Format Preserving Encryption, or FPE, is an encryption algorithm which preserves the format of the information while it is being encrypted. FPE is weaker than standard Advanced Encryption Standard (AES), but FPE can preserve the length of the data as well as its format. FPE works with existing databases to encrypt data while keeping it in the same format, encrypting data while not harming the function of existing applications.
Format Preserving Encryption (FPE)
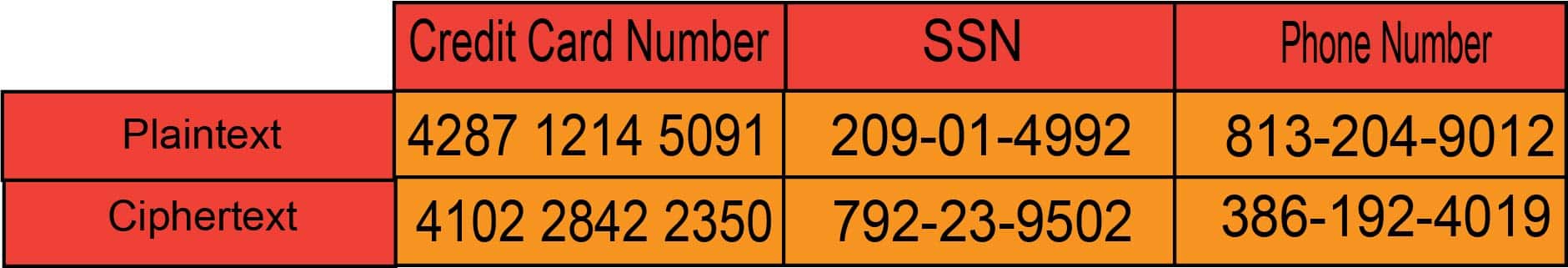
FPE encrypts takes plaintext and converts it to ciphertext, of the same format. An example of this is seen above. By keeping the format the same, an application can do operations on data as if it were the plaintext, while not revealing the sensitive information encrypted. Personally Identifiable Information (PII), credit card information, social security numbers, and other sensitive data are normally encrypted with Format Preserving Encryption. FPE has three different modes of operation: FF1, FF2, and FF3, which are referred to as FFX as a whole.
All three of the operation methods utilize the AES block cipher within their encryption. The second mode, FF2, was created but never approved by the National Institute of Standards and Technology (NIST). Instead, FF1 and FF3 were approved. FF1 is the most commonly used version, because of a cryptanalytic attack performed on the FF3 method which showed it held flaws. This attack found that the proposed 128-bit level of security was not reached. In response, a method called FF3-1 was created in early 2019 which addressed these issues.
FPE works extremely well with existing applications as well as new applications. If an application needed data of a certain length and format, then FPE could be applied to the data to encrypt it while not necessitating the changing of the application. This works particularly well with software that cannot handle long strings of data. Format Preserving Encryption is a valid encryption algorithm to be used for compliance with NIST standards. An NIST publication, called NIST 800-38G, was created to address FPE. This NIST publication focuses on the three methods of Format Preserving Encryption, describing the technical details of each mode of operation.
FPE on the Cloud
Many vendors offer FPE with their services, including Comforte, HashiCorp, Futurex and Xmart Solutions. Some cloud service providers (CSPs) offer options to utilize FPE within their platform, but far fewer than regular vendors. Of the three biggest CSPs, Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP), only GCP offers users the ability to work with Format Preserving Encryption.
Using FFX, Google Cloud Platform allows users to have access to FF1 and FF3 FPE methods, though FF1 is the more commonly used method. FFX uses multiple rounds of a Feistel function on the plaintext, along with a key, to create the ciphertext. A Feistel function splits the plaintext into two parts, permutates the text to change what it looks like, and then swaps the left half of text to the right and vice versa. The FF1 method uses 10 rounds of a Feistel function, and FF3 uses 8 rounds.
For a user utilizing the Data Loss Prevention (DLP) API in GCP, to encrypt with FFX, an alphabet to be used to encrypt the plaintext must be specified. This can be done by using a shortened name of one of the four most common alphabet types. NUMERIC specifies numbers 0-9, HEXADECIMAL includes the NUMERIC alphabet along with A-F, UPPER_CASE_ALPHA_NUMERIC is for 0-9 and A-Z, and ALPHA_NUMERIC specifies 0-9, A-Z and a-z. Users can also use a radix value specifying the size of the alphabet. Specifying 2 gives an alphabet consisting of the numbers 0 and 1, while specifying 95 gives an alphabet with all numeric, upper-case alpha, lower-case alpha, and symbol characters. The last way to specify the alphabet is by providing the exact numbers, symbols, and letters that are in the alphabet.
Encrypting with FPE on GCP can result in an image like the previous image, or a surrogate annotation may precede the ciphertext, if the data is unstructured. A ciphertext with a surrogate annotation will follow this format:
SURROGATE_INFOTYPE(SURROGATE_LENGTH): SURROGATE_VALUE
The surrogate_infotype is chosen by the user and can be any word. The surrogate_length tells how long the surrogate_value is, and the surrogate_value is the ciphertext itself. An example of ciphertext with a surrogate annotation is:
FaKeInFoTyPe(13): 182-123-3596
FPE with Encryption Consulting
Encryption Consulting offers blogs providing information for any organization or user wanting to learn more about FPE. We also provide resources that utilize Google Cloud Platform’s FPE options. Bucket Protector and Cloud Data Protector both work with the DLP and Key Management Services (KMS) APIs to encrypt data being sent to Google Cloud Storage or data on an organization’s local database with FPE. Bucket Protector and Cloud Data Protector fall under the Cloud Data Lake Protection services offered by Encryption Consulting, protecting data at the Data Storage and Data Ingestion phases of the Cloud Data Lake Lifecycle.

