It is crucial to understand that data protection is not just an issue that arises due to the legal and regulatory constraints it poses to businesses but a crucial factor in their operations. Cyber threats continue to evolve and become more complex which could require organizations to implement stringent security measures because of strict regulations like the GDPR, CCPA, HIPAA, and the PCI DSS. Therefore, you can use this blog as a hands-on guide to review and improve your current data protection framework.
Data Protection helps to safeguard information from unauthorized use, disclosure, or alteration while protecting individuals and persons or entities’ interest to organizations. The action plan that is aimed to be accomplished here is to ensure that such information does not fall into the wrong hands.
Key Principles of Data Protection
Accidental setbacks that can cause great harm to your organization can easily be prevented if an effective data protection structure is well adapted. Preserving the organization’s data involves an effective framework to control fraud and cyber threats depending on your organization’s needs.
The major concepts of information security convey an understanding that the individual who is involved in the data collection process is the one accountable for the customers’ personal information and there is no premeditated intent to deceive, the process and the message about the customers’ information are both objective. These principles are nearly all contained in data protection laws like the General Data Protection Regulation (GDPR) of the European Union. Below are the key principles:
Lawfulness, Fairness and Transparency
Due to compliance with the law, non-discrimination, and transparency, data about a particular individual will only be processed where it is required by law, for a contractually agreed purpose, by the consent of the holder of the data, or for any other lawful purpose. Data will not be processed in a false manner that would be deceitful to any person and the holder of data will have an understanding of how the data of an individual will be used.
Purpose Limitation
Data must always be collected in a lawful manner, and for a genuine purpose for which it is required. It should not go through a change that is not consistent with those objectives from the angle of legislation enactment.
Data Minimization
Personal data must be processed in a correct manner and the data must be kept accurate, where and when necessary, the data should be updated with correct information.
Accuracy
Personal data collected should not be excessive, irrelevant, or outdated for the stated purpose, and should be processed in a timely manner where necessary. Any incorrect data should be followed by immediate correction or deletion.
Integrity and confidentiality
For the cases of specific transformation from unauthorized access and moreover additional intended or unintended removal, destruction, and all other types of harm to the personal information for the same reasons, the personal information needs to be processed for safety against any forms of disorder and harm provided by applying the most suitable technologies or methods of management.
Data Protection Evaluation Checklist
Today more than ever before, everyone: business and private citizens alike must take data protection seriously because the world is digital. Since you also must abide by the law in the best possible way, you are advised to evaluate each of your data protection systems. Below, we have compiled a list of things that you can do to assess or upgrade all aspects of data protection.
-
Understand the Legal or regulatory requirements
Identify the strengths of regulatory and legal frameworks regarding your organization’s needs. Some of these include the General Data Protection Regulation (GDPR) for the European Union, The California Consumer Privacy Act (CCPA) for the United States, the Health Insurance Portability and Accountability Act (HIPPA), and the Payment Card Industry Data Security Standard (PCI DSS). It is important to establish exactly what these regulations are and how they can affect the protection of data in an enterprise.
-
Data Inventory and Classification
It is mandatory to develop an inventory of what data the organization owns and controls including PII, PHI, PCI, operational data, Intellectual property, and more, so that the organization knows what data it possesses. At the same time, data has sensitivity and business criticality levels which could be classified as highly sensitive, restricted, or public. The next step is to understand where the personal information is being stored, in the cloud, on the company’s premises, or other third-party servers.
-
Develop Data Protection Policies
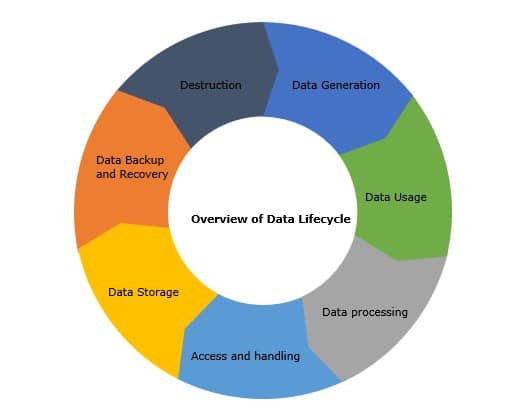
The top strategies for data protection should include the implementation of ideal policies and plans that should deal with data through the whole lifecycle of the said data, in processes such as generation, use, processing, access and handling, storage, backup, and disposal.
-
Data Encryption and Anonymization
Availability of required encryption solutions for securing data when it is stored (data-at-rest) and when it is transferred (data-in-transit) over a network for personal or sensitive information. All in all, to prevent this information from falling into the wrong hands, it is suggested that there should be an ongoing update in encryption protocols to the current standard as necessary. Wherever possible, ensure that personal information has been masked to obscure the identity of the individual involved.
-
Risk Assessment
Conduct a risk analysis of the possible risks and vulnerabilities that an organization may face, including internal risks like an employee using information for the wrong purpose, external risks where an outsider can access the organization’s information, and environmental risks that belong to the organization, like natural calamities.
-
Access Control
Specify a proper identification of access control measures, including but not limited to role-based access control (RBAC), multi-factor authentication (MFA), and regular review of access logs and audits to ensure that only the approved personnel can access your organization’s sensitive information
-
Regular Audits and Assessment
At least once a year, there should be data protection audits to identify the risks involved and the existing policies followed. Source with third-party auditors to evaluate the protective measures facilitating data within your organization. Here are a few tips that can be taken into consideration when conducting an audit:
- Form an audit team
- Establish a detailed audit plan, steps of procedure, and the documentation process
- Consider reviewing any previous records or information on consultations on a related issue
- Conduct workshops with identified stakeholders
- Assess existing data security measures, evaluate current and best practices for protecting data
- Evaluate employee training and awareness program
- Identify gaps in the current environment
- Provide recommendations for each identified gap
- Maintain regular progress tracking
-
Data Retention and Disposal
Implement a data retention policy to determine the time that different data types shall be retained. Also, make sure that the data can be erased efficiently when the data is no longer useful or required (e.g., shredding, wiping of hard disks, and more). Your organization also needs to review the data retention and disposal process and practices from time to time to ensure compliance with current standard practices within the industry.
-
Continuous improvement
There must be a clear realization when it comes to securing data that this is not a ‘set it and forget it’ process. It would be useful to carry out the revision of the data protection policy at regular intervals in order to ensure that the currently used measures of protection and, therefore, security policies and procedures in the company correspond to the norms, rules, and regulations set at the time when the policy was developed.
We have found that building a detailed data protection plan for your organization will effectively protect valuable company data and increase the confidence people have in your company.
-
Employee Training and Awareness
Run an awareness campaign to educate employees about the importance of data protection best practices and industry standards. Provide ongoing data protection training to employees.
How Encryption Consulting can help with Data Protection Evaluation
We are the global leaders in data protection, trusted by 100+ Fortune 500 companies. Our focus is on advising companies and organizations on the use of encryption and data protection systems and strategies. Through our data protection services, you will be able to devise a unique data protection plan based on your corporate security and compliance needs to complement your organization’s current data protection setup. In protecting sensitive data, we can be your valuable ally in your data protection regarding your endeavor to create a secure environment that shall accommodate your data. Get to know more about the specific aspects of our data protection advisory and implementation services.
Encryption Consulting’s Data Protection offering view:
We recommend treating data discovery and classification as the foundation to protect the data cycle. As observed at the beginning, an important core of proper data discovery and classification involves identifying the “Crown Jewels”, or the data that would be most precious to the organization in question. Our key service offerings, as part of our advisory services, include:
- Data Protection advisory services (assessment, strategy and roadmap)
- Vendor evaluation
- Proof of concept (POC) session
- Implementation of data protection/encryption solution
- Integration with identified use cases
- Help customers optimize and enhance the current data protection environment
Conclusion
Protecting sensitive data is an ongoing task involving continuously staying alert and enhancing security measures. Businesses’ implementation of this Data Protection Evaluation Checklist enables them to protect their data more effectively, adhere to relevant legislation, and maintain customer loyalty. The key to remaining ahead of newly developing hazards while guaranteeing their data’s privacy and security is through frequently reviewing and updating one’s data protection strategies.