- How does Zero Trust Security Work?
- Best Practices for Implementing Zero Trust
- Steps to Implement a Zero Trust Security Model
- Principles of a Zero Trust Security Model
- Benefits to a Zero Trust Security Model
- Challenges of a Zero Trust Model
- The road to a Zero Trust Security Model
- Services offered by Encryption Consulting
- Conclusion
Before we go deep into the Zero Trust Security model, we should first analyze the model called a Castle-and-Moat model. The Castle-and-Moat model assumes that whatever is inside the organization, i.e., on-prem, is highly trusted, while the resources outside the organization are untrusted. The weakness of this model lies in its misplaced intense focus on external threats. When an organization extends its network to the cloud, there is a flaw in this model where users can have permission to create resources that the user can then mark public or private. If the user marks it as public, then it is considered outside the organization, while making it private makes it inside the organization. It is not, however, the same case on-prem. In recent years, high-profile attacks taught that external threats are usually the least of a company’s problems. Even secured attack surface can still be infiltrated. Still, insider threats are frequently overlooked.
There are more disadvantages of the Castle-and-Moat approach that include:
- Providing permissions that are unclear or that can be overused.
- Allowance of Bring Your Own Device (BYOD), which results in data leakage.
- User authentication by passwords only.
This is where Zero Trust Security comes into the picture. The Zero Trust Model is based on the concept of “Trust No One,” whether it is inside of the organization or not. The Zero Trust Security model requires identity verification of every entity, whether it is a user or any network device trying to access private resources.
Cybercrimes are increasing day by day, so organizations need to be proactive about their data and network security. The Zero Trust Security model can be effectively used to secure data and networks from unauthorized access.
How does Zero Trust Security Work?
As hackers try to steal data regularly, data security is critical to a successful Zero Trust Model. The Zero Trust Security model focuses on increasing the organization’s data security, while integrating with current laws and providing the flexibility to adopt future security and privacy laws.
Data security is critical to an effective Zero Trust model, because hackers are constantly attempting to steal it. While all security safeguards are vital, there will always be a significant gap if data activity is not controlled.
Some areas need that need to be focused on for security purposes are:
-
Data Security
As data is a crucial part of every organization. The Zero Trust Security model protects the data by encrypting data-at-rest and data-in-transit before moving to cloud storage devices or any other devices. If a data breach occurs, even in with limited access to data, no one can read the data except the intended person.
-
Multi-factor authentication (MFA)
The Zero Trust Security model validates the user based on multiple factors including location, device, permissions, and IP address.
-
Micro-segmentation
This security model splits the data centres into secure segments or zones based on different parameters like user groups, locations, etc. Segments can have their own security policies that can act as border control within the system.
-
Logs and Packet Analysis
This deals with determining the source of the abnormal activity and monitoring all activities around it. It also creates logs for every activity, and inspects and analyzes all the traffic and data.
Best Practices for Implementing Zero Trust
Some best practices should be considered while implementing the Zero Trust Security model:
-
Understanding the Protection Surface
Regulatory compliance standards and guidelines such as General Data Protection Regulation (GDPR), make it compulsory for organizations to identify and secure data accordingly. All regulatory compliance standards and the Zero Trust Security model share a common component: the organization’s sensitive data.
-
Mapping the Connections
A conventional network architecture diagram that depicts network traffic flow is insufficient. A complete map of the various connections throughout the network is required for the Zero Trust Security model to be effective. It requires a detailed mapping of applications currently in use, data associated with the applications, and data transmission connections with enough details to decide where security controls are needed.
-
Architecting the Network Using Micro-Segmentation
Popular information security tools such as Firewalls, intrusion detection, and prevention systems, deep packet inspection tools, and data loss prevention tools, can be used to implement a Zero Trust environment, but they must be updated to assess and regulate traffic across the stack.
-
Implementing Zero Trust Policies
Organizations must develop and implement policies about the appropriate traffic flow that should be accepted or denied and enforced on all networks. The following questions should be considered while implementing Zero Trust Policies:
- Who is the user?
- What resource does the user want to access?
- Where are the requesting users and endpoints located?
- Why does the user want to access the requesting resource?
-
Monitoring Traffic continuously
All resources and traffic in an organization should be continuously monitored for better security and to detect malicious activity. Monitoring of traffic should be automated so that it effectively monitors and blocks unwanted traffic.
Steps to Implement a Zero Trust Security Model
A Zero Trust model is based on the concept “Trust No One.” Instead of implementing security measures at the network border, it concentrates on bringing them as close as possible to the actual surface that must be protected. It also requires strong user authentication and validation of the device over the network. The following steps should be followed to implement a Zero Trust Security model in your organization:
-
Identifying and Segmenting Data
One of the most challenging aspects of establishing Zero-Trust is determining which data is sensitive. The Zero Trust model requires micro-segmentation. Micro-segmentation is the process of dividing security perimeters into small zones so that different areas of the network can have independent access. A user who can access one of these zones should not be able to access another zone with the same authorization.
-
Implement Multi-Factor Authentication
Since a Zero Trust Security model is based on the concept of “Trust No One, always verify,” it requires verification every time a resource needs to be accessed. For that, Multi-Factor Authentication is a fundamental component of a well-designed network security strategy. Multi-Factor Authentication operates by requesting further information for verification. One-time passwords (OTP) are one of the most typical Multi-Factor Authentication elements that users follow. There are three main types of Multi-factor Authentication Methods:
-
Knowledge
It refers to the things that users know, such as a PIN or Password.
-
Possession
Things that users have, such as a smart card, ATM card.
-
Inherence
Things that users have attached to themselves, such as fingerprints, iris scanning, etc.
-
-
Implement the Principle of Least Privilege (PoLP)
Enforcing least privilege helps to reduce the overall cyber-attack surface by limiting super-user and administrator privileges. Least privileges must be enforced on endpoints so that malware attacks will not exploit elevated rights to increase access and move laterally to install or execute malware or otherwise damage the machine.
Access rights for applications, systems, processes, and devices can be restricted to to those permissions required to perform authorized tasks using the principle of least privilege. -
Validate all endpoint devices
Trust No One means No One, whether a user or a device. There must be a robust authentication procedure for the verification of the device also. Zero Trust Security can be achieved by extending the identity-centric controls to the endpoints. Any device used to access resources must be enrolled first for its identification and verification.
By implementing the Zero Trust Security model, an organization can have better control over access to resources, like who can access what resource.
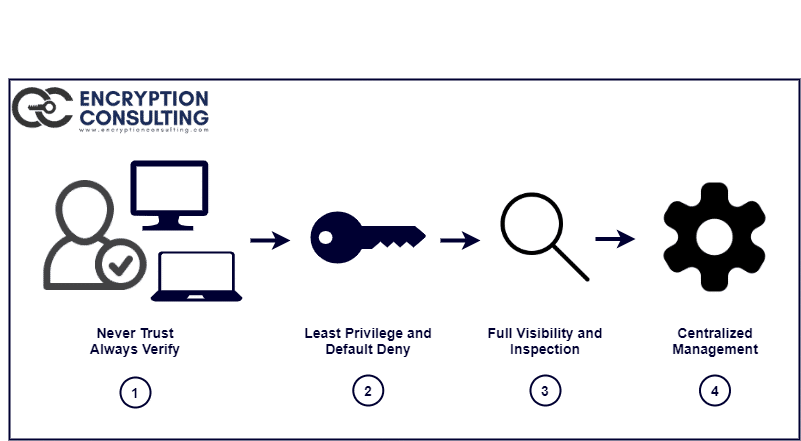
Principles of a Zero Trust Security Model
-
Strict Authentication Access
A Zero Trust Security Model is based on the concept of “Trust No One.” The organization should not trust anything inside or outside of it. According to the model, an attacker can be inside and outside the network, so the organization must authenticate and authorize access to every system.
-
Least Privilege Model
The Zero Trust Security model limits the user’s access only to the required resources based on their roles and can prevent the attacker from gaining full access to a large number of resources by getting access to a single account.
-
Documentation and Inspection
All activities must be assessed and authenticated under the Zero Trust approach. There must be a procedure that documents every action automatically. To detect any malicious activity running, the organization needs to analyze a complete picture of data accesses to guide better decision-making. It can also detect any malicious activity going on within the organization, like if any user tries to access the resource of another department not associated with them.
Benefits to a Zero Trust Security Model
-
User Identification and Access
The Zero Trust model uses multi-factor authentication (MFA) to access resources that are more secure than two-factor authentication. By making it mandatory for all employees and customers to verify their identity using Time-based One-time passwords, Google Authenticator, etc., only authorized users can access resources.
-
Robust Access Policy
The Zero Trust model uses micro-segmentation of data and resources, protecting critical data from unauthorized access. Splitting the organization’s network into segments, and each segment having its security policies, reduces the chances of attack by keeping vulnerable systems well-guarded. It can also mitigate insider risks.
-
Greater visibility across the Enterprise
The Zero Trust Security model is based on the concept “Trust No One.” When you’ve set up monitoring for all of your resources and activities, it gives complete visibility of who accesses your network with time, location, and which application was accessed.
-
Enhanced Data Security
A Zero Trust model restricts access to resources and reduces the attack surface through Robust Access Policy and User Identification and Access. By deploying the monitoring system, all ongoing activities are tracked.
-
Better User Experience
The Zero Trust model automates the verification process and makes it more efficient as users need not wait for approval for access requests.
-
Easy Cloud Migration
All organizations are moving to cloud-based solutions. The Zero Trust Security model provides a robust access policy and user identification process for cloud platforms, making it easier and more secure to migrate to the cloud.
Challenges of a Zero Trust Model
Following are some of the challenges and complexities associated with a Zero Trust model:
-
Technical Challenges
The Zero Trust model requires micro-segmentation of data and resources and monitoring all activities in an organization. But most of systems are not capable of meeting the Zero Trust model’s micro-segmentation requirements.
-
Legacy Systems
Legacy systems do not have a concept of least privilege, and the Zero Trust Security model requires multiple verification of the user trying to access resources. Based on the characteristics of legacy systems, monitoring network traffic is also nearly impossible due to the heavy encryption requirements of the Zero Trust model.
-
Peer-to-Peer Technologies
Many systems, including Windows operating systems and wireless mesh networks, adopt the peer-to-peer (P2P) model, which works in a decentralized manner and breaks the micro-segmentation model of the Zero Trust model.
-
Hybrid Cloud
The micro-segmentation model breaks when both cloud services, i.e., public and private, work together and unite to provide a common service, which in turn destroys the Zero Trust model.
-
Moving from Silos to Data-Centric
The majority of systems in use are data silos that contain both sensitive and general information. Because the Zero Trust model relies solely on data for verification and access control, efficient segmentation is required. Currently, most systems require a larger architecture.
The road to a Zero Trust Security Model
Due to redefining and reengineering job roles and their classification, implementing the Zero Trust Security model might be challenging for an organization. Organizations require an entirely separate inventory service for better device monitoring, greater visibility into apps, multiple user authentications, and enforcing access control policies. All these efforts are required at the managerial level. The trust in users must be based on their identity, devices, and resources they want to access, instead of access attempts. An organization must implement Multi-Factor Authentication and User Behavioural Analytics to establish the required level of trust.
Services offered by Encryption Consulting
The Zero Trust Security model focuses on increasing an organization’s data security while integrating with the present laws and having the flexibility to adopt future security and privacy laws. An organization can get an encryption assessment from Encryption Consulting to know how strong the current encryption techniques implemented by your organization are, how they can be improved, and what the encryption strategy should be. It can also help to know what privacy laws are currently followed by your organization.
Conclusion
On comparing the challenges and benefits of the Zero Trust Security model, we can conclude that the disadvantages are primarily related to the additional technicality necessary in the implementation phase. After implementing the Zero Trust model in an organization, it ensures greater trust within the organization and adds an additional security layer outside the organization. The only challenge associated with the Zero Trust model is how the organization adopts and implements it. Otherwise, it is an extremely effective cyber-security solution.
- How does Zero Trust Security Work?
- Best Practices for Implementing Zero Trust
- Steps to Implement a Zero Trust Security Model
- Principles of a Zero Trust Security Model
- Benefits to a Zero Trust Security Model
- Challenges of a Zero Trust Model
- The road to a Zero Trust Security Model
- Services offered by Encryption Consulting
- Conclusion

