- Why do we use PKI?
- What are the encryptions used in PKI?
- What are Digital Certificates? What is its role?
- What is X.509 Standard?
- What does PKI consist of? Where are the certificates created and stored?
- What is a Certification Authority?
- What are CRLs?
- What is a Delta CRL?
- What is an ARL?
- What is OCSP?
- Trusted Root Certificates
- What is a two-tier Architecture in PKI?
- What is a three-tier Architecture in PKI?
- Implementation of PKI
- Encryption Consulting - PKI Advisory Services
- Conclusion
Public Key Infrastructure (PKI) is a solution where, instead of using Email ID and Password for authentication, certificates are used. PKI also encrypts communication, using asymmetric encryption, which uses Public and Private Keys. PKI deals with managing the certificates and keys and creates a highly secure environment that can also be used by users, applications, and other devices. PKI uses X.509 certificates and Public Keys, where the key is used for end-to-end encrypted communication, so that both parties can trust each other and test their authenticity.
PKI is mostly used in TLS/SSL to secure connections between the user and the server, while the user tests the server’s authenticity to make sure it’s not spoofed. SSL certificates can also be used to authenticate IoT devices.
Why do we use PKI?
PKI offers a way to identify people, devices, and apps, while providing robust encryption so that communication between both parties can remain private. Besides authentication and identification, PKI provides digital signatures and certificates to create unique credentials for the certificate holder and to validate the certificate holder.
PKI is used all over the Internet in the form of TLS/SSL. When a client (in this case, a web browser) communicates with a server, the client gets ahold of the certificate and validates it to ensure its authenticity. Next, it employs asymmetric encryption to encrypt the traffic to and from the server. The digital certificate contains information such as the validity period of the certificate, issuer of the certificate, certificate holder, public key, signature algorithm, etc.
It also contains a certification path. A certification path is an ordered list consisting of the issuer’s public key certificate and more, if applicable.
A certification path must be validated before it can be relied upon to establish trust in a subject’s public key. Validation can consist of various checks on the certification path’s certificates, such as verifying the signatures and checking that each certificate has not been revoked. The PKIX standards define an algorithm for validating certification paths consisting of X.509 certificates.
Apart from being used as SSL over the internet, PKI is also used in digital signatures and sign software. PKI is also being used in smart devices, phones, tablets, game consoles, passports, mobile banking, etc. To overcome compliance challenges and follow all regulations and maintain security at its best, organizations are using PKI in more than a few ways to keep all things secure.
What are the encryptions used in PKI?
PKI makes use of both symmetric and asymmetric encryption to keep all its assets secure.
Asymmetric Encryption
Asymmetric encryption or Public Key Cryptography uses two separate keys for encryption and decryption. One of them is known as a public key, and the other is a private key. The public key can be generated from the Private key, but the Private key cannot be generated from the Public key. The private key and vice versa can only decrypt encryption done by the public key. Together, these keys are called “Public and Private Key Pair”.
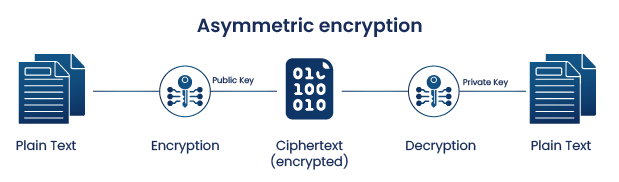
Asymmetric encryption offers a way to encrypt data in public channels by distributing the public key. As it doesn’t require exchange of secret keys thus we don’t face the key distribution issue that we generally do in symmetric encryption.
These keys use a high level of randomness to ensure enhanced security. Algorithms like RSA, EDSCA, DSA, and Diffie-Hellman, with a key size of 1024 to 2048 or more, are typically used. Generally, the longer the key size, the more secure the encryption method. For context, if 2048-bit encryption is used to generate the key, then there are about 2^2048 combinations possible. It would take hundreds of years to go through these many combinations.
Now, because the keys are longer and there is always a need to generate two different keys for encryption and decryption, this process becomes time consuming. Moreover, here we also use more complex algorithms. These are some of the many reasons why the Asymmetric encryption is slower as compared to symmetric encryption.
In SSL certificates used for encrypted communication between a client and a server, a public key is attached to the certificate, which will initiate secure communication between two parties.
Asymmetric encryption is used to exchange a secret key, which is done during the initial handshake between the two parties.
The secret key exchanged is used to establish symmetric encryption for further communication. Symmetric encryption is faster than asymmetric one, so the combination of them both provides robust end-to-end security.
Symmetric Encryption
Symmetric encryption, unlike Asymmetric encryption, uses only one key for both encryption and decryption. This shared key is crucial for secure communication, but securely exchanging it between the communicating parties presents a notable challenge in symmetric encryption, commonly known as the “key distribution problem.” To address this, various techniques have been developed, such as key derivation functions and trusted third-party key distribution centers.

Now, both the entities that are communicating via symmetric encryption (sender and receiver) should exchange the key so that it is used at the time of decryption. Here, the data is encrypted in a seemingly random and unintelligible form (ciphertext) and can only be recovered to the original form by the secret key.
Symmetric encryption is the most widely used type of encryption, and it is commonly used in applications such as email, file sharing, and virtual private networks (VPNs). Some examples of symmetric encryption include AES (Advanced Encryption Standard) , DES(Data Encryption Standard) , RC4(Rivet Cipher 4). Though this is faster than asymmetric encryption, but if the key is compromised, anyone can decrypt the contents encrypted. Therefore, asymmetric encryption is used to ensure the secret key is not compromised, and the connection remains secure.
Now as we know the use case of both of these encryptions depends on the advantages they bring to the table. In the cases where speed is the priority over increased security, we use symmetric encryption. Some of the most common cases include:
-
Banking
In Payment applications, sensitive user data like account number or partial credit card info needs to be encrypted so that it is protected from malicious actors. This helps to reduce the risk of daily transactions without compromising the speed of transactions.
-
Data Storage
Encrypting data that is at rest i.e, when storing large amounts of sensitive data companies prefer to encrypt the entire storage medium.
In the cases where advanced security is of priority over speed or there is a need for identity verification, we use asymmetric keys
-
Digital Signatures
They maintain the authenticity and integrity of the data being transferred. Moreover, they are of use in email, data interchange, etc.
-
Public key infrastructure (PKI)
Using asymmetric keys for issuance and management of digital certificates.
Now there are also several cases where Symmetric and Asymmetric encryption is used together, messaging apps and SSL certificates use a combination of both these encryptions.
Messaging apps like whatsapp use this to achieve end to end encryption. Asymmetric encryption on one hand establishes a secure channel initially, with users’ public keys stored on the server and private keys remaining on their personal devices. This allows secure exchange of a session key, which on the other hand is then used for efficient symmetric encryption of the actual message.
SSL certificates use asymmetric encryption to authenticate the server and establish a secure channel for exchanging a session key. This session key then uses symmetric encryption for the website data you access. In both scenarios, both encryption methods are utilized efficiently: asymmetric for secure key exchange and initial setup, and symmetric for efficient data encryption during actual communication.
What are Digital Certificates? What is its role?
Digital certificates are widely used in PKI. A digital certificate is a unique form of identification for a person, device, server, website, and other applications. Digital certificates are used for authentication as well as validating the authenticity of an entity. It also makes it possible for two machines to establish encrypted communication and trust each other without the fear of being spoofed. It also helps in verification, which allows in the Payment Industry, which allows e-commerce to grow and be trusted.
The certificate can be of two types.
- Self-signed certificate Users can create their certificates, which can be used for internal communication between two trusted parties.
- Signed by Certification Authority A Certification Authority issues a certificate which can be used for TLS/SSL on the website. Customers can validate the certificate from the third-party issuer, which would validate the server’s authenticity.
Before a Certification Authority issues a certificate, the issuer makes sure that it is given to the right entity. Several checks are made, such as if they are the domain name holders, etc. The certificate is issued only after the checks are complete.
What is X.509 Standard?
Most public certificates use a standard, machine-readable certificate format for certificate documents. It was initially called X.509v3. The format is used in many ways, such as
- Internet Protocols (TLS/SSL, which makes secure HTTP connections)
- Digital Signatures
- Digital Certificates
- Certificate Revocation Lists (CRLs)
What does PKI consist of? Where are the certificates created and stored?
PKI or Public Key Infrastructure use multiple elements in their infrastructure to ensure the security it promises. PKI uses digital certificates to maintain and validate people, devices, and software accessing the infrastructure. Certification Authority or CA issues these certificates. A Certification Authority issues and validates certificates issued to a user, device, software, a server, or another CA. CA ensures the certificates are valid and also revokes certificates and maintain their lifecycle.
What is a Certification Authority?
Certification Authority certifies the identity of the requestor. The requestor can be a user, application, etc. Depending upon the type of CA, security policies, and requirements for handling requests, the identification mode is determined.
While setting up, a certificate template is being chosen, and the certificate is issued based on the given information upon request. CA also release revoked lists called CRLs, which ensure invalid or unauthorized certificates cannot be used anymore.
Root CA is a trusted certificate authority, has the highest hierarchy level, and serves as a trust anchor. While validating a certificate path, the root certificate is the last certificate that is checked. For the most part, Root CA remains offline and should stay air-gapped to make sure it is never compromised. Root CA signs certificate for issuing CA and other subordinate CA, which is used around the network. If an issuing CA fails, another can be created, but if a Root CA fails or gets compromised, the whole network needs to be recreated.
Subordinate CA is under Root CA but is above endpoints. They help in issuing certificates, managing policies, etc. Their main objective is to define and authorize types of certificates that can be requested from root CA. Example: Subordinate CA may differ by location, or one CA may handle RSA keys, and the other may handle ECC keys.
Who decides if CA can be trusted?
Trust in CAs is established through membership programs where each CA must meet strict criteria and protocols to be accepted as a member. Browsers and Operating Systems have a limited set of approved CAs. They must follow strict guidelines and security practices to ensure the integrity and trustworthiness of the certificates they issue.
For example, a Domain Validated (DV) SSL Certificate confirms domain ownership, while an Extended Validation (EV) SSL certificate goes further. EV certificates involve thorough company checks by the CA, resulting in additional information displayed in the browser bar, like the company name. This extra verification adds to the trustworthiness of the website and the issuing CA.
Process of certificate creation
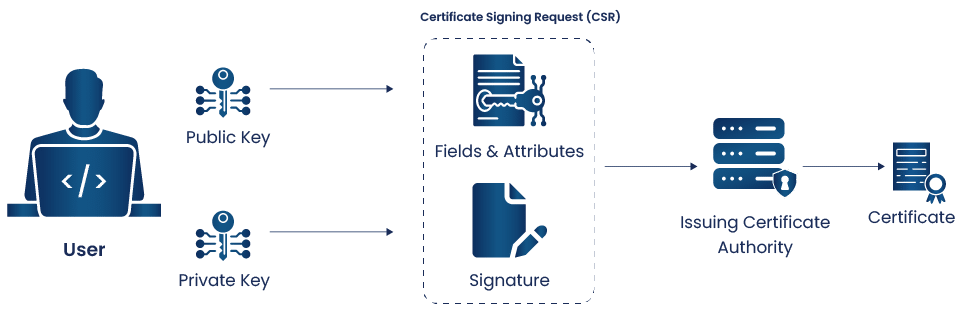
Step 1: Key Generation
This is done by the user. The public key is sent to the registration auth and private key is held by the user.
Step 2: Create a CSR
Using a private key we generate a CSR which includes the public key and necessary details required for certificate like domain and organization information.
Step 3: Submit to CA
The CSR is then submitted to a trusted CA for certificate issuance.
Step 4: CA verification
Upon receiving the certificate CA starts the verification process before granting the certificate i.e., based on the type of requested certificate type ( Domain Validated, organization validated,etc.)
Step 5: Certificate Issuance
After the process of verification a corresponding certificate is issued.
What are CRLs?
Certificate Revocation Lists is a list of all digital certificates that have been revoked. A certification authority populates CRLs as CA is the only entity to revoke certificates that it issues.
Without a Revocation list, it is harder to enquire if a certificate has been revoked or not before it’s expiration period. The revocation list is similar to a list of unauthorized entities.
A certificate can expire due to the end of the lifecycle of the certificate. While the certificate is created, it is also set for how long the certificate would remain valid.
If, however, within that time frame, if the key is compromised, or the user resigns, or for more such reasons, the certificate is revoked, so it can’t be used to get access. The certificate would be flagged as unauthorized and then cannot be used by someone else.
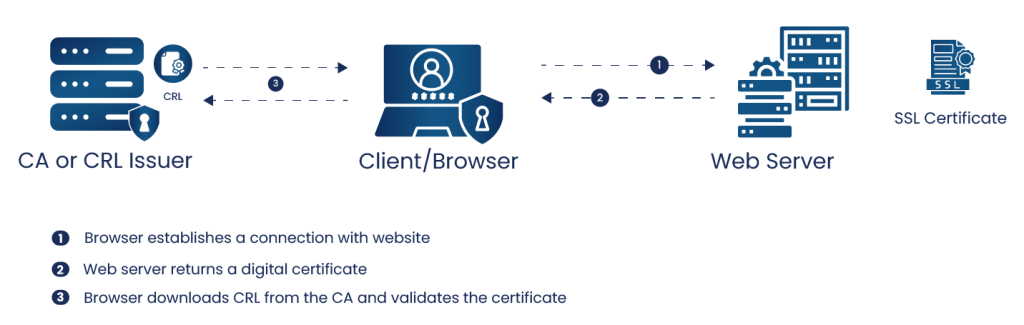
Moreover, these CRLs act as a checkpoint within the PKI infrastructure. When our browser establishes a connection with a website that we visit, it validates the digital certificate issued by the website. These certificates contain one or more links which the browser can access to retrieve CRL. Depending on the response, the browser will either consider the certificate as trustworthy or alert us about the revoked certificate.
Thus, in this whole process CRL functions as a blacklist, containing information on certificates that have been revoked before their expiry date due to security compromises or other issues.
What is a Delta CRL?
In a large organization, CRLs can grow to be quite massive. Since a certificate must remain in CRL until it expires, they can stay on for several years. To transfer the whole CRL from one server to another can take a while. To make this process quicker, CA, delta CRL, is issued, which only includes the changes made since the last CRL update. This makes the transfer much shorter and updating of CRLs much quicker.
What is an ARL?
Authority Revocation List is a derivation of CRL. It contains revoked certificates issued to Certificate Authorities rather than users, software, or other clients. ARL is only used to manage a chain of trust.
What is OCSP?
Online Certificate Standard Protocol described in RFC 6960 is used to confirm a digital certificate’s revocation status. OCSP is a simpler and faster way to check revocation than CRLs since CA’s checks are performed instead of PKI. The data transferred is less, which helps the CA to parse the data.
However, OCSP is less secure than CRLs. Reasons include:
- OCSP is less informative. The only information CA sends back is either “good”, “bad” or “unknown”.
- OCSP does not have requirements for encryption.
- Possible where a “good” response can be captured, and replaying back to another OCSP request is possible.
Trusted Root Certificates
Trusted certificates establish a chain of trust that verifies other certificates signed by the trusted roots. They are primarily the top-level certificates in the hierarchy of certificates. When we visit a secure website (using HTTPS), our browser checks the website’s SSL/TLS certificate against a list of trusted root certificates stored locally. If the certificate presented by the website is signed by one of these trusted root certificates, the connection is deemed secure and encrypted.
One such example is Microsoft root certification Authority. This certificate is issued by Microsoft Corporation, and it is included in the trusted root certificate store of Windows operating systems and Microsoft products. It is used to establish trust for various Microsoft services, applications, and websites.
What is a two-tier Architecture in PKI?
A two-tier architecture is a layout that would meet the requirements for most organizations. The root CA lies on the first tier, which should remain offline and air-gapped. Subordinate Issuing CA should be online under it. Since we separate the role of Root CA and Issuing CA, the security does increase. The Root CA being offline protects its private keys better and reduces the chances of being compromised.
Two-tier architecture also increases scalability, flexibility and thus also increases fault tolerance. Since we separate the roles, multiple issuing CA can be created and placed under a load balancer. This also enables us to remember CA in different regions and to use different security levels depending upon the region. Manageability also increases as CAs are separate, and Root CA needs to be brought online only to sign CRLs.
Two Tier Architecture is the highly recommended design for most PKI solutions.
What is a three-tier Architecture in PKI?
Like two-tier architecture, three-tier also has an offline root CA on the top and online issuing CA on the bottom, but intermediate tier is now placed which holds CA which should remain offline. Intermediate CA may act as policy CA which dictates what policies to be followed while issuing a certificate. Any authenticated users can get a certificate, or the user may need to appear in person for certificate approval.
However, if an issuing CA face compromise or something similar, the second-level can revoke the certificates while keeping the rest of the branches alive.
Three-tier PKI does increase security, scalability, flexibility but comes with increased cost and manageability. If an organization does not implement administrative or policy boundaries, then the middle tier may remain unused, so three-tiers are not usually recommended or used.
Implementation of PKI
What are the Challenges solved by PKI?
-
Trust
PKI helps users confirm the validity of devices and websites. This ensures that users are connecting to the right website. Also, the communication between the user and the server remains encrypted. This removes the chances of being spoofed or a man-in-the-middle attack.PKI also help customers trust e-commerce website and make online payments securely. PKI ensures the authenticity of all parties involved and also encrypts communication between them, which allows them to grow a sense of trust.
-
Authentication
Passwords have been weak since people tend to share, write on a post-it, etc. PKI creates digital certificates that validate their identity, and since identity is validated, it works to authenticate users, devices, and applications.
-
Security
PKI does improve security, as when trust is increased and authentication is implemented, the only attack vector that remains is PKI itself. People tend to be the weakest links in security, and when PKI is implemented, users are not left with much control. PKI ensures all policies are maintained, security is in place, and digital certificates (in the form of smart cards) help ensure that users would not be using passwords or pin which can be easily compromised. The only variable remain would be PKI, which can be secured, thus protecting the network.
PKI for Internet
Browsing the internet is often done using HTTPS, a secure version of HTTP that is the primary way to visit websites. While we use HTTPS, our connection to the server is encrypted. To ensure we connect to the correct server, our browser initially accepts a certificate from the server. Then it validates the certificate and uses the public key in the certificate to establish a secure connection.
That certificate proves the server’s authenticity, increases security, encrypts the connection, and lets the user trust the website.
If the certificate is invalid or expired, the browser will notify the user not to trust the website and often may not even allow the user to visit that particular website. The browser may also stop the user from visiting sites that are not using HTTPS connections.
PKI for Authentication
PKI provides digital certificates that prove the authenticity of the user. Since the user is authentic, if the user is authorized, it acts to authenticate users onto an area using smart cards or onto the network. PKI extends far beyond just user authentication. It allows users and systems to verify their identity and communicate over the air like in the cases of certificate-based Wi-Fi authentication.PKI also.
Using those digital certificates can also authenticate other devices and servers to have access and privilege to the network. This can also include Intrusion Detection Devices or other network devices such as routers. PKI also plays a big role in VPN authentication. Moreover. as there is highly sensitive data that is accessed through VPN, certificates are considered the preferred method for authentication. Generally, the CA is stored on the firewall of the device and once the user is authenticated. A secure tunnel is created between both the communicating entities.
PKI for Communication
PKI can be used for communication, where both parties can check each other’s authenticity, which would lead them to trust each other’s identity and then also encrypt their conversation. This highly increases the security and trust among the parties participating in the communication. A prime example of PKI in communication is secure email. S/MIME (Secure/Multipurpose Internet Mail Extensions) uses digital certificates to encrypt emails. Both sender and recipient need a trusted CA-signed certificate. S/MIME utilizes these certificates to ensure authenticity of the sender and encrypt the email content that only the intended recipient can access using the public key.
PKI in IOT
Earth has more devices than people. In the US, there are 11 connected devices on average in each household. To be able to manage and to have enough IP for all the devices has been a challenge. In November 2019, Europe ran out of IPv4. For this reason, IPv6 came out in 2012 and is being in play ever since.
The number of devices is only bound to increase due to the boom in IoT. With increasing smart devices, it becomes a challenge to confirm these devices’ digital identity and provide proper network security.
PKI provides a way to assign digital certificates to smart devices and secure a connection to the server. This helps OEMs to track the smart devices, push updates, and monitor and even fix them if necessary. It also keeps IoT devices secure from any attack, which can be catastrophic as it can affect our homes and our personal space.
Encryption Consulting – PKI Advisory Services
Encryption Consulting with its top of the line consultants provide a vast array of PKI services for all customers. Our services include:
- PKI Assessment The assessment will identify gaps & provide recommendations as part of a comparative study of the current and future state of customer’s PKI. This study will provide customers with a valuable risk report, a roadmap to improvement, and a way to prioritize data security investments.
- PKI Design/Implementation Designing and implementing a successful PKI needs expertise. This is where we can help customers. To assist you in this, we design PKI and supporting processes. Post design, we help you with implementing/ migrating PKI technology and infrastructure, including the root & issuing CAs. We develop PKI policies, rules and operational processes in alignment with your business needs.
- PKI CP/CPS Development The CP and CPS documents describe the architecture of your specific PKI, and include sections on certificate uses, naming, identification, authentication, key generation, procedures, operational controls, technical controls, revocation lists, audits, assessments, and legal matters. Encryption Consulting will work collaboratively with customer stakeholders to develop a Certificate Policy (CP) / Certificate Practice Statement (CPS) document following the template provided in Request for Comment (RFC) #3647.
- PKI As A Service Encryption Consulting’s PKI As A Service offers you a customizable, high-assurance Microsoft PKI designed and built to the highest standards. It’s a low risk managed solution that gives you full control of your PKI without having to worry about the complexity.
- PKI Training Encryption Consulting offers PKI training for anyone using or managing certificates, designing, or deploying a PKI enterprise solution, or evaluating & selecting a commercial PKI Technology Solution
Conclusion
In conclusion, Public Key Infrastructure (PKI) remains the cornerstone of modern virtual security, providing authentication, encryption, and approving the necessary means of secure communication across domains If with asymmetric encryption, digital using robust certificates and verification processes, PKI ensures authenticity and authenticity of users, devices and packages.
Encryption Consulting provides comprehensive expertise and customized solutions. With a team of top experts, Encryption Consulting provides comprehensive PKI testing, design, implementation, and schooling services, ensuring that clients receive tailored answers that match their unique security desires.

