- Introduction
- Types of Symmetric Encryption Algorithms and their modes of operation
- Can Symmetric Encryption systems be hacked?
- NIST Recommendations for Securing Symmetric Encryption Keys
- Advantages of Symmetric Encryption
- Disadvantages of Symmetric Encryption
- Combining symmetric and asymmetric encryption
- Ensure compliance with cryptographic standards
- Use Cases
- Post-Quantum Cryptography and its Impact on Symmetric Algorithms
- Conclusion
With fast-paced technology advancements, cyberattacks are on the rise, making it easier for unauthorized access of sensitive data, whether it’s online banking, emails, social media, encryption has become essential to keep our sensitive data from prying eyes and malicious activities. But how exactly encryption works? Let’s dive in crucial topics and explore why encryption is more important than ever.
If encryption is not implemented properly, it poses security risks. To illustrate, let’s take a recent real-world example from the Group Health Cooperative of South-Central Wisconsin (GHC-SCW). In January 2024, hackers got unauthorized access to the organization’s network and attempted to encrypt the patient’s data and execute a ransomware attack. Even though the effort failed, yet they managed to get access to the database that stored patients’ sensitive information, containing their credentials, social security numbers, insurance details, etc., that compromised data belonging to over 5,30,000 individuals.
If strong symmetric encryption had been implemented, the sensitive data compromise could have been prevented. This is because even if the attackers had infiltrated the security perimeter, the data would have been in an unreadable form. This attack clearly demonstrates the extent to which all organizations are at risk when strong encryption is not employed on their data.
Introduction
In symmetric encryption, only one single secret key, also known as a symmetric key, is used to encrypt and decrypt information. A simple analogy would be locking up a zip file using a password for encryption while unlocking it for decryption. The secret key is known to both the sender and the recipient.
Working
A secret key shared exclusively between the sender and receiver is used to encrypt and decrypt data by employing a symmetric encryption algorithm. The data is first scrambled into ciphertext using a symmetric algorithm that makes the data not readable in any form while in transit. When the data reaches its destination, the receiver decrypts the ciphertext with the same key.
The formulas mentioned below represent how data is encrypted and decrypted:
ciphertext = encrypt(plaintext, key)
plaintext = decrypt(ciphertext, key)
Now, let us understand the role of generating the key pairs in symmetric encryption.
The Process of Key Generation
In symmetric encryption, the generation of private keys is a critical process that ensures they are generated in a manner that is both random and strong. Simple random number functions are not enough as they might show predictable patterns, which makes it easier for attackers to exploit the values. Therefore, attacker-proof methods like Cryptographically Secure Pseudorandom Number Generators (CSPRNGs) are used.
An example of such a generator is the Blum Blum Shub algorithm, which is used to eliminate all attacks based on patterns. To further enhance security, more sophisticated methods are applied, such as employing elliptic curves with secure hash algorithms in the generation of key pairs, ensuring the keys generated are unique and extremely difficult to guess. Such a strong key generation method will come in handy when encryption takes place for data since weak and predictable keys could be compromised, thus threatening their confidentiality and integrity.
There are two methods of encrypting data using symmetric encryption, as follows:
1. Block encryption
In this method, fixed-length blocks are encrypted, which are typically chunks of 128 bits. It transforms the individual plaintext blocks into their corresponding ciphertext blocks.
2. Stream encryption
In this method, data is encrypted one byte at a time while generating a continuous stream of pseudorandom bits for added security.
To learn more about block cipher and stream cipher, click here.
Types of Symmetric Encryption Algorithms and their modes of operation
The various types of symmetric encryption algorithms are designed to address particular security requirements. Furthermore, their modes of operation describe the way in which the data is encrypted and efficiently processed. Let’s explore them in detail.
1. The Data Encryption Standard (DES)
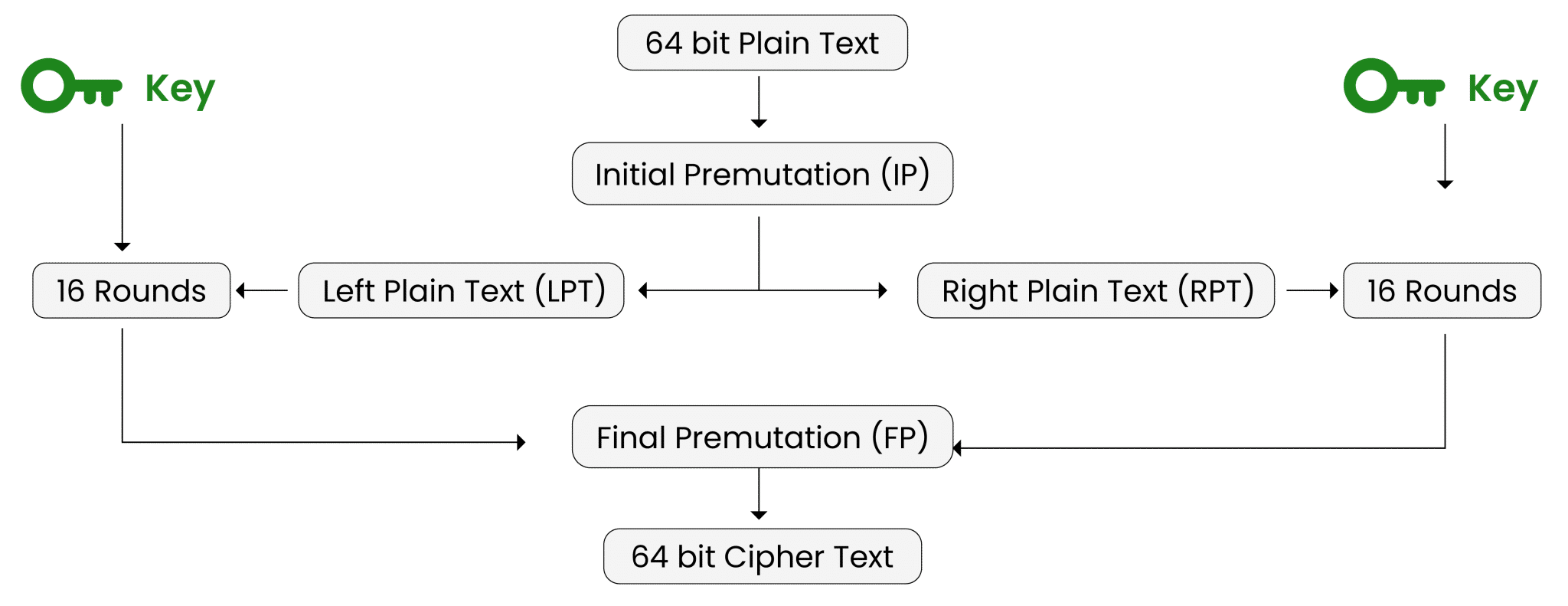
Developed by IBM in the 1970s and accepted by the National Institute of Standards and Technology (NIST) in 1977. It was widely adopted. It is a block cipher algorithm where the data is encrypted in 64-bit blocks using a key of 64 bits, whereas only 56 bits are used for the actual encryption and the rest 8 bits are reserved for parity to help detect errors. The encryption used in DES combines two cryptographic principles, substitution (confusion) and transposition (diffusion), to hide the relationship between a message’s plaintext, ciphertext, and key.
Now, let us break down the DES encryption process into three levels, each of which is a critical stage in transforming plaintext to ciphertext.
Level 1: Initial Permutation (IP) is applied to the 64-bit plaintext block initially, and transposition is performed on it using a fixed pattern. The Subsequent steps are the division of the plain text block into Left Plain Text (LPT) and Right Plain Text (RPT), i.e., two parts of 32 bits each.
Level 2: Each of these halves undergo 16 rounds of encryption. Each round consists of steps involving substitution and transposition. Now, the Right Plain Text (RPT) undergoes expansion to 48 bits and XORs it with a round-specific 48-bit subkey. After that, the results pass through substitution boxes and are compressed into 32 bits. Now, permutations are included and transferred to LPT, thereby creating an interaction for LPT and RPT.
Level 3: Now, LPT and RPT are recombined and given Final Permutation (FP). The output of this process is called the ciphertext, which is 64 bits and the encrypted version of the original plaintext.
However, due to advancements in computational power, brute-forcing the keys is a security vulnerability, and therefore, DES is no longer widely used.
2. Triple DES
It is also known as the successor of the DES algorithm. Its encryption process consists of three rounds, wherein three 56-bit unique keys (say K1, K2, and K3) are taken to encrypt the 64-bit plaintext with K1, then decrypting it with K2 and then again encrypting the above output with K3.
Triple DES provides significantly greater security than the DES algorithm. For further details, follow this link.
3. Blowfish
This algorithm is considered an alternative to the DES algorithm and uses a 64-bit block size as input with variable key size length (ranging from 32 bits to 448 bits), making it flexible for different security requirements.
The algorithm is based on the Fiestel structure for encryption and decryption, with 16 rounds providing higher security and greater speed than DES.
To learn more, click here.
4. Advanced Encryption Standard
It is the most widely used algorithm in today’s cyberspace and was published by the NIST with the intention of replacing DES with both software and hardware optimization for greater performance. It allows multiple rounds of encryption and decryption by using different key sizes: 128 bits, 196 bits, or 256 bits for 10,12 or 14 rounds, respectively, making it more secure.
The process involves multiple transformations, including four main steps- substitution, permutation, mixing, and key mixing.
To learn more, click here.
5. Twofish
Twofish structures the data in blocks of 128 bits and uses keys of 128-bit, 192-bit, and 256-bit size. Furthermore, it was designed to be highly secure through the combination of a substitution-permutation network (SPN) and very complex key schedules.
Usually, Twofish is used in applications requiring a high level of security as an alternative to AES in certain situations.
To learn more, click here.
6. RC4
Rivest Cipher 4 is a type of symmetric stream cipher that was designed by Ron Rivest in 1987. The basic operation of RC4 is that it generates a pseudorandom keystream, which is then XOR-ed with the plaintext to produce the ciphertext. While the key may range from 1 to 256 bytes, 128 bits is the common key size for RC4. It is fast and efficient and very well-known in many common protocols like WEP and SSL/TLS. Unfortunately, some of the vulnerabilities discovered over time in the key scheduling and biased keystream led to the deprecation of RC4.
To learn more, click here.
7. AES-CBC Cipher Suites
AES-CBC leverages the Advanced Encryption Standard (AES) algorithm in Cipher Block Chaining (CBC) to provide confidentiality. However, it does not guarantee message integrity or the necessary authentication. Therefore, an additional mechanism has been formulated and used with AES-CBC, such as HMAC (Hash-based Message Authentication Code), to account for authentication and integrity.
In CBC mode, each plaintext block is XORed with the ciphertext from the previous block before encryption. The first block is XORed with a random initialization vector to add variation. This makes the encryption more secure because identical plaintext blocks will produce different ciphertexts, preventing some types of attacks, such as pattern attacks.
The developers’ implementation of the AES-CBC-HMAC construction is not easy due to its complexity. The technique is usually difficult to handle, especially with the Initialization Vector (IV), which has been misused several times and might be prone to issues. To tackle these challenges, a well-organized process was introduced using a new authenticated encryption standard called Authenticated Encryption with Associated Data (AEAD), making it easier for developers to encrypt their works.
AEAD simplifies the complexity involved in authentication and encryption altogether into one entity. The authentication tag accompanies the ciphertext, wherein the tag is computed based on both the ciphertext data and the optionally provided additional data.
Therefore, this would allow a system to authenticate not just the ciphertext but also the accompanying data, providing one extra level of assurance regarding the integrity of all data sent.
The AES-GCM is the most popular and widely used AEAD mode. AES-GCM economically employs the Counter (CTR) mode of encryption and also applies multiplication in a Galois field for authentication, resulting in high efficiency and security for the encryption system. Here, ciphertext confidentiality is achieved through AES encryption, but integrity is maintained by an authentication tag, which is an all-in-one process.
Can Symmetric Encryption systems be hacked?
Despite being a reliable method for securing sensitive information, symmetric encryption still faces certain threats. To break an adversary’s symmetric encryption system, there are two aspects that the malicious attackers must investigate: the secret key and the encryption algorithm. These two aspects are the foundation on which the encryption’s strength is based, so any breach in their security may result in sensitive information being made available to an undesirable party.
Advanced cryptanalysis is the primary method used by adversaries seeking to break symmetric encryption, which involves mathematical methods being applied to discover weaknesses in the encryption methods. Central to this approach is the “ciphertext-only attack,” which refers to an approach where an attacker has access to the encrypted contents of a message only and applies analysis over the ciphertext, which enables the deciphering of the secret key without ever directly accessing it.
NIST Recommendations for Securing Symmetric Encryption Keys
Several factors influence the strength of the symmetric encryption keys. They are as follows:
1. Length of the key bit size
It is recommended to use longer keys to resist brute-force attacks, which is a type of attack that makes use of all possible key combinations to decrypt the encrypted data. For instance, in the case of AES encryption, NIST specifies the use of a 256-bit key size for provision against future computing technologies like quantum computers.
The key length is determined by the encryption algorithm used and the level of security desired; NIST also recommends the appropriate key length for various algorithms such as AES and others.
2. Randomness
The NIST emphasizes the importance of high-quality randomness, which is unpredictable in the process of key generation. Such randomness, ideally, is taken from a safe origin, such as a cryptographically secure pseudorandom number generator (CSPRNG).
For example, SP 800-90A provides ‘Recommendation for Random Number Generation’ so that no pattern and regularity are predictable.
3. Key generation
It is vital that the key generation system make certain that the keys produced are both unpredictable and unique to each instance. In NIST’s recommendations, it is clearly pointed out that any key-generating process should avoid applying any method that is weak or can be easily predicted, such as system timestamps.
4. Key Management, Rotation, and Destruction
In terms of key management, the NIST mentions that the methods of storage, distribution, and usage of keys should be safe. Regular key rotations should take place to bring down the risks associated with the use of keys over a long period. Old keys must also be revoked in order to prevent unauthorized access, and they must be destroyed so that unauthorized recovery is not possible. All these, along with the policies about secure accesses, key rotation, and destruction, must be implemented via key management systems.
5. Access Control
Access to symmetric keys should be limited according to the principle of Role Based Access Control (RBAC) and Identity Access Management (IAM). Only personnel or systems that are given permission to use the keys should be granted access.
Some restrictions need to be imposed for monitoring key usages and activities, such as logging and auditing, to prevent or mitigate who tries to misuse keys or access them without authorization.
To learn more, visit here.
Advantages of Symmetric Encryption
Symmetric encryption offers various advantages that enhance the effectiveness of data security. Below are some of the key advantages:
1. Speed and Efficiency
Symmetric techniques employ a single key for both encryption and decryption, which makes the advancement of such technologies less complex.
This is largely due to the fact that this particular approach uses efficient methods of performing computational processes that do not take up much operational time. In this sense, the efficiency of symmetric encryption becomes even more important for applications with low latency and high throughput, such as the protection of real-time voice communications, bulk data transfers, or network-level security protocols such as IPsec and SSL/TLS.
2. Low Computational Overhead
The symmetric key algorithm is designed in a way that minimizes the cost of computation and, hence, will be appropriate in those applications where real-time encryption and decryption should be taking place.
In contrast, the key techniques that are used in asymmetric encryption are the modular arithmetic-based key techniques, which are very resource-intensive. On the other hand, symmetric encryption algorithms rely on simple bit manipulations with less requirement on the system. Therefore, this makes symmetric encryption suitable for low-powered systems or applications that do not have high processing requirements, such as embedded systems, including mobile applications and IoT devices.
3. High Security
Symmetric encryption algorithms, which include AES-256, offer great security through larger key sizes and system designs that are resistant to modern cryptographic attacks, especially brute-force or different cryptanalysis attacks.
One such design is AES-256, which works with a 256-bit key and is well recognized for its massive security in theoretical as well as practical scenarios of cryptography. Together with efficient controls for protecting the encryption keys, such as hardware security modules (HSMs) for key storage and short-time duration session keys, symmetric encryption expands its ability to safeguard the confidentiality of data in several areas, from the transmission of sensitive information to disk encryption.
4. Scalability for Large Data Sets
Because of its faster execution speed, symmetric encryption is naturally suitable for processing and transmitting large quantities of data. In contrast, asymmetric encryption is not efficient for encrypting bulk data because it requires a lot of time and computational power to encrypt and then later decrypt messages.
Symmetric encryption’s less operational time makes it useful in instances involving large data sets or data streaming, such as securing video streaming, etc.
5. Widely Adopted and Versatile
Symmetric encryption is one of the pillars and is extensively used in protocols for TLS/SSL, VPNs (OpenVPN), disk encryption (BitLocker), and many more. This is due to its efficiency and compatibility with the technology. Since symmetric encryption is almost always used together with other encryption techniques (for example, public-key cryptography for encrypting the symmetric keys), it allows for high performance. Therefore, it is widely adopted.
Disadvantages of Symmetric Encryption
Now that we know the advantages symmetric encryption offers, let us explore the limitations. The key challenges associated with it are as follows:
1. Key Distribution Problem
The cryptographic shared key in symmetric encryption has to be distributed over discrete channels with high risks of information leakage. If the insecure channel gets intercepted and someone gets hold of the key, then the security of the communication is compromised. Thus, additional protocols, e.g., Diffie-Hellman or any other supported public-key infrastructures, must be used to prevent exposure while distributing the keys.
2. Scalability Issues
In symmetric encryption, each unique pair of users is required to have a unique key, which causes the key management to grow exponentially with the total number of users. This increases the problem of scalability to a great extent, especially in environments where users are dynamic and keep changing, as that creates a lot of administration burden and threats to security.
3. Lack of Non-Repudiation
As the same key is used for both encryption and decryption, there is no non-repudiation guarantee in symmetric encryption. Since there is no proof of source, this makes it impossible to use such functions in applications where accountability is required, such as digital signatures or money exchanges.
4. Key Management Complexity
Symmetric key management, which includes the processes of generation, distribution, storage, rotating management, and revocation management of keys, becomes a tedious task when the number of keys increases. Vulnerabilities are introduced due to poor key management, which requires safe management system solutions like hardware security modules (HSMs) essential for secure handling.
5. The Risk of Key Compromise
If the secret key is disclosed, all data that was protected with this key will no longer stay protected. This is because, in symmetric encryption, a single key is used for both operations, where, if the key is revealed, it is possible to read every other encrypted text protected by that key. Hence, changing the keys often and keeping them away from the public is very important.
Combining symmetric and asymmetric encryption
Modern communication systems guarantee security as well as efficiency in hybrid encryption systems. An asymmetric key exchange mechanism starts the whole transactional process. First, the client and the server share their public keys to enable a secure channel for data transfer. This is particularly important in the authentication process of the server, while for the public key of the server, Certificate Authorities (CAs) have a significant part to play in the verification of the server’s public key’s access through the provision of digital certificates.
At this time, when a secure channel has already been established, a session key is randomly generated. The server’s public key, which is made available to the client, is used to encrypt the session key. Then, this encrypted session key is sent to the server, which has the corresponding private key, to decrypt it and get the session key. The shared symmetric key is efficient enough to allow all encrypted and decrypted data exchange between the client and the server
SCENARIO
Two individuals, namely Alice and Bob, where Alice wants to share a confidential document with Bob. Here, they employ symmetric encryption to ensure that the document is protected from unauthorized access.
Step 1: The initial step in communication is the establishment of a common secret key by mutually agreeing on a secure method to use a passphrase and securely exchanging it or by using secure key exchange protocols.
Step 2: As soon as the common secret key is established, Alice encrypts the sensitive document using a strong symmetric encryption algorithm. The plaintext document is thus transformed into ciphertext, ensuring no one can read it without the shared key. To add more security, encryption modes like Galois/Counter Mode (GCM) or Cipher Block Chaining (CBC) are applied, often combined with an initialization vector (IV) to prevent patterns in the encrypted data.
Step 3: Alice now sends the encrypted document to Bob. The ciphertext, even if intercepted while transmitting, cannot be read by unauthorized persons without the key. The secure channel that Alice can use to send the ciphertext to Bob includes encrypted email services, SFTP, or even offline methods like a USB drive.
Step 4: After receiving the ciphertext, Bob uses the same symmetric encryption algorithm and shared key in order to decrypt the ciphertext. The decryption process restores the original document to Bob and gives secure access to its contents.

Ensure compliance with cryptographic standards
FIPS 140-3
Annex A contains a comprehensive listing of the cryptographic algorithms that can be approved for use inside a cryptographic module. However, all algorithms mentioned in Annex A must also undergo validation under the Cryptographic Algorithm Validation Program (CAVP).
NIST Special Publications (SP)
SP 800-38A is an elaborated document that marks the selection and use of various block cipher modes of operation. It dives into the security properties as well as the advantages and disadvantages of each mode and assists the developers and implementers in making informed decisions.
SP 800-38D outlines the CCM mode of operation for block ciphers, providing recommendations for achieving both authentication and confidentiality in cryptographic processes.
ISO/IEC Standards
ISO/IEC 29192-2 lays down the specific security requirements and testing procedures of lightweight symmetric encryption algorithms. These algorithms are meant for resource-constrained devices that are deployed on the Internet of Things (IoT) or embedded systems, as the computational power and memory are not sufficient.
Use Cases
Symmetric encryption is utilized across various domains to ensure the confidentiality of sensitive data. Here are some major use cases for symmetric encryption and the importance they bring to the protection of digital information:
1. For securing data at rest
Data at rest refers to any digital information stored in a specified location across various storage facilities, such as cloud storage, file storage services, relational databases, non-relational databases, and data warehouses. This information is categorized into structured data, like that contained in tables, schemas, or spreadsheets, and unstructured data, such as text, video, images, and log files.
Most services use symmetric encryption to keep their backups secure. For example, AWS and IBM Cloud both recommend utilizing AES-256 for server-side encryption in transit and at rest to safeguard data with the strictest confidentiality by industry standards. Such highly secure encryption prevents any unauthorized access to the protected information in the cloud.
2. Securing Data in Transit with Virtual Private Networks (VPNs)
Symmetric security is applied in a VPN to produce an encrypted tunnel over which the information may be transmitted securely between the client and its hosts. In symmetric encryption, we use a shared key for both encryption and decryption to make it possible for only the sender and its associated receiver to read what is being sent. Typically, VPNs use encryption protocols like AES (Advanced Encryption Standard) in combination with secure key exchange methods (like Diffie-Hellman or ECDH) to securely share the symmetric key over the network.
The various VPNs use several strong algorithms to offer high-level security; for instance, the VPN protocols OpenVPN, which is free software, and SSTP, which was created by Microsoft, are both reliant on AES-256 in ensuring that data transmission is secure, especially where there is a high-security concern such as in preventing man-in-the-middle attacks.
3. For securing Wireless Network Communications (Wi-Fi)
Wireless fidelity networks usually apply protocols such as WPA (Wi-Fi Protected Access), WPA2, and the newest WPA3, which makes their usage secure in wireless communications.
In order to ensure security, they use symmetric encryption of data during movement, achieving perfect confidentiality and integrity without affecting the performance of wireless communication.
Post-Quantum Cryptography and its Impact on Symmetric Algorithms
Post-quantum cryptography focuses on mitigating the impacts of quantum threats on symmetric encryption with respect to key sizes and hybrid encryption systems. To know more details on how these advancements are shaping the future of encryption, read on.
1. Key size
An algorithm having a 128-bit key has 2128 possible combinations. This makes it impossible for classical computation to guess the key through brute force. However, as quantum technologies become more and more advanced, they are most likely to crack almost all current encryption algorithms.
The use of Grover’s algorithm reduces the effective key space of symmetric encryption for quantum computers. This algorithm allows a quantum computer to search through all possible keys at a speed proportional to the square root of the total number of combinations.
Thus, Grover’s algorithm halves the effective strength of symmetric keys.
To mitigate this problem, cryptographers use larger key sizes. For example, AES-256 is now considered the gold standard, as its 256-bit key offers an effective level of security, even in the presence of quantum computers.
2. Hybrid Encryption Systems
As discussed, quantum algorithms like Grover’s algorithm halve the effective strength of symmetric keys, thus necessitating larger key sizes for security. However, even if this risk is reduced, vulnerabilities with respect to an entire cryptographic framework, such as key exchange processes, can be exploited.
On the other hand, asymmetric encryption methods, which facilitate secure key exchanges, are most vulnerable to quantum algorithms such as Shor’s algorithm. This algorithm efficiently breaks these methods.
Therefore, hybrid encryption systems have come to the rescue. This is because, in hybrid systems, quantum-safe algorithms such as lattice-based cryptography, hash-based cryptography, or code-based cryptography are integrated into systems to protect the shared cryptographic key during encryption. With this multi-layered form of security, if one level of security is compromised, the other continues to keep the data safe. Hybrid systems combine both efficiency features from symmetric encryption and quantum resilience by means of quantum-safe algorithms.
Conclusion
Symmetric encryption stands out as one of the most acceptable ways to keep your information safe. Symmetric key cryptography allows ciphering and deciphering by the use of a common secret key, from which the allowable entities can only obtain the requisite secure data.
Organizations need to prepare for rising cybersecurity threats by enforcing strong symmetric encryption algorithms like AES, Blowfish and Twofish to prevent unauthorized access or data leaks of any kind.
- Introduction
- Types of Symmetric Encryption Algorithms and their modes of operation
- Can Symmetric Encryption systems be hacked?
- NIST Recommendations for Securing Symmetric Encryption Keys
- Advantages of Symmetric Encryption
- Disadvantages of Symmetric Encryption
- Combining symmetric and asymmetric encryption
- Ensure compliance with cryptographic standards
- Use Cases
- Post-Quantum Cryptography and its Impact on Symmetric Algorithms
- Conclusion

