- What is Certificate Provisioning?
- The Importance of Certificate Provisioning in Cybersecurity
- A Simple Guide on Downloading Your Certificate Files from CA
- Downloading the SSL Certificate in Windows using the Chrome Browser
- One Certificate, Many Servers: Is It Possible?
- How one TLS/SSL Certificate can be installed on Multiple Servers?
- Important Aspects to note while Installing a Single SSL Certificate on Multiple Servers
- How can Encryption Consulting help?
- Conclusion
When you browse the web and enter your personal details or payment information, you probably notice a small lock icon on your browser’s address bar. That lock is a sign of trust, a symbol representing your private and secure connection. But what is behind that lock, and how did it get there?
Behind the lock icon lies a certificate issued, verified, and installed by a process known as certificate provisioning. Without such a process, online communication would be open to attacks and unauthorized access.
What is Certificate Provisioning?
Certificate provisioning is a detailed concept that entails requesting, issuing, maintaining, and revoking a certificate. Automated steps manage applications, services, or devices to efficiently and securely issue, reissue, or revoke certificates. These certificates serve as virtual IDs with the goal of verifying the identity of the site to ensure that the exchanged information is encrypted and safe from interception.
The five major components of certificate provisioning are:
-
Certificate Request
This process begins the provisioning chain of events. It is often initiated by a device or application that needs to receive a certificate. A formal request known as a Certificate Signing Request (CSR) is made to the Certificate Authority (CA) to issue a certificate for secure communication. A CSR is a block of encoded text that includes details such as the organization’s name, domain name, country, and public key. The CA uses these details to create and issue a digital certificate.
-
Certificate Generation
Once the Certificate Authority (CA) validates CSR, the process of generating the certificate begins. This may include creating a key pair (public and private keys) if the CSR does not already provide one. The CA then signs the certificate using its private key to ensure the authenticity of the certificate and establish trust. The generated certificate contains essential details such as the entity requesting it (subject), the public key, the expiration date, and the CA’s digital signature. This signed certificate is now ready to be issued for secure use.
-
Certificate Issuance
This is the process of providing the requested certificate to the requesting entity, such as a website or application, usually over a safe channel. Secure delivery of the certificate is crucial to ensure it is not intercepted or tampered during transmission. The issued certificate can be installed and used for secure communication, authentication, and encryption.
-
Certificate Management
An ongoing process of maintaining certificates to ensure they are properly maintained throughout their lifecycle. It includes renewing certificates before they expire, updating details such as domain name, and monitoring for potential issues like expiration or compromise. Organizations usually rely on automation tools such as CertSecure Manager to streamline tasks and prevent outages due to expired certificates.
-
Certificate Revocation
The process of withdrawing a certificate from active status and notifying that it is no longer valid or has been compromised. Notification of revocation is sent to inform relevant parties that the certificate is no longer trusted. Revocation also ensures that it cannot be used for malicious purposes.
Certificate provisioning is used in many situations to keep communications safe and shield sensitive data. In e-commerce, SSL/TLS certificates are used to secure online transactions, while in enterprises, S/MIME certificates safeguard email communications. IoT systems also rely on automated certificate provisioning to secure device-to-device communication, and cloud services and APIs utilize certificates to encrypt data exchanges.
DevOps pipelines use provisioning to make microservices and containers communicate securely. It is also crucial for regulatory compliance in industries like finance and healthcare, enabling encrypted communication and data protection. Through automated certificate provisioning, remote employees get secure VPN access, ensuring uninterrupted connectivity and security.
The Importance of Certificate Provisioning in Cybersecurity
The right certificates provide websites with encryption, data protection, and authenticity. They play an important role in maintaining trust and securing user information. Proper certificate provisioning ensures encryption of all the communications between your site and the users. An SSL/TLS certificate encrypts data like passwords, credit card numbers, and other confidential information into an unreadable format that only authorized parties can decrypt. This ensures the data stays secure and unaltered during transmission, protecting it from unauthorized access or tampering. Without a valid certificate, this data would be vulnerable to malicious alterations or theft.
Moreover, certificate provisioning helps establish the authenticity of your site. Think of certificates as a digital passport proving the authenticity of your site and securing the exchange of data. They are issued by trusted organizations, known as Certificate Authorities (CAs), to validate the identity of the site and prove to users that it’s safe to share sensitive data.
A Simple Guide on Downloading Your Certificate Files from CA
After you have successfully requested and obtained your SSL/TLS certificate from the CA, the next phase is downloading the certificate files. The following steps will help you to download your certificate files from the CA:
-
Log in to Your CA Account:
After your certificate is issued, log in to your CA account to download the certificate files. Sometimes, the CA will even provide you with a direct link to download your certificate, making it super convenient!
-
Go to the Certificates Section:
After logging in, go to “Certificates” or “My Certificates” in your dashboard. This is where all your issued certificates will be stored.
-
Search for Your Certificate:
In the Certificates section, there is a list of all the certificates that have been issued to you. Search for and click on the appropriate certificate you wish to save.
-
Choose the Right Format and Download:
Select the right format depending on the type of server you use:
- CRT: The .crt format contains the public key and certificate chain, including intermediate and root certificates, and is commonly used in UNIX-based systems for direct integration into server configuration files.
- PEM: The .pem format is a flexible, text-based format used for storing certificates and private keys in a Base64-encoded text format, often in Apache or Nginx servers, due to its ease of use in configuration files.
- PFX: The .pfx format bundles the certificate, private key, and certificate chain in a binary file, typically used primarily in Windows servers. It simplifies certificate import/export on Microsoft systems like IIS or Exchange Server.
-
Protect Your Certificate Files:
Encrypted storage is a safe option. Therefore, ensure that you store your private key securely and never share it with anyone, so that they remain inaccessible to entities with malicious intentions.
To summarize, after obtaining the certificate, one needs to visit the certificate authority’s website, log in, and search for the certificate to be downloaded. According to your server, select the preferable format of your choice and click on download. If something about a certain file format does not make sense to you, CAs assist you prior to making the wrong decision with the file format.
Downloading the SSL Certificate in Windows using the Chrome Browser
SSL certificates are primarily used to secure communication between clients and servers, ensuring data privacy and protection from interception. They are crucial in e-commerce platforms, banking applications, and any website handling sensitive user data. By following the steps mentioned, you can download the SSL certificate using the Chrome browser in Windows.
Step 1: Visit the website from which you want to download the certificate.
Here, https://www.encryptionconsulting.com/ site is opened.
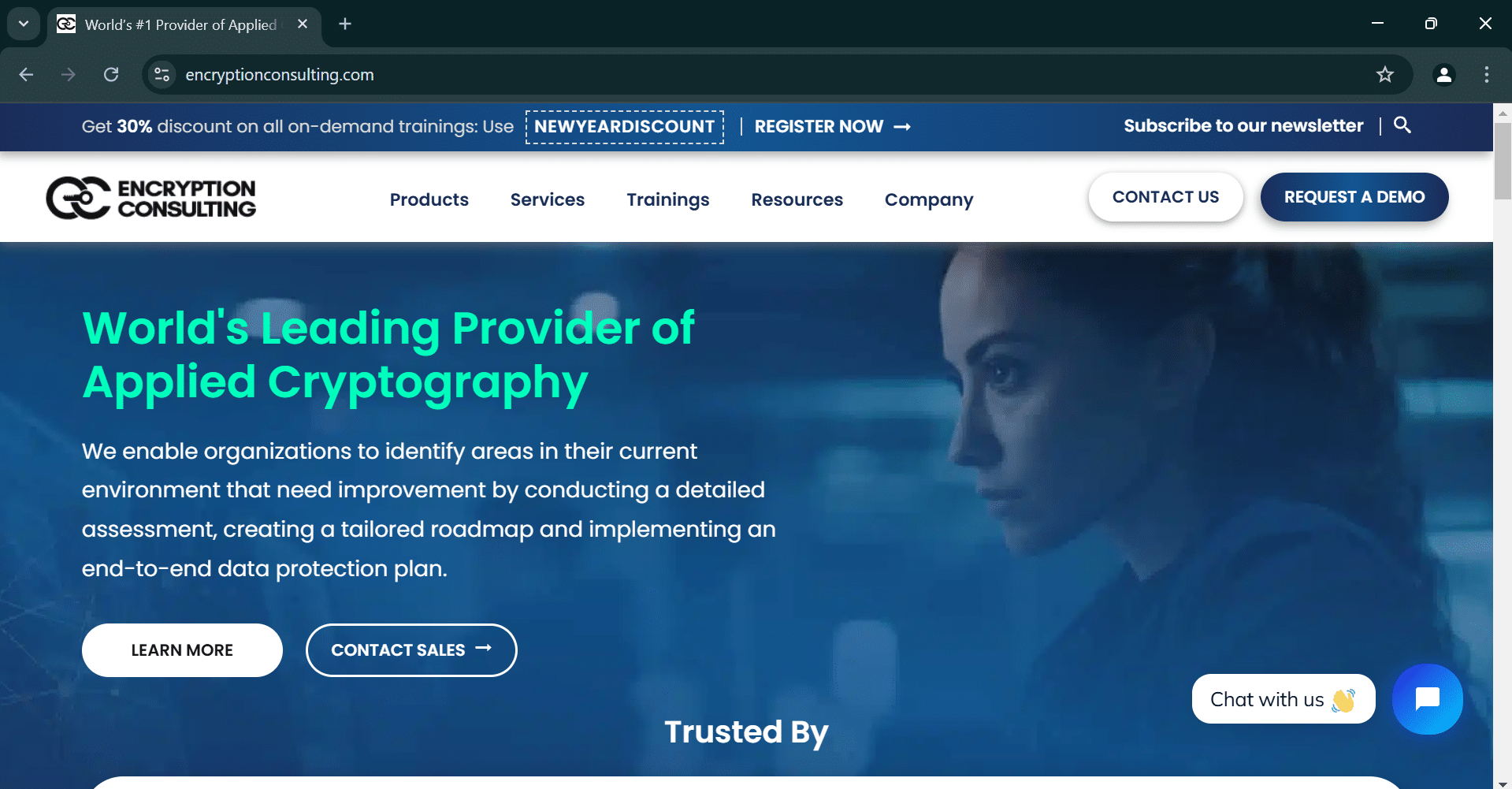
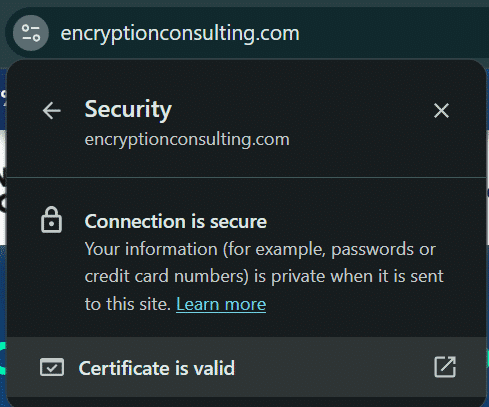
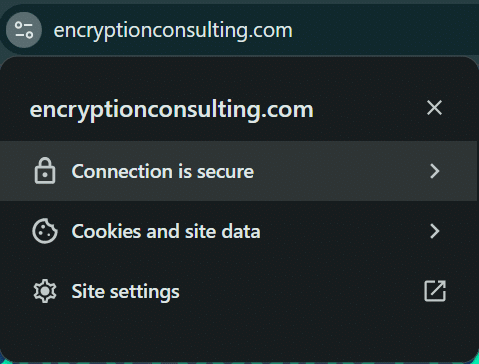
Step 2: Click on the secure icon next to the URL
Click on “Connection is Secure” and then, “Certificate is valid.” This indicates that the website’s communication is encrypted and the SSL certificate is working correctly.

Step 3: Select “Details” and “Export”
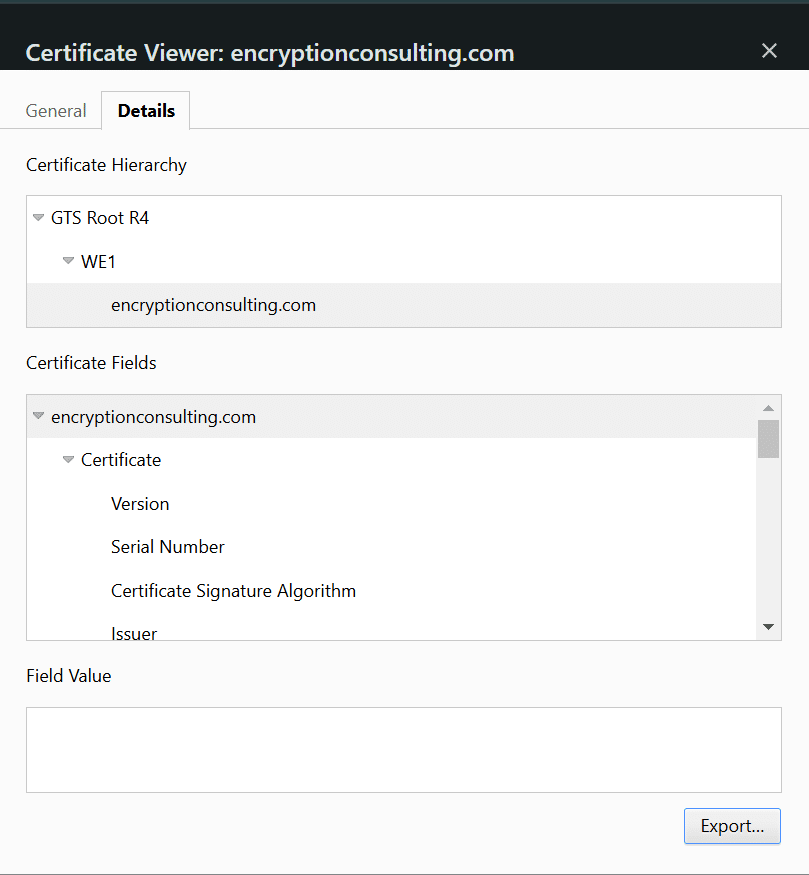
Step 4: Save Your Certificate File
Select the desired format (usually Base-64 encoding X.509 .CER) and enter the file name. Click Save.
One Certificate, Many Servers: Is It Possible?
Yes! One TLS/SSL Certificate can be installed on any number of servers, and the below-mentioned points describe how to install one SSL Certificate on multiple servers.
-
Using a Wildcard SSL Certificate
A wildcard certificate secures all subdomains of a primary domain with a single certificate. For example, a wildcard certificate for *.example.com would cover www.example.com, site.example.com, and blog.example.com. This certificate can be installed on multiple servers within the same domain without needing individual certificates for each subdomain or purchasing additional ones. This makes them especially useful for growing businesses or organizations with evolving needs, as they can easily secure new subdomains without additional complexity or costs.
-
Using a Subject Alternative Name (SAN) Certificate
SAN certificates, also known as multi-domain certificates, allow you to secure multiple domains or subdomains under one certificate. For example, you can secure www.example.com, site.example.com, and blog.example.net with a single SAN certificate. SAN certificates can be particularly useful if you are running multiple sites on different servers but want to maintain a single certificate for all.
-
Exporting and Importing the Certificate
Once a certificate is generated and installed on one server, you can export the certificate along with its private key and install it on other servers. This is particularly common for load-balanced environments, where multiple servers distribute incoming traffic to ensure high availability, reliability, and secure connections from end-users, and the same certificate needs to be used across all servers for consistent and secure communication.
-
Using Load Balancers
In a load-balanced environment, you can install the certificate on the load balancer itself, and it will manage the encryption for all the backend servers. This is known as SSL termination. The load balancer decrypts incoming traffic and forwards it to the servers, reducing the SSL handshake load on each individual server.
How one TLS/SSL Certificate can be installed on Multiple Servers?
-
Start with saving the certificate on the same server that generated the CSR. This guarantees certificate linkage with its original private key.
Safely export the certificate and its private key with caution.
Use OpenSSL to export and convert the certificate into an encrypted PKCS#12 (PFX) file using a password. This protects the private key during the transfer. Securely transport the PFX file to other servers, preferably using encryption tools like SSH or SCP. Do not use insecure ways like email or other non-encrypted file transfer methods.
Import the PFX file to the new servers. Follow the installation process specific to the server type (e.g., IIS for Windows or OpenSSL for Linux).
If a different format is required for the target server than the source server, request that the CA issue suitable copies of the certificate. This allows you to perform a seamless installation while upholding security measures.
Lastly, after the installation, delete the PFX file from that server to prevent it from being accessed without proper permission. It is also wise to keep private keys dormant and protected at all times.
Important Aspects to note while Installing a Single SSL Certificate on Multiple Servers
- Stay Coordinated with Your Certificate Authority (CA)
- Check for Compliance: Regularly check your CA’s policies to make sure you are following their rules and to find out if there is any limitation on the usage of a single certificate. Some Certificate Authorities have rules on where you can use your certificate. So, it is worth checking these to stay compliant. Some common CA policies or restrictions include domain/subdomain usage limits, private key handling and storage rules, geographic restrictions, and compliance with industry standards (e.g., PCI DSS, HIPAA).
- Automating Certificate Deployment
- Save Time with Automation: The wonderful thing about automation tools is that they make it super easy to deploy and renew certificates across servers, thus saving your time and manual effort and reducing the risk of expired certificates.
- Moving Certificates Across Servers Safely
- Exporting your Certificate and its Private Key: Assuming that you would need to use the same certificate on multiple servers, you would need to export it from one server and import it to the other server afterward. It is important to keep the private key secure, therefore limiting access, storing keys securely in Hardware Security Module (HSMs), and monitoring usage to prevent unauthorized access.
- Smart Ways to Use a Single Certificate
- For Multi-Domain Setups:When handling multiple domains, SAN certificates can be useful. A SAN certificate allows one certificate to secure multiple domains or subdomains, simplifying SSL management by covering various websites or services, such as www.example.com and blog.example.com, with just one certificate.
- For load-balanced systems: Think of load balancers as traffic controllers, using the same certificate across all the servers to keep things running smoothly and provide seamless operations.
- Watch Out for Security Risks
- Centralized Management: Managing certificates from a single place makes it easier to keep things up to date. However, this convenience comes with a downside: having a single central system means there is also a single point where security could be vulnerable. If one server’s security is breached, it might put the entire setup at risk. To keep things extra secure, think about using Hardware Security Modules (HSMs) to protect your keys and add an extra layer of protection like multi-factor authentication (MFA) for accessing certificate management systems and network segmentation to limit access to trusted devices and personnel.
- Risk of Compromise: Using the same certificate on multiple servers can create vulnerabilities. If one server’s security is breached, it can affect the other servers sharing that certificate. Therefore, in some cases, it is better to have the private keys of each server on separate certificates or to segregate the private keys entirely.
How can Encryption Consulting help?
Encryption Consulting can enhance your certificate provisioning process through an all-in-one solution, CertSecure Manager, designed to oversee the complete lifecycle of certificates. From the stages of request and issuance to deployment, renewal, and revocation, it assures that your certificates remain current and are securely implemented across servers and domains. We also help in managing multi-server configurations, offering specialized advice on utilizing wildcard and SAN certificates and applying best practices for securing private keys. Our offerings guarantee adherence to industry standards, reduce security threats, and streamline the entire process, assisting you in upholding a secure and encrypted connection for your users.
Conclusion
In today’s digital world, certificates play a crucial role in ensuring confidentiality and protecting data. The lock icon in your browser represents the trust and safety that users expect when interacting online. Knowing how to manage, download, and install certificates is key to safeguarding both your own information and that of your users.
Securing private keys is crucial since they permit the decryption of encrypted information, and if they are exposed, they can lead to unauthorized access, compromising the security of your communication channel. By protecting private keys, we maintain the integrity of SSL/TLS encryption, guaranteeing secure and reliable online interactions. Ultimately, digital security is vital, and understanding how to manage certificates is an important skill in creating a secure online environment.
- What is Certificate Provisioning?
- The Importance of Certificate Provisioning in Cybersecurity
- A Simple Guide on Downloading Your Certificate Files from CA
- Downloading the SSL Certificate in Windows using the Chrome Browser
- One Certificate, Many Servers: Is It Possible?
- How one TLS/SSL Certificate can be installed on Multiple Servers?
- Important Aspects to note while Installing a Single SSL Certificate on Multiple Servers
- How can Encryption Consulting help?
- Conclusion

