Often in the cybersecurity field, encryption algorithms are broken or deemed to be too weak, and so the industry standards shift to a new algorithm. This switch can damage existing hardware that previously relied upon the deprecated encryption algorithm, unless that security system is cryptographically agile. Cryptographic agility refers to the ability of security hardware to change to a new algorithm, as per industry standards, without the need to rewrite applications or deploy new hardware systems.
Crypto-agility comes about when an infrastructure has such complete control over their cryptographic operations that a change to those operations will not impact the day to day functions of the hardware in any way. As time has gone on, computer systems have become more complicated, as have encryption algorithms and attackers methods of attacks, in turn. Since attackers are learning to break algorithms, new ones must be devised regularly. Thus, crypto-agility has become a necessity with newly developed hardware systems.
Crypto-agility offers a multitude of benefits, including reduced downtime and costs from seamless algorithm transitions, enhanced future-proofing by adapting to evolving threats, incorporating new algorithms, and improved compliance with industry standards and regulations, ultimately mitigating legal risks.
Why is Crypto-Agility Important?
As previously mentioned, attackers breaking encryption algorithms is one of the main reasons those algorithms are replaced. Attackers are discovering new ways to crack secure algorithms used every day. In 2018, the National Institute of Science and Technology (NIST) released a guideline that brought attention to the fact that the Sweet32 vulnerability was used to make the encryption algorithm 3DES insecure. 3DES is used in the financial sector by most companies, so changing from 3DES to a new encryption algorithm could break the hardware used in the financial sector, if it is not cryptographically agile. As time goes on, vulnerabilities are bound to be found in all types of encryption, so crypto-agility will continue to grow in most organization’s hardware devices.
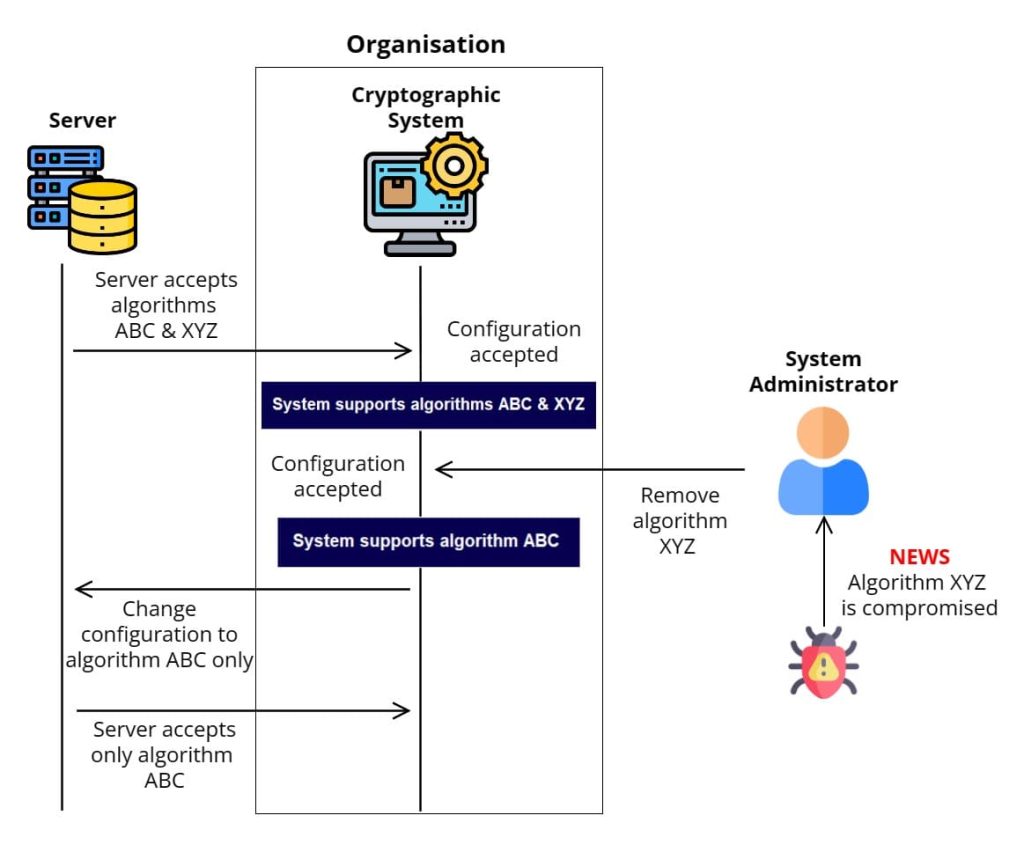
Another reason to ensure an IT infrastructure is cryptographically agile is because of the emergence of quantum computing. Quantum computing is an emerging side of computer science that is being more and more heavily researched each year, as quantum computing has the potential to be able to render all classical computing cryptosystems useless. Quantum computing will continue to grow for the foreseeable future, and so certain crypto-agility techniques must be implemented. Future computing systems will need to be able switch between multiple encryption algorithms, as opposed to just one, to combat quantum computing.
While crypto-agility offers significant benefits, implementing it can come with costs associated with system upgrades, testing, and training. Organizations should carefully evaluate the cost-benefit trade-off before adopting crypto-agile solutions. Also, educating users about the importance of crypto-agility and secure password management practices forms a critical layer of defense alongside cryptographic mechanisms.
How to achieve and maintain Crypto-Agility?
The most important part of creating cryptographically agile hardware systems is by planning for it at the beginning. When the designs for your security systems are initially made, ensure that crypto-agility is one of the main requirements. This will ensure that the cryptographic agility of the hardware is being monitored at all times. With existing systems, there is software that exists that can implement crypto-agility, as recreating the systems from the bottom up is not feasible.
Another method to achieve crypto-agility is by implementing policies that tell employees the proper procedures to follow to reach and maintain crypto-agility. These policies should be detailed, but not too technical, to allow employees from any sector to be able to understand the policies. The policies should also be clear and enforce the use of the most up-to-date cryptography methods. Everyone within the organization should be trained in the use of all policies, especially crypto-agility related ones. These policies should be where the role-based access controls are discussed as well.
IT security teams should train the different sectors of the company on the responsibilities of that sector to help reach the goal of crypto-agility. The sector responsibilities for all parts of the organization should include maintaining an accurate inventory of crypto assets, noting the current access level of each member of the sector, and keeping track of who owns what data. This will assist IT security team members in maintaining crypto-agility throughout the organization.
Public Key Infrastructures (PKIs) are another great method to attaining crypto-agility. A PKI deals with the management of certificates and keys, and automates the replacement, creation, and rotation of keys and certificates. This removes the issue of human error from the management of keys and certificates. You also gain control over the Chain of Trust and Certificate Authorities (CAs) utilized in the PKI, gaining your organization the ability to have even more control over the encryption of data.
The following best practices will help reinforce the methods used to attain crypto-agility:
- Automate management and tracking (e.g., key rotation, certificate lifecycle management, algorithm updates) across all sectors to maintain strong visibility. This includes visibility into supported cryptographic algorithms, dependencies, and user usage throughout the organization.
- Identify and fix vulnerabilities before data can be stolen or compromised.
- Update with the latest security patches for hardware and software regularly to remain protected against evolving threats.
- Ensure the ability to test and seamlessly replace current encryption algorithms with newly created, industry-standard options. This includes implementing robust testing procedures and compatibility assessments.
- Supplement RSA implementations with Elliptical Curve Cryptography (ECC) wherever possible for added security and efficiency.
- Use high key lengths (e.g., >256 bits) for symmetric ciphers and large bit sizes for hash algorithms to enhance security.
- Avoid hard-coding of cryptography into applications or algorithms to maintain flexibility for future updates and advancements.

