Introduction
Cryptography is the study of securing communications from outside observers. Encryption algorithms take the original message, or plaintext, and converts it into ciphertext, which is not understandable. The key allows the user to decrypt the message, thus ensuring on they can read the message. The strength of the randomness of an encryption is also studied, which makes it harder for anyone to guess the key or input of the algorithm. Cryptography is how we can achieve more secure and robust connections to elevate our privacy. Advancements in cryptography makes it harder to break encryptions so that encrypted files, folders, or network connections are only accessible to authorized users.
Cryptography focuses on four different objectives:
-
Confidentiality
Confidentiality ensures that only the intended recipient can decrypt the message and read its contents.
-
Non-repudiation
Non-repudiation means the sender of the message cannot backtrack in the future and deny their reasons for sending or creating the message.
-
Integrity
Integrity focuses on the ability to be certain that the information contained within the message cannot be modified while in storage or transit.
-
Authenticity
Authenticity ensures the sender and recipient can verify each other’s identities and the destination of the message.
These objectives help ensure a secure and authentic transfer of information.
History of Cryptography
Cryptography began with ciphers, the first of which was the Caesar Cipher. Ciphers were a lot easier to unravel compared to modern cryptographic algorithms, but they both used keys and plaintext. Though simple, ciphers from the past were the earliest forms of encryption. Today’s algorithms and cryptosystems are much more advanced. They use multiple rounds of ciphers and encrypting the ciphertext of messages to ensure the most secure transit and storage of data. There are also methods of cryptography used now that are irreversible, maintaining the security of the message forever.
The reason for more advanced cryptography methods is due to the need for data to be protected more and more securely. Most of the ciphers and algorithms used in the early days of cryptography have been deciphered, making them useless for data protection. Today’s algorithms can be deciphered, but it would require years and sometimes decades to decipher the meaning of just one message. Thus, the race to create newer and more advanced cryptography techniques continues.
What are Various Types of Ciphers?
Ciphers are algorithms used for encryption and decryption of data. They can be broadly categorized into several types based on their structure and method of operation. The various types of cipher include Substitution Cipher, in which each letter in plaintext is replaced with another letter; Transposition Cipher, in which the positions of the letters in the plaintext are shifted according to a certain system, Stream Ciphers, which encrypts plain text one bit or byte at a time by using a keystream generated from a secret key, Block Ciphers, which encrypts the data in fixed-sized blocks, Public Key Ciphers, which used a pair of keys (public and private).
Types of Cryptography
Cryptography can be broken down into three different types, which encompass various types of encryption and types of ciphers:
- Secret Key Cryptography
- Public Key Cryptography
- Hash Functions
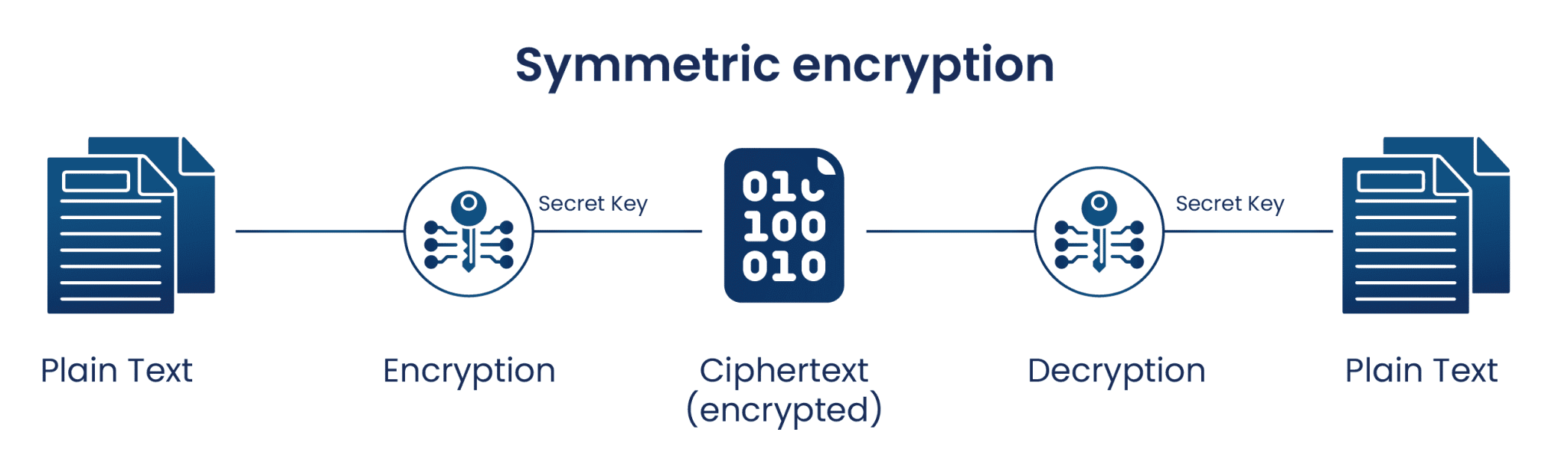
Secret Key Cryptography, or symmetric cryptography, uses a single key to encrypt data. Both encryption and decryption in symmetric cryptography use the same key, making this the easiest form of cryptography. The cryptographic algorithm utilizes the key in a cipher to encrypt the data, and when the data must be accessed again, a person entrusted with the secret key can decrypt the data. Secret Key Cryptography can be used on both in-transit and at-rest data, but is commonly only used on at-rest data, as sending the secret to the recipient of the message can lead to compromise.
Examples:
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard) [Deprecated]
- Caesar Cipher
Public Key Cryptography, or asymmetric cryptography, uses two keys to encrypt data. One is used for encryption, while the other key can decrypts the message. Unlike symmetric cryptography, if one key is used to encrypt, that same key cannot decrypt the message, rather the other key shall be used.
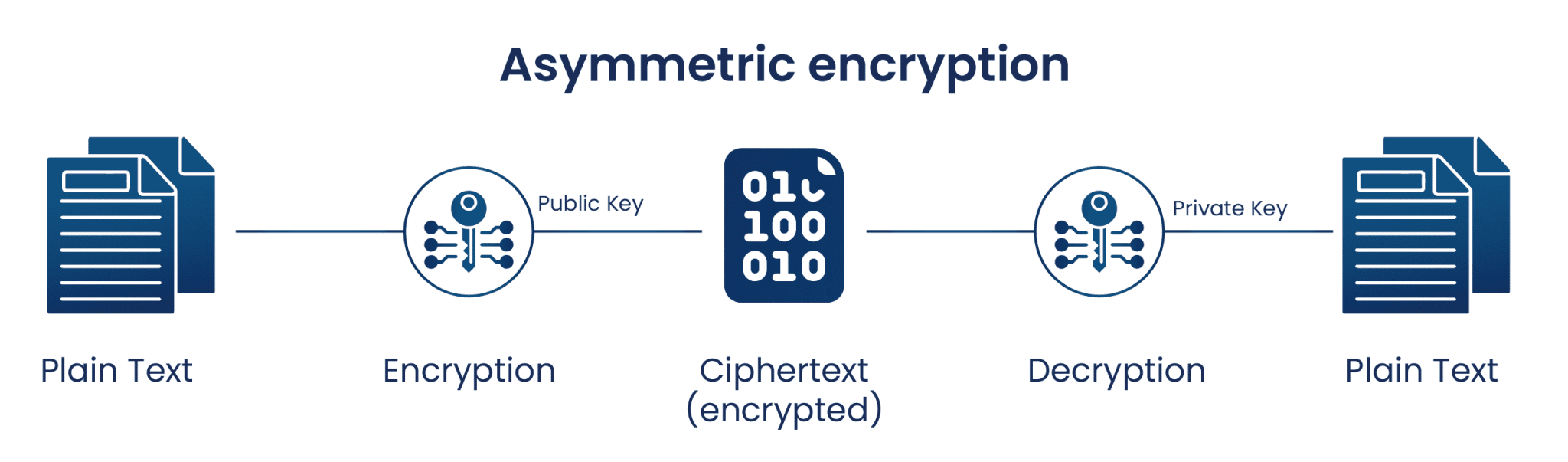
One key is kept private, and is called the “private key”, while the other is shared publicly and can be used by anyone, hence it is known as the “public key”. The mathematical relation of the keys is such that the private key cannot be derived from the public key, but the public key can be derived from the private. The private key should not be distributed and should remain with the owner only. The public key can be given to any other entity.
Examples:
- ECC (Elliptic Curve Cryptography)
- Diffie-Hellman
- DSS (Digital Signature Standard)
Hash functions are irreversible, one-way functions which protect the data, at the cost of not being able to recover the original message. Hashing is a way to transform a given string into a fixed length string. A good hashing algorithm will produce unique outputs for each input given. The only way to crack a hash is by trying every input possible, until you get the exact same hash. A hash can be used for hashing data (such as passwords) and in certificates.
Some of the most famous hashing algorithms are:
- MD5
- SHA-1 [Deprecated]
- SHA-2 family which includes SHA-224, SHA-256, SHA-384, and SHA-512
- SHA-3
- Whirlpool
- Blake 2
- Blake 3
Understanding how cryptography works involves recognizing the importance of these different types of encryptions and the underlying crypto algorithms that enable secure communication. Each type of encryption serves specific purposes and employs various types of ciphers to ensure data confidentiality and integrity.
Conclusion
Cryptography plays an important role in modern digital security, striving to achieve confidentiality, integrity, authenticity, and non-repudiation in communication. Evolving from ancient ciphers to complex algorithms, it safeguards data in transit and at rest. The advent of tailored encryption services underscores the growing importance of robust cryptographic solutions in safeguarding sensitive information.
With a strong focus on Encryption Advisory services and decades of consulting expertise, Encryption Consulting offers a range of cryptographic solutions. Among these, PKI as a Service (PKIaaS) stands out, providing round-the-clock support to clients for any issues related to their PKI environment. This comprehensive approach enhances security, ensuring organizations remain resilient against potential misconfigurations in their encryption setups.

