A cipher suite is a set of algorithms that help secure online communications by encrypting data and ensuring its integrity. These algorithms play a crucial role in protecting sensitive information, such as your payment details or personal data, during online transactions.
But how does this work in practice? Have you ever wondered what happens behind the scenes when you enter your credentials while making an online purchase? How is it possible for the transaction to happen securely within a few seconds? Right before you enter your payment details, you might notice a little padlock icon in the address bar. Ever wondered what that padlock really means?
That padlock is more than a symbol. It represents the start of a secure handshake between your browser and the website, initiated by a set of cryptographic tools called cipher suites.
What are Cipher Suites?
It is a collection of algorithms that dictate how information is encrypted and decrypted during an SSL/TLS handshake. It specifies the algorithms used to secure the communication channel between your web server and the browser.
So, what actually happens behind the scenes?
When you open a web browser and visit a site, like your online banking platform, your browser starts a connection with the bank’s web server, and this is where SSL/TLS steps in, ensuring the communication between the server and browser is secure and in this process cipher suites play a crucial role by ensuring that the information sent between a client and server is secure, private, and unaltered.
The handshake process of SSL/TLS starts when the client sends a message known as a client hello to the server, listing supported cipher suites in order of preference. The server reviews this list and selects a cipher suite that both the browser and the server can support, and that is secure enough for the connection. Once a cipher suite is selected, it is used to secure the communication channel between the browser and the server.
Cipher suites play an important role in the broader context of cybersecurity as they are the building blocks of secure communication protocols like SSL/TLS. They define the algorithms used for encryption, authentication, and key exchange, which together ensure data confidentiality, integrity, and authenticity during transmission. Just like choosing the right combination of locks and keys to protect a safe, a cipher suite carefully selects the strongest cryptographic algorithms to ensure your data remains private and untouched.
Components of Cipher Suites and Role of Cipher Suites in TLS
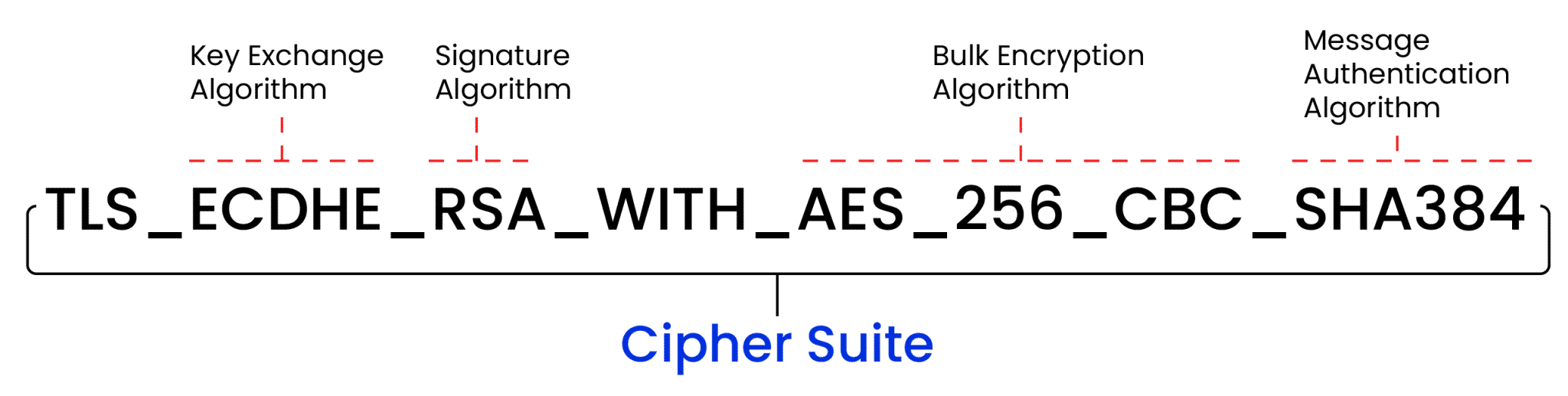
There are different algorithms that make up a cipher suite, and each has its own specific purpose of guaranteeing that the transmission of data is safe, private, and intact. A cipher suite usually contains the following items:
-
Key Exchange Algorithms
To keep data secure, the transmitted information between the client and server during the communication needs to be encrypted. For this process, both the server and client create a shared secret key, which is then used to encrypt and decrypt the data exchanged during that session. The key exchange algorithm defines how these keys are shared between the client and server in a way that only they know. Popular key exchange algorithms include RSA (Rivest-Shamir-Adleman), DH (Diffie-Hellman), ECDHE (Elliptic Curve Diffie-Hellman Ephemeral), and ECDH (Elliptic Curve Diffie-Hellman) because they securely share encryption keys, ensuring that only the client and server can decrypt the session data.
-
Authentication Algorithms
Authentication algorithms ensure that the client and server can verify each other’s identities. This prevents attacks like man-in-the-middle attacks, where someone could intercept the communication. These algorithms use digital signatures or public key cryptography to validate identities. Preferred authentication algorithms are RSA(Rivest-Shamir-Adleman), DSA (Digital Signature Algorithm), and ECDSA (Elliptic Curve Digital Signature Algorithm) for verifying identities through digital signatures.
-
Bulk Encryption
This algorithm is responsible for ensuring confidentiality by encrypting the real information exchanged between the client and server. It scrambles the content of the communication so that even if it is intercepted, it cannot be read. Bulk encryption algorithms are designed to secure large amounts of data efficiently. Some commonly used bulk encryption algorithms are AES, ChaCha20, 3DES, and CAMELLIA because of their ability to securely encrypt large amounts of data efficiently, ensuring confidentiality during communication.
-
Message Authentication
While sending sensitive information over the Internet, it is necessary to ensure that the message remains intact and has not been modified during the transmission. That’s exactly where message authentication codes (MACs) come into play. A MAC acts like a unique signature that confirms the integrity of the message. The sender generates the MAC for the message, and the receiver checks it upon receiving the message to confirm that it has not been altered in any way. Cipher suites often use algorithms like SHA-256, SHA-384, MD5, and POLY1305 because they generate unique message authentication codes (MACs), ensuring data integrity and preventing tampering.
In short, each part of a cipher suite works together to make sure that the information sent between a client and server is secure, private, and unaltered. Whether it is a banking transaction or a routine email, understanding the components of cipher suites can give you a better grasp of how your online activities are kept secure.
Why is it Necessary to Select Strong Cipher Suites?
Let us imagine a situation where you are sitting in a restaurant and using the free Wi-Fi to check the balance of your bank account. Nothing seems to be wrong, but are you aware that a person sitting nearby could hack your details if adequate protection is not put in place?
Using techniques like packet sniffing or man-in-the-middle attacks, a hacker can capture your data as it travels over the network. If your connection is not secured with strong encryption, your login credentials and sensitive information could be exposed, putting your overall security at significant risk.
This makes it crucial to select a strong cipher suite. Let us explore more about how they keep your data safe and secure:
-
Prevents Eavesdropping
How secure will you feel knowing that the message that you want to send to someone is being sent to the unintended recipient?
This happens in a Man-in-the-Middle (MITM) Attack, where the attacker intercepts and relays communications between two parties who believe they are directly communicating with each other. If a weak cipher is used, the attacker can decrypt, alter, or inject messages, compromising both confidentiality and integrity.
Weak cipher suites make it easier for attackers to fetch and decrypt sensitive information, such as users’ credentials and financial details. On the other hand, employing strong encryption methods like AES-GCM and ChaCha20 ensures that even if the connection is intercepted by the attacker, no information transmitted over it will be accessible to the attacker.
AES-GCM and ChaCha20 are considered strong encryption methods because they use advanced techniques to protect data confidentiality and integrity. AES-GCM (Advanced Encryption Standard in Galois/Counter Mode) combines encryption with an authentication layer, which verifies data integrity alongside encryption, making it impossible to alter or decrypt the data without the correct key. ChaCha20 is a fast, secure stream cipher that works efficiently even on low-power devices, providing strong encryption through complex mathematical operations. Both algorithms use large key sizes and resist brute-force and cryptographic attacks, making intercepted data unreadable to attackers.
-
Preserving Data Integrity
Imagine yourself in the following situation: You are sending a crucial document to your manager, but someone intercepts it during transmission and alters its content. Isn’t it concerning? So, how can you ensure that your message is not altered during its transmission?
In a strong cipher suite, a reliable message authentication scheme, such as HMAC with SHA-256, is used to ensure that the data received by the receiver is exactly the same as the data sent by the sender, i.e., no modification is done during the transit. If some changes are made in the data, the receiver will be able to spot it, and thus, the sender will ignore this data packet and request that it be sent again.
HMAC with SHA-256 combines a secret key with the SHA-256 hash function to create a unique code that ensures data integrity. The receiver recalculates the HMAC using the same key to verify the message has not been tampered with. It is considered strong because it resists attacks like collisions and brute force, and the use of SHA-256 makes it computationally secure and resistant to reversal.
-
Ensures Confidentiality
Now, picture the scenario above once again.
What if some sensitive information you had to transmit gets disclosed during the exchange? And what if your opponents get access to that information, for example, business development plans, strategies, or any sensitive data about your clients? Isn’t it concerning?
When encryption algorithms are not applied appropriately, attackers can take advantage of weaknesses present in the system to retrieve private information. Therefore, to secure connections and protect sensitive information such as user credentials or personal information, an effective means of encryption, such as the use of AES 128-bit keys, or rather AES 256-bit keys, is employed.
-
Facilitates Perfect Forward Secrecy (PFS)
Would you feel safe if someone had access to your key today and could access your previous conversations? Yes, this is possible if the encryption does not include Perfect Forward Secrecy (PFS).
Perfect Forward Secrecy (PFS) is an advanced encryption feature that enhances the confidentiality of communications. PFS cipher suites ensure that even if an attacker compromises the private key of a server or client, they cannot decrypt previously captured data. This is achieved by using ephemeral keys, which are unique to each session and are discarded after the session ends. By preventing attackers from leveraging stolen keys to access past communications, it adds an additional layer of security, ensuring long-term protection of sensitive data.
-
Meets Security Compliance Standards
Choosing strong cipher suites is critical for ensuring that you minimize risks and comply with the regulations applicable to your industry. For example, when processing payments that involve credit card transactions, you should comply with the PCI-DSS standard. The consequences of not employing effective encryption strategies as mandated by standards could result in the serious risks of fines, sanctions, or even adverse effects on the image of the business. Effective cipher suites ensure that these requirements are fulfilled and businesses, as well as their clients, do not suffer legal challenges.
-
Reduces Vulnerabilities
Now, let us talk about the importance of staying up to date.
Using outdated cipher suites such as RC4, DES, or even 3DES is like guarding yourself against criminals with an ancient rusty lock on the front door. When you recognize that the existing security measures are insufficient, the natural response is to upgrade to a more advanced system.
Similarly, transitioning to modern, robust cipher suites ensures stronger algorithms that are more resistant to attacks, effectively safeguarding your sensitive information from external threats.
Cipher suites such as TLS_AES_128_GCM_SHA256, TLS_AES_256_GCM_SHA384, and TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 are indeed commonly used in modern organizations. These suites use strong encryption algorithms like AES (Advanced Encryption Standard) and ECDHE (Elliptic Curve Diffie-Hellman Ephemeral) to ensure that data transmission is both secure and efficient
Comparing TLS 1.2 and TLS 1.3 Cipher Suites
TLS (Transport Layer Security) is a protocol that ensures secure communication over the Internet by encrypting data between a client and a server. It protects sensitive information, like passwords and credit card details, from being intercepted by attackers. TLS also verifies the authenticity of the parties involved, ensuring you are communicating with the intended source and not an imposter. It is the backbone of online privacy and security. TLS has evolved through versions 1.0, 1.1, 1.2, and 1.3, with each newer version offering enhanced security and performance. TLS 1.0 and TLS 1.1 are outdated and no longer recommended due to their vulnerabilities. The most widely used versions today are TLS 1.2 and TLS 1.3.
In terms of cipher suites, when shifts were made from TLS 1.2 to TLS 1.3, major improvements in security, speed, and ease of use were seen due to the following reasons:
-
Cipher Suites
-
TLS 1.2: Cipher suites are complex as they contain four distinct components:
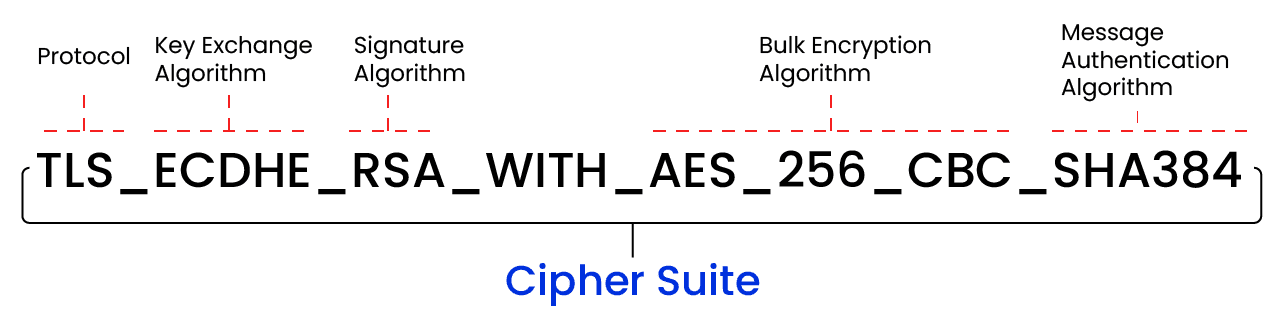
TLS is the protocol that is being used, ECDHE indicates the Key Exchange algorithm, RSA is the Authentication algorithm, AES128-GCM is the Bulk Data Encryption algorithm, and SHA256 is the Message Authentication Code (MAC) algorithm.
Supported cipher suites in TLS 1.2 are:
- TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
- TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
- TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_DHE_RSA_WITH_AES_128_CBC_SHA256
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256
- TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256
- TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305
-
TLS 1.3: It simplifies cipher suites by reducing them to two main components: an AEAD (Authenticated Encryption with Associated Data) algorithm, such as AES-GCM or ChaCha20-Poly1305, which combines encryption and integrity, and separate mechanisms for key exchange and authentication during the handshake. The absence of standalone integrity algorithms is compensated by AEAD’s ability to encrypt and authenticate data in a single step, ensuring data confidentiality and integrity. Moreover, TLS 1.3 mandates Perfect Forward Secrecy (PFS), guaranteeing that even if a private key is compromised, previous communications remain secure, thus maintaining a high standard of security. For example:
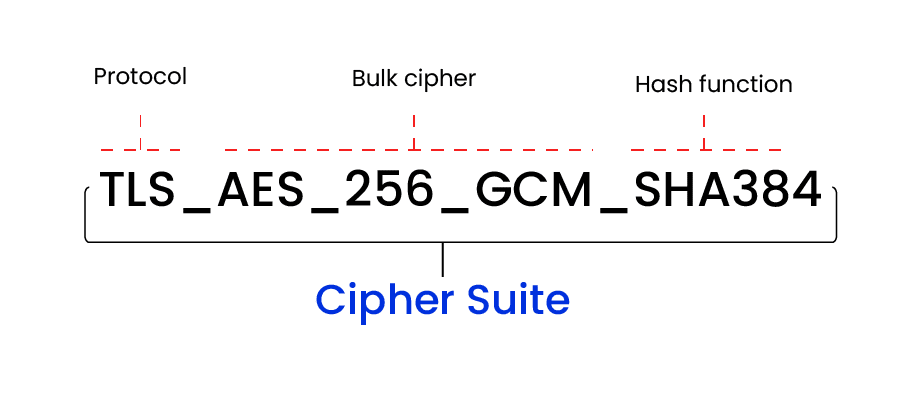
TLS indicates the protocol that is being used, AES-256-GCM is used for authenticated encryption, and SHA-384 is the hash function used for the given TLS handshake.
With the introduction of TLS 1.3, several old and insecure ciphers were deprecated for the following reasons:
- RC4
RC4 was deprecated because it was found to have significant vulnerabilities that allowed attackers to recover plaintext from ciphertext, particularly through biases in the RC4 keystream. These weaknesses made it unsuitable for secure communications.
- DSA (Digital Signature Algorithm)
DSA is weaker compared to modern elliptic curve cryptography (ECC) algorithms. While it was once widely used for digital signatures, ECDSA (Elliptic Curve Digital Signature Algorithm) and other elliptic curve-based algorithms offer much better security and performance. DSA also tends to be slower and less efficient.
- MD5 and SHA-1
Both MD5 and SHA-1 have been found to be cryptographically broken due to vulnerabilities like collision attacks. These algorithms allow attackers to find two different inputs that hash to the same value, undermining their use for integrity checks or signatures.
- Weak Elliptic Curves
Some older elliptic curves used in ECDSA and ECDHE (Elliptic Curve Diffie-Hellman) were vulnerable to advanced cryptographic attacks that exploit their weak parameters.
- RSA Key Exchange
RSA key exchange does not provide Perfect Forward Secrecy (PFS). Without PFS, if an attacker ever compromises the private RSA key, all previous communications encrypted with that key can be decrypted. Modern key exchange mechanisms, like ECDHE (Elliptic Curve Diffie-Hellman Ephemeral), provide PFS by using ephemeral keys that are discarded after the session ends.
- Static Diffie-Hellman (DH, ECDH)
Static Diffie-Hellman (including ECDH) is vulnerable because it uses static (long-term) keys, which do not provide Perfect Forward Secrecy. If the private key is compromised, all past communications are also at risk. The ephemeral versions of these protocols (ECDHE, DH-E) offer better security as the keys are generated and discarded on the fly.
- Block Ciphers (CBC Mode)
CBC (Cipher Block Chaining) mode block ciphers are vulnerable to attacks like padding oracle attacks (e.g., BEAST, POODLE, Lucky Thirteen). These attacks exploit vulnerabilities in the way padding is handled in CBC mode, leading to potential plaintext recovery.
- Non-AEAD Ciphers
Non-AEAD (Authenticated Encryption with Associated Data) ciphers do not include built-in integrity checks. This makes them prone to attacks such as bit-flipping or truncation, which can alter the ciphertext without detection, potentially compromising the security of the communication.
- RC4
- TLS_AES_256_GCM_SHA384
- TLS_CHACHA20_POLY1305_SHA256
- TLS_AES_128_GCM_SHA256
- TLS_AES_128_CCM_8_SHA256
- TLS_AES_128_CCM_SHA256
Overall, these older and weaker ciphers were deprecated in TLS 1.3 to improve security and performance and ensure the highest standards of cryptographic protection. TLS 1.3 relies on modern, stronger algorithms, like AEAD ciphers, ECDHE, and SHA-256 (or better) for hashing, which offers robust security and resistance to contemporary cryptographic attacks.
The supported cipher suites in TLS 1.3 have now dropped to just five and are the following:
-
-
Key Exchange and Authentication
-
TLS 1.2:
RSA is commonly used for both key exchange and authentication, but if the private key gets compromised, past sessions can be decrypted, i.e., it fails in making the communication channel forward secure.
-
TLS 1.3:
RSA key exchange is no longer supported. Instead, only FFDHE or ECDHE is used, ensuring Perfect Forward Secrecy for every session. For authentication, ECDSA or RSA signatures are used only to facilitate the handshake. Moreover, TLS 1.3 combined the ServerHello and EncryptedExtensions messages into a single message, simplifying the handshake.
The ServerHello message is sent by the server in response to the client’s ClientHello and includes essential information such as the protocol version, session ID, and selected cipher suite. The EncryptedExtensions message contains additional parameters necessary for the secure connection, such as supported groups and signature algorithms. By combining these messages, TLS 1.3 reduces the number of round trips required to establish a secure connection, enhancing performance.
-
TLS 1.2:
-
Bulk Encryption
-
TLS 1.2:
Bulk encryption was typically achieved using block ciphers like AES in modes such as CBC, which had multiple weaknesses that made it susceptible to exploitation by padding Oracle attacks. A Padding Oracle attack occurs when an attacker exploits weak error handling in padding schemes of block ciphers, like AES-CBC, to decrypt data. By manipulating ciphertext and analyzing server responses, the attacker can gradually recover the plaintext.
-
TLS 1.3:
Authentication and encryption are done more efficiently in one process using Authenticated Encryption with Associated Data (AEAD) ciphers like AES-GCM or ChaCha20-Poly1305.
-
TLS 1.2:
-
Message Authentication
-
TLS 1.2:
MAC algorithms are used to verify the integrity of messages.
-
TLS 1.3:
Eliminates the use of MACs because AEAD substitutes encryption and separates MACs within the upper layer protocol. This removes potential vulnerabilities that can arise from mismatched or weak MAC choices and simplifies the entire process.
-
TLS 1.2:
-
Handshake Speed
-
TLS 1.2:
Requires two round trips for a handshake to complete.
-
TLS 1.3:
The entire handshake procedure has been reduced to just one round trip (client-server-client) to reduce the time taken to connect. With the introduction of 0-RTT or Zero Round Trip Time in relation to session resumption, the clients can reconnect in a matter of seconds with some security trade-offs. While it improves performance, it can expose the connection to replay attacks if not effectively managed.
-
TLS 1.2:
-
Perfect Forward Secrecy
-
TLS 1.2:
If you needed Perfect Forward Secrecy, you had to choose specific cipher suites because not all the supported algorithms offered PFS.
-
TLS 1.3:
But in TLS 1.3, PFS support is built into every connection. Just like auto-locking doors for your car, no extra steps are required, and you are always protected. Similarly, PFS is mandatory and, therefore, provides greater protection of past communications.
-
TLS 1.2:
-
Outdated Algorithms
-
TLS 1.2:
Supported weaker, deprecated algorithms like:
- RC4:Not used due to biases that allow ciphertext analysis.
- CBC mode: Vulnerable to attacks like Poodle.
- DES and 3DES: Due to their small key size, are vulnerable to brute-force attacks.
-
TLS 1.3:
Removed support for these weak algorithms and uses only modern ciphers like:
- ChaCha20-Poly1305: A fast and secure cipher for devices that do not support AES hardware.
- AES-GCM: AES with Galois/Counter Mode, which provides both encryption and authentication.
-
TLS 1.2:
-
Default Security
-
TLS 1.2:
Offers a wide range of options, but not all of them are secure, which can result in weakened security if configured inappropriately.
-
TLS 1.3:
It has fewer choices, but every option it supports is strong and secure by default, which results in better overall security.
-
TLS 1.2:
To sum it up, TLS 1.3 brings faster speeds, stronger security, and is simpler to set up. It is like switching from an old car with manual locks to a new one with advanced safety features, so you do not have to worry much because you know you are well protected.
How can Encryption Consulting help?
Encryption Consulting can help by offering expert advice and support tailored to your encryption needs. With our Encryption Advisory services we bring years of experience to assist you in creating strong, customized encryption strategies for your organization.
One of our key offerings is PKI as a Service (PKIaaS), which provides continuous, 24/7 support to address any challenges related to the Public Key Infrastructure (PKI) environment. With this service, organizations can proactively manage their cryptographic keys, certificates, and authentication processes to ensure secure communications. This comprehensive approach significantly strengthens security and minimizes the risk of potential vulnerabilities or misconfigurations in encryption setups.
Conclusion
In a world where data security is more critical than ever, understanding and selecting the right cipher suite is key to keeping your data secure. By choosing strong, updated cipher suites, you can significantly reduce vulnerabilities, protect sensitive information, and maintain data integrity. The transition from TLS 1.2 to TLS 1.3 has made this process even smoother, with better security, performance, and easier configuration.
For any organization, prioritizing strong cipher suites does more than just securing data, as it builds trust with clients, ensures compliance, and helps to guard against potential threats. Since the cybersecurity landscape changes rapidly, staying informed and proactive about encryption standards is a wise strategy to keep data safe well into the future.

