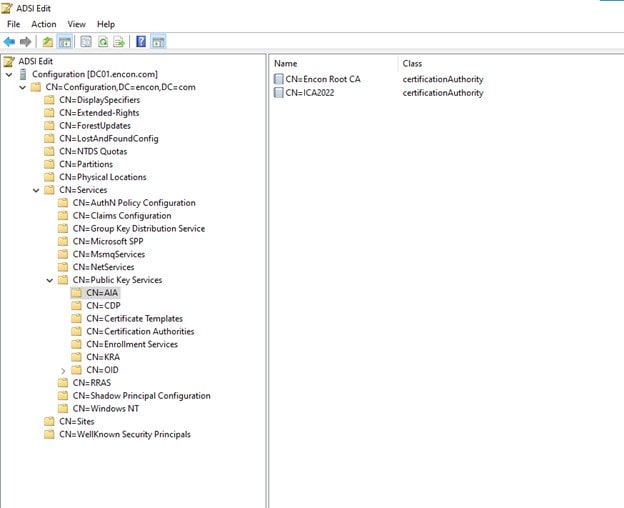
To resolve this, we navigate to our issuing CA and run the command
certutil -dspublish -f <path to certificate> SubCA
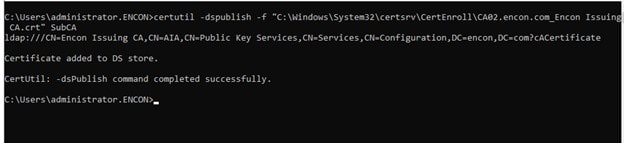
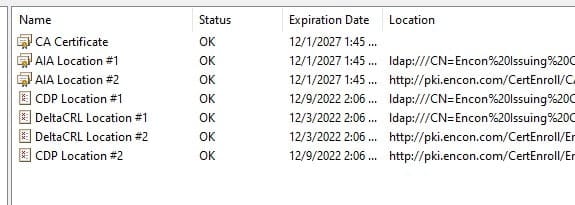
Once the command runs successfully, we can refresh our PKIView.msc to check if the issue is resolved, and we should see a clean slate
However, if the AIA location #2, or the HTTP location is causing errors, this error is because the certificate isn’t present at that server endpoint.
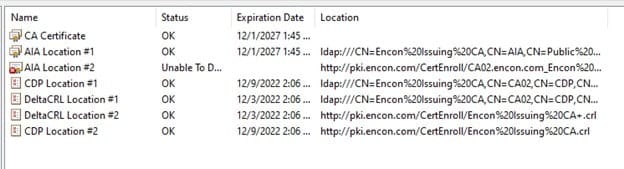
To resolve this, we copy the certificate from %windir%\System32\certsrv\CertEnroll location to our web server, which hosts our certificate.
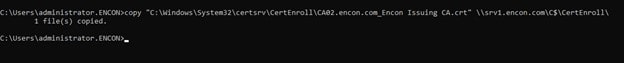
This would resolve our issue, which we can check on PKIView.msc again.
Conclusion
Issues with CDP and AIA locations can be tricky. Misconfiguration can often cause issues, which can be harder to track. With this guide, we hope to make the configuration of CDP/AIA points much easier with debugging steps to support any technical issues.




