AWS provides many services, including database, storage, networking, and many more. AWS Key Management Service (KMS) is one of the most popular services offered by AWS. It is a beneficial service that helps in dealing with sensitive data and managing cryptographic keys.
What is AWS Key Management Service (KMS)?
AWS KMS is a service that can be integrated with various other AWS services. It can be used to create, store, and control cryptographic keys to encrypt data in your application. With the help of the AWS KMS service, a user can control access to the encrypted data. AWS KMS provides almost 100 percent of the durability of cryptographic keys.
Keys are stored in multiple Availability Zones (AZ’s) that ensure the high availability of keys. AWS KMS is integrated with CloudTrail, which allows users to audit the purpose for which the key is used, when it was used, and by whom the key was used.
Some Important Points about AWS KMS
- The keys generated in a region cannot be sent outside of that region.
- KMS uses an AWS Hardware Security Module (HSM), which is FIPS 140-2 compliant, to store keys.
- AWS KMS allows controlling access to master keys.
- Users can encrypt data stored in Amazon EBS, Amazon S3, and Amazon Redshift as AWS KMS is integrated with these services.
How does AWS KMS work?
To learn the inner workings of AWS KMS, we must first learn the terms and concepts used in AWS KMS.
There are two types of keys in AWS KMS:
- Customer Master Keys
- Data Keys
Customer Master Keys (CMKs)
A CMK is a logical representation of the master key. The CMK contains metadata like key ID, Creation Date, key state, and description of the key and the key material used for encryption and decryption.
By default, Key material is created by AWS KMS. No one can modify, manage, view, or extract the key material. Key material cannot be deleted as well. If a user wants to delete key material, then the user has to delete the CMK. Users can import their key material into a CMK or create key material for CMKs in an AWS CloudHSM Cluster.
AWS CMK provides both Symmetric and Asymmetric CMKs. Symmetric CMKs use a 256-bit key for encryption and decryption. In contrast, asymmetric CMKs use RSA key pairs for encryption and decryption or Signing and verification. An asymmetrically created key, called an ECC key, can only be used for signing and verification. CMKs are created in AWS KMS. CMKs can be managed by the AWS Management Console or the AWS KMS API. All symmetric keys and private asymmetric keys never leave the AWS KMS unencrypted. To perform any cryptographic operation using CMKs, the user must use the AWS KMS API.
There are three types of CMKs supported by AWS KMS:
- Customer Managed CMK: Customer Managed CMKs are those CMKs in the user account that the user can create, own, and manage. Users have complete control over Customer Managed Keys, allowing them to establish and manage their key policies, IAM policies, grants, rotation of cryptographic material, etc.
- AWS Managed CMK: The CMKs in the user account created and managed by AWS on behalf of the user is known as AWS Managed CMKs. AWS managed CMKs cannot be directly used in cryptographic operations. Users cannot manage, rotate or change the key policies of AWS managed CMKs. However, users can view the key policies and audit their use in AWS CloudTrail (integrated with AWS KMS) in their AWS account.
- AWS Owned CMK: The Collection of CMKs owned and managed by AWS for use in multiple clouds is known as an AWS Owned CMK. AWS owned CMKs protect the resources in the user account. These CMKs are not found in the user’s account. With AWS owned CMKs, users do not need to create or manage CMKs. Users cannot view, use, track, or audit them.
Data Keys
The keys used to encrypt data and other data encryption keys are Data Keys. Data keys are used to encrypt a large amount of data as customer master keys (CMKs) cannot encrypt data larger than 4KB. Data keys are used and managed outside of AWS KMS. Data keys are not stored, managed, or tracked by AWS KMS. AWS KMS does not perform any cryptographic operation with data keys, however, users can generate, encrypt, and decrypt data keys with the help of AWS KMS customer master keys (CMKs). Data keys can encrypt and decrypt data in other AWS services like Amazon S3, EBS, EC2, etc.
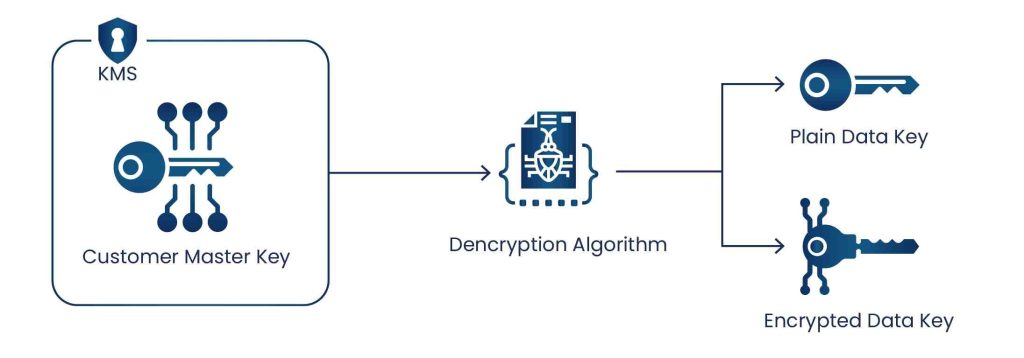
- Create data key
AWS KMS uses user-specified CMKs to generate a data key. A data key can be generated by calling the GenerateDataKey operation. This operation returns two copies of the data key, one in plaintext and the other one encrypted under the CMK. Another operation, GenerateDataKeyWithoutPlaintext, can also be used, which returns a single copy of the data key that is encrypted under CMK.
Before using an encrypted data key, ask AWS KMS to decrypt it.
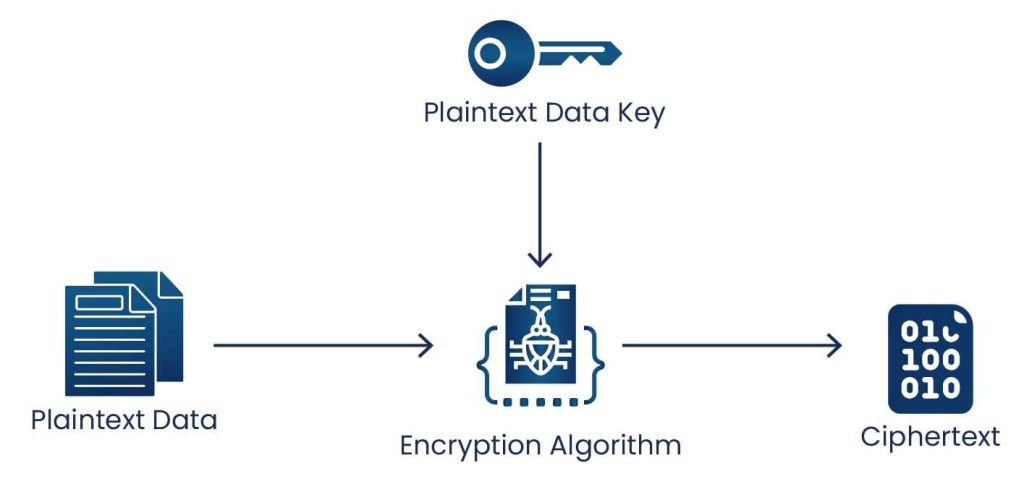
- Encrypting data with a data key
As mentioned earlier, AWS KMS does not use data keys to perform any cryptographic operation. To encrypt data with a data key, use a plaintext data key, encrypt data outside of AWS KMS, and delete it from memory, then, store the encrypted data key.
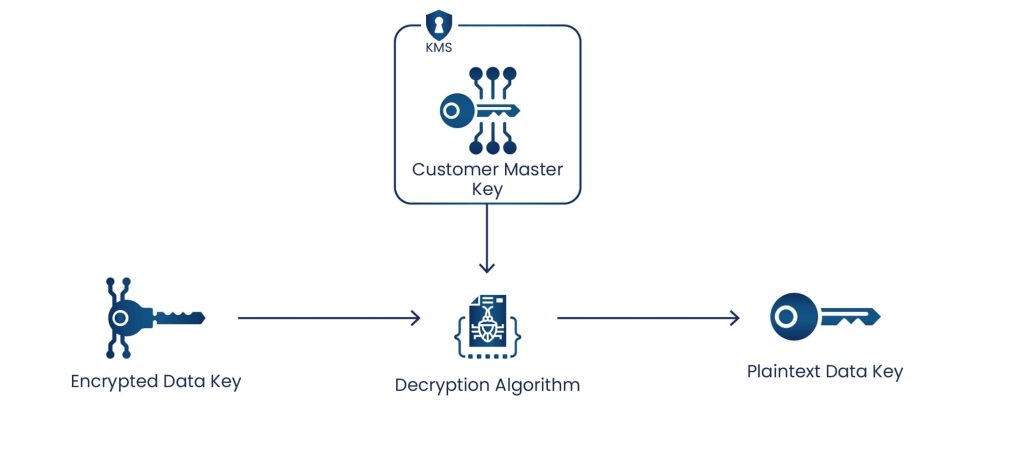
- Decrypting data with a data key
To decrypt data outside of AWS KMS with a data key, the Decrypt operation is used to decrypt the encrypted data key, which returns a plaintext copy of the data key.
Now, Data outside of AWS KMS can be decrypted using a plaintext data key. The user must remove the plaintext data key from memory after using it.
The following diagram show how the Decrypt operation decrypt the Encrypted Data Key:
- Data Key Pair
Users can create an asymmetric data key pair consisting of mathematically related private and public keys. Generally, these key pairs are used for client-side encryption and decryption or the signing and verification process outside of AWS KMS.
The private key of each data key is protected by AWS KMS using user-specified symmetric CMKs, but users have to manage and use the data key pair outside the AWS KMS as it does not track, manage or use data key pairs to perform any cryptographic operations.
Users can generate the following data key pairs in AWS KMS:- RSA key pair of 2048 bit, 3076 bit, and 4096 bits. Generally used for encryption and decryption.
- Elliptical Curve key pair: ECC_NIST_P256, ECC_NIST_P384, ECC_NIST_P512, and ECC_SECG_P256K1. Generally used for Signing and verification.
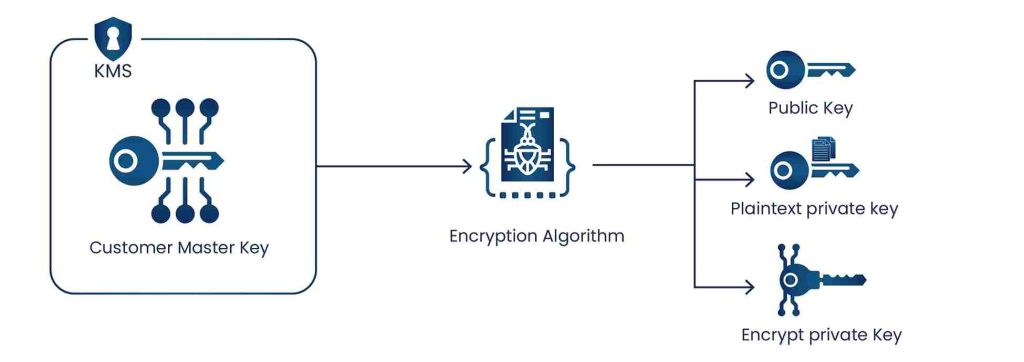
- Creating a Data key Pair
To generate a data key pair, the user needs to call the GenerateDataKeyPair or GenerateDataKeyPairWithoutPlaintext operation according to the requirement and specify a symmetric CMK that will encrypt the private key.
GenerateDataKeyPair operations generate three keys: a plaintext public key, a plaintext private key, and an encrypted private key. In contrast, GenerateDataKeyPairWithoutPlaintext generates two keys: a plaintext public key and an encrypted private key.
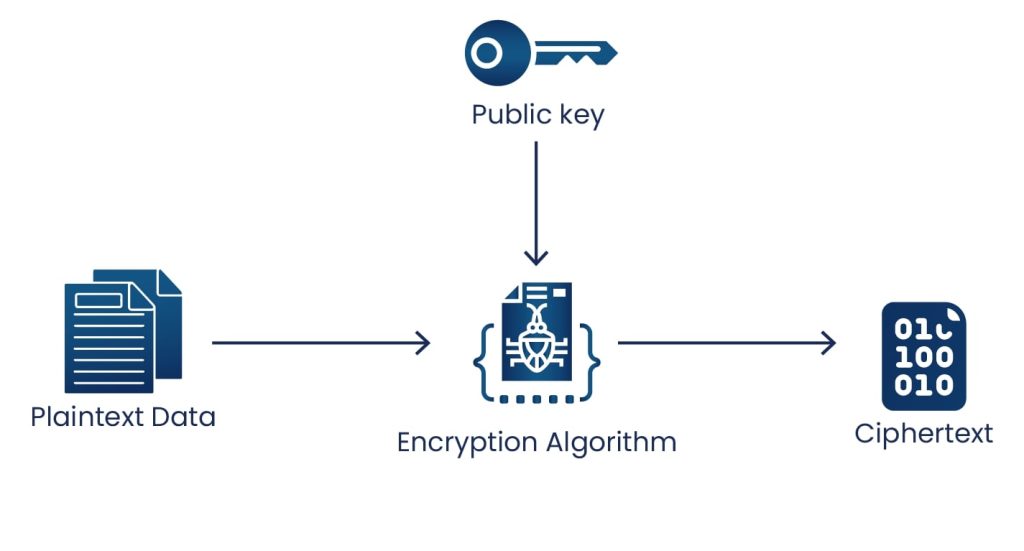
- Encrypting data with a data key pair
The public key of a data key pair is used to encrypt the data, and the private key of the same data key pair is used to decrypt the data.
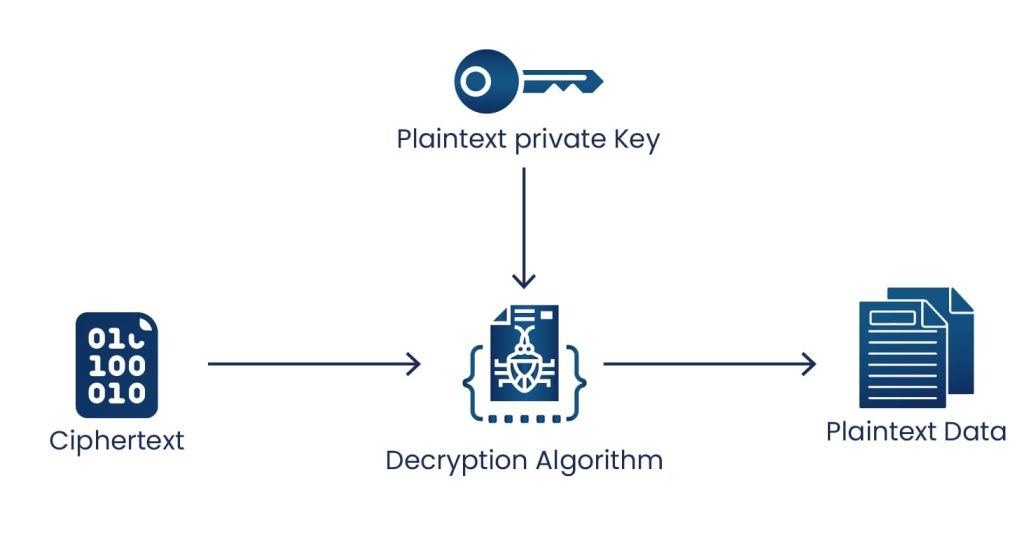
- Decrypting data with a data key pair
The plaintext private key of the same data key pair whose public key was used for encryption is used to decrypt the data. The Decrypt operation is used to decrypt the encrypted private key of a data key pair, and remove the plaintext private key from memory after using it.
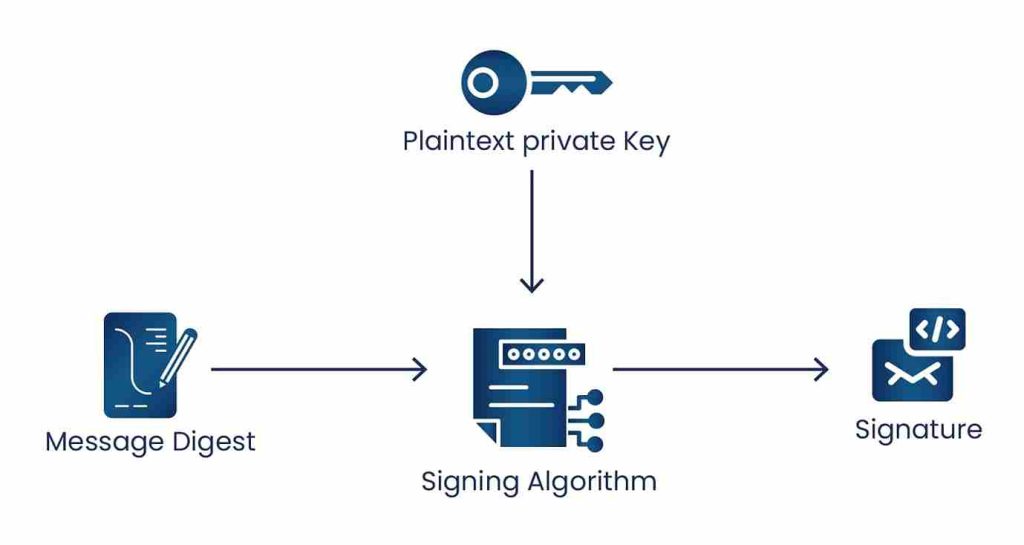
- Signing messages with a data key pair
The plaintext private key of a data key pair is used to generate a cryptographic signature for a message, and anyone with the public key of the same data key pair can use it to verify the signature.
If the private key is encrypted with the AWS CMK, the Decrypt operation is used, which returns the private key in plaintext format used for signing purposes. As always, the user should remove the plaintext private key from memory after use.
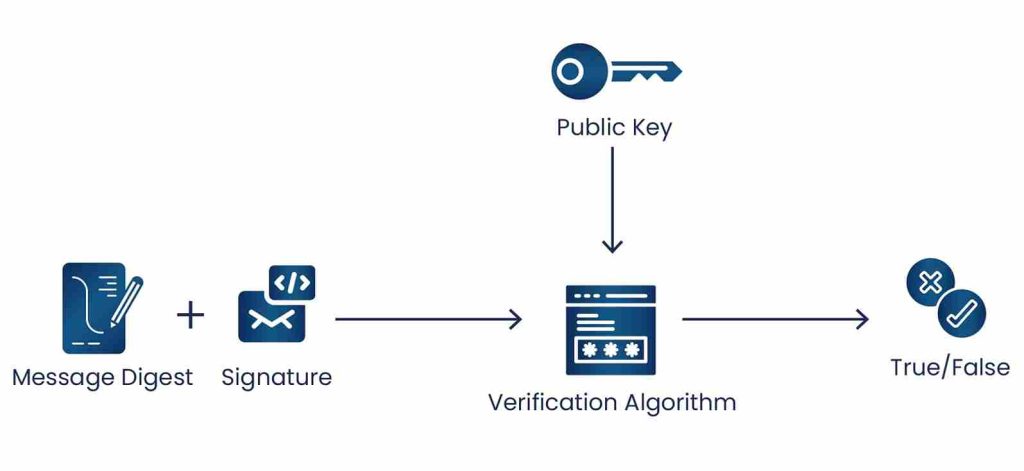
- Verifying a message with a data key pair
The public key of the data key pair is used for verification. The public key should belong to the same data key pair whose private key was used for Signing. Verification of the signature confirms that an authorized user signed the message and it has not been altered.
- Aliases
Users can give a friendly name to a CMK known as an Alias. For example, the CMK name is 9897aswd-34dw-1234-89hg-asdkal212012, the user can give it an alias of key-01. With the help of an alias, users can easily identify a CMK in AWS KMS operations. - Cryptographic Operations
The AWS SDK, AWS Tools for PowerShell, or AWS Command Line Interface (AWS CLI) is required to perform any cryptographic operations with CMKs because CMKs remain within AWS KMS. Users cannot perform any cryptographic operation with CMKs in the AWS KMS console.
Below is a table which summarizes the AWS KMS cryptographic operations:
| Operation | CMK Key Type | CMK Key Usage |
|---|---|---|
| Decrypt | Symmetric/Asymmetric | ENCRYPT_DECRYPT |
| Encrypt | Symmetric/Asymmetric | ENCRYPT_DECRYPT |
| GenerateDataKey | Symmetric | ENCRYPT_DECRYPT |
| GenerateDataKeyWithoutPlaintext | Symmetric | ENCRYPT_DECRYPT |
| GenerateDataKeyPair | Asymmetric | ENCRYPT_DECRYPT |
| GenerateDataKeyPairWithoutPlaintext | Asymmetric | ENCRYPT_DECRYPT |
| ReEncrypt | Symmetric/Asymmetric | ENCRYPT_DECRYPT |
| Sign | Asymmetric | SIGN_VERIFY |
| Verify | Asymmetric | SIGN_VERIFY |
Note: GenerateDataKeyPair and GenerateDataKeyPairWithoutPlaintext operations generate asymmetric data key pair which symmetric CMKs protect it.
- Envelope Encryption
Users can protect their plaintext data by encrypting it with a key, but how do they protect the encryption key? This brings in the concept of Envelope encryption, where the plaintext data is encrypted with the data keys, and the data keys are encrypted with master key. AWS KMS is responsible for the security of the master key. Master keys are stored and managed by AWS KMS and never leave the HSM unencrypted.
Benefits of Envelope Encryption:- Protecting data keys: The data keys are inherently protected by encrypting them with CMKs. So, the encrypted data keys can be safely stored with encrypted data.
- Encrypting the data key with master key: Encrypting large data with data keys, again and again, can be a time-consuming process. So, instead of encrypting data repeatedly, the encryption key can be encrypted with a master key.
- Combining the strength of multiple algorithms: Envelope Encryption enables you to use the strength of both Symmetric and Asymmetric algorithms.
- Key Policy
Users can define the permissions for CMK in a document called a key policy. Users can add, remove or change permissions at any time for Customer Managed Keys, but cannot edit the AWS Managed CMK as AWS manages it on behalf of the user. - Grant
Grants are temporary permissions that users can create, use, and delete without changing key or IAM policies. Grants are also considered with IAM policies and key policies when users access a CMK. - Auditing CMK Usage
AWK KMS is integrated with CloudTrail, which can be used to audit key usage. CloudTrail creates log files for AWS API calls and related events in the account. These log files contain all AWS API requests from AWS SDK, AWS Management Console, or AWS command-line tools. These log files can be used to find important information like when the CMK was used, which operation was requested, requester identity, and the source IP address.
Creating Customer Managed Symmetric CMKs
A user should follow the following steps to create Customer Managed Symmetric CMK using AWS Management Console:
- Sign in to the AWS management console and open the AWS KMS console.
- You can change the AWS region from the upper-right corner of the page.
- Choose customer manages keys from the navigation pane.
- Choose create key.
- In Key type, select the type of CMK, i.e., Symmetric.
- Click on Next.
- Create an alias for the CMK.
- Type the description for the CMK. (Optional)
- Click on Next.
- Type a tag key and tag value. (Optional)
- Click on Next.
- Select IAM users and roles that can administer the CMK.
- Clear Allow key administrators to delete this key check box if you do not want to allow IAM users and roles to delete this key. (Optional)
- Click on Next.
- Select IAM users and roles that can use the CMK to perform cryptographic operations.
- In the Other AWS accounts section, click on Add another AWS account and type AWS account identification number to allow them to use this CMK for cryptographic operations. (Optional)
- Click on Next.
- Review the key configuration that you have done.
- Click on Finish to create the CMK.
Creating Customer Managed Asymmetric CMKs
A user should follow the following steps to create Customer Managed Symmetric CMK using AWS Management Console:
- Sign in to the AWS management console and open the AWS KMS console.
- You can change the AWS region from the upper-right corner of the page.
- Choose customer manages keys from the navigation pane.
- Choose create key.
- In Key type, select the type of CMK, i.e., Asymmetric.
- In Key usage, select the purpose for which key is created, i.e., Encrypt and decrypt or Sign and verify.
- Select the specification of your asymmetric CMK.
- Click on Next.
- Create an alias for the CMK.
- Type the description for the CMK. (Optional)
- Type a tag key and tag value. (Optional)
- Click on Next.
- Select IAM users and roles that can administer the CMK.
- Clear Allow key administrators to delete this key check box if you do not want to allow IAM users and roles to delete this key. (Optional)
- Click on Next.
- Select IAM users and roles that can use the CMK to perform cryptographic operations.
- In the Other AWS accounts section, click on Add another AWS account and type AWS account identification number to allow them to use this CMK for cryptographic operations. (Optional)
- Click on Next.
- Review the key configuration that you have done.
- Click on Finish to create the CMK.
Benefits of AWS KMS
- Fully managed: AWS KMS provides full control access to encrypted data by enforcing the permissions defined by the user to use keys.
- Centralized key management: AWS KMS provides a single control point to manage and define key policies. Users can create, import, manage, delete, or rotate keys from the AWS key management console, or use AWS CLI or SDK.
- Digitally Sign data: The user can generate an asymmetric key in AWS KMS and can perform digital signing operations to maintain the integrity of the data.
- Secure: In AWS KMS, keys are generated and protected in Hardware security modules (HSMs) validated under FIPS 140-2. For security, keys are only used inside HSMs and can never be shared outside the AWS region in which they were created.
- Built-in auditing: AWS KMS is integrated with CloudTrail to help in monitoring key usage to meet regulatory and compliance needs.
Below is the table which summarizes the AWS Key Management Service Crypto Properties:
| Tenant | Multi-Tenant |
| Standard | FIPS 140-2 Level 2 |
| Master Keys | – Customer Owned Master key – AWS Managed Master Key – AWS owned Master key |
| Crypto Keys | – Symmetric – Asymmetric – AES in XTS mode only |
| Crypto API | AWS SDK/API for KMS |
| Access Authentication/Policy | AWS IAM Policy |
| Key Accessibility | Accessible in multiple regions (Keys outside the region in which created cant be used) |
| High Availability | AWS Managed Service |
| Audit Capability | – CloudTrail – Cloud Watch |
AWS CloudHSM
AWS CloudHSM is an AWS hardware security module that is customer-owned and managed. AWS CloudHSM acts as a single-tenant on hardware, restricting it from being shared with other customers and applications. Organizations can utilize AWS CloudHSM for those wanting to use HSMs to administer and manage encryption keys, but not have to worry about managing HSM Hardware in a datacenter.
AWS CloudHSM allows FIPS 140-2 Level 3 overall validated single-tenant HSM clusters in your Amazon Virtual Private Cloud (VPC) to store and use your keys. Complete control is given to users whose keys are used through an authentication mechanism separate from AWS.
AWS CloudHSM supports multiple use cases, including the following: management of Public/Private key pairs for Public Key Infrastructure (PKI), Code & Document Signing, or storing private keys for various services such as database, storage, and web applications, storing keys for DRM solution. AWS CloudHSM will allow your organization to meet compliances of key management requirements with the use of Hardware Security Modules supervised by AWS with the ability to incorporate multiple platforms to store keys.
Below is the table which summarizes the AWS Cloud HSM Crypto Properties
| Tenant | Multi-Tenant |
| Standard | FIPS 140-2 Level 2 |
| Master Keys | – Customer Owned Master key – AWS Managed Master Key – AWS owned Master key |
| Crypto Keys | – Symmetric – Asymmetric – AES in XTS mode only |
| Crypto API | AWS SDK/API for KMS |
| Access Authentication/Policy | AWS IAM Policy |
| Key Accessibility | Accessible in multiple regions (Keys outside the region in which created cant be used) |
| High Availability | AWS Managed Service |
| Audit Capability | – CloudTrail – Cloud Watch |
Custom Key Store
The Custom Key store feature of AWS KMS provides a way of integrating AWS CloudHSM clusters easily with AWS KMS.
Users can configure their CloudHSM cluster to store keys rather than the default KMS key store.
Users can also generate key material within the CloudHSM cluster. The master keys generated in the customer key store never leave the AWS Hardware Security Module in the CloudHSM Cluster in plaintext form, and all the cryptographic operations required by KMS are performed within the HSMs.
Conclusion
AWS CloudHSM provides single-tenant key storage giving organizations FIPS 140-2 Level 3 compliance. CloudHSM allows full control of your keys, including Symmetric (AES), Asymmetric (RSA), SHA-256, SHA 512, Hash-Based, or Digital Signatures (RSA). On the other hand, AWS Key Management Service is multi-tenant key storage owned and managed by AWS. AWS KMS allows Customer Master Keys for symmetric key encryption (AES-256-XTS) and asymmetric keys (RSA or elliptic curve (ECC)). Suppose your organization’s key management strategy for encryption will be running a singular cloud service provider for now and for the foreseeable future. In that case, AWS KMS will provide the simplest environment to maintain the keys. However, suppose you are planning to take advantage of multiple cloud providers but do not wish to maintain the HSMs. In that case, AWS CloudHSM may be the solution for your organization that allows separating encryption keys from the data of the other platforms that are being utilized.