Perform Signing with Jarsigner and PKCS#11 Library


Code signing is a critical process in software development that ensures the authenticity and integrity of applications, protecting them from tampering and unauthorized modifications. To enhance this process, Encryption Consulting’s PKCS#11 library offers a powerful solution for performing code signing with Jarsigner across multiple operating systems, including Windows, Linux (Ubuntu), and macOS.
The Jarsigner tool, included in the Java Development Kit (JDK), provides a robust mechanism for digitally signing files, making it an essential tool for Java developers distributing applications across various platforms.
It helps to sign the below mentioned file types:
Before we look into the process of signing using Jarsigner Tool and our PKCS11 Wrapper in Linux (Ubuntu) machine, ensure the following are ready:
To install the dependencies, run the following commands
Step 1: Go to EC CodeSign Secure’s v3.02’s Signing Tools section and download the PKCS#11 Wrapper for Ubuntu.
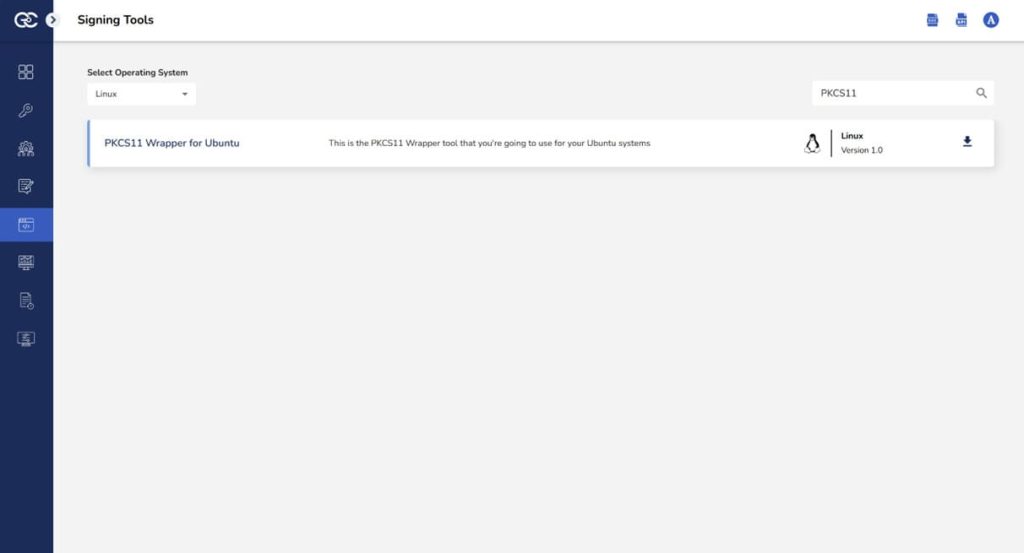
Step 2: After that, generate a P12 Authentication certificate from the System Setup > User > Generate Authentication Certificate dropdown.
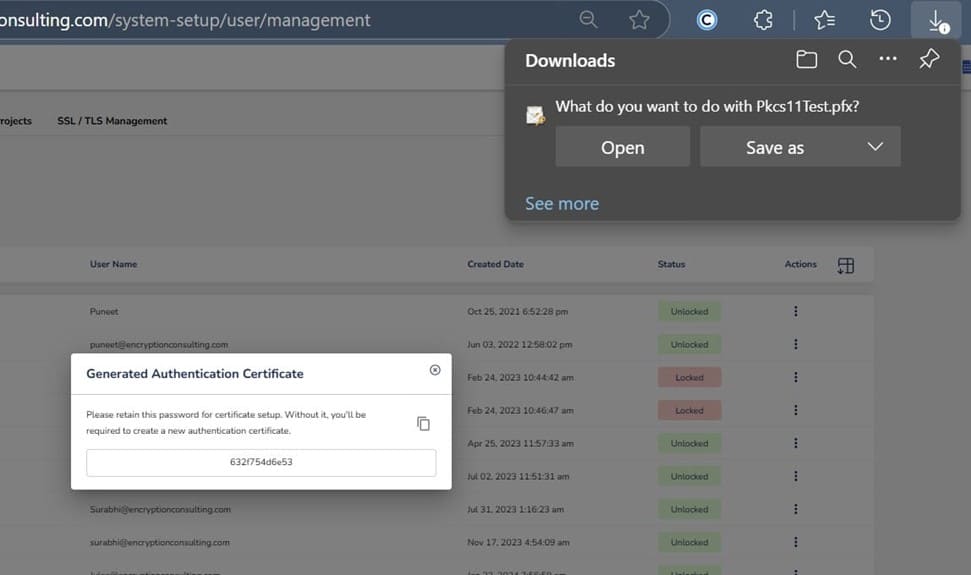
Step 3: Go to your Ubuntu client system and edit the configuration files (ec_PKCS#11client.ini and PKCS#11properties.cfg) downloaded in the PKCS#11 Wrapper.
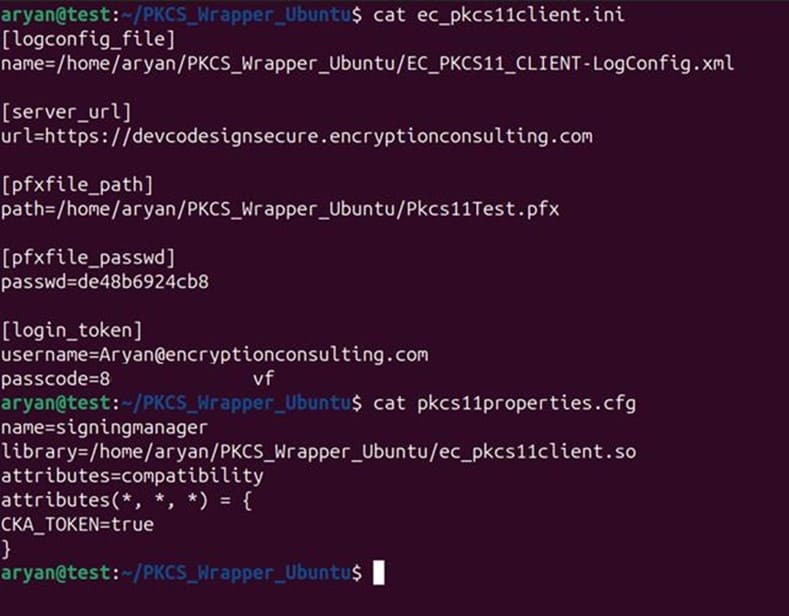
You will also need to install Java (Java 8-17) on your Ubuntu machine for Jarsigner to work with our PKCS11 Wrapper.
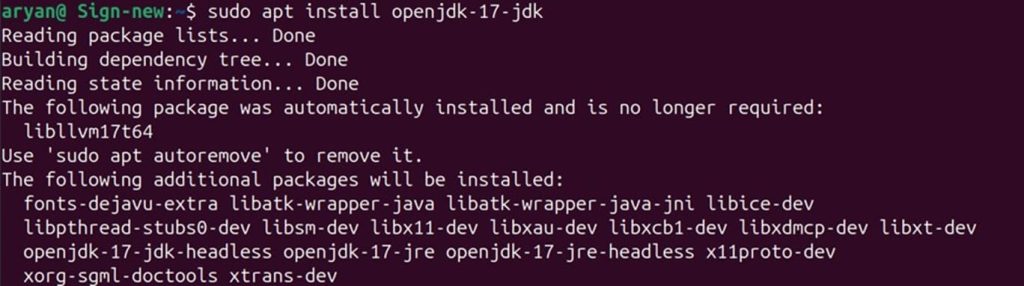
Step 1: Install Java 17 on your Ubuntu machine.
sudo apt install openjdk-17-jdk
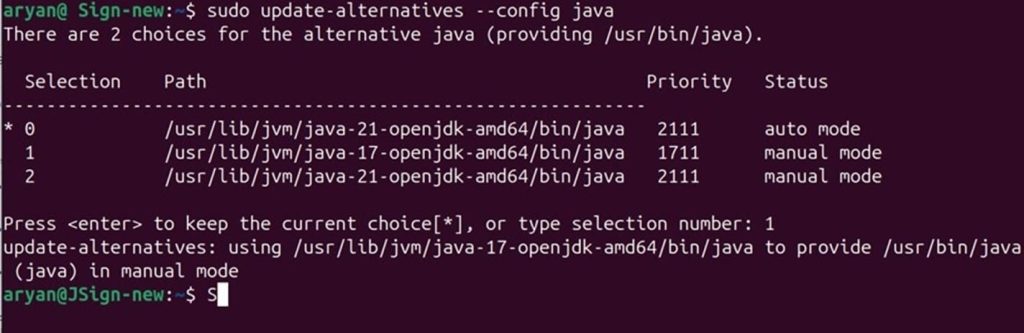
Step 2: Set Java 17 as the active version
sudo update-alternatives –config java
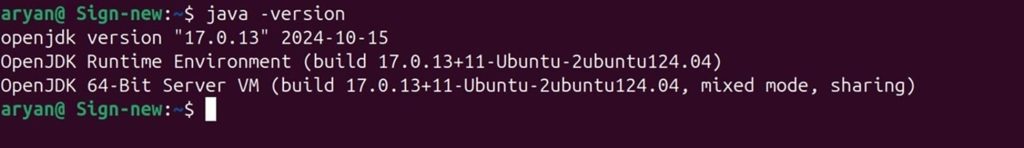
Step 3: Check whether Java has been installed properly or not
java -version
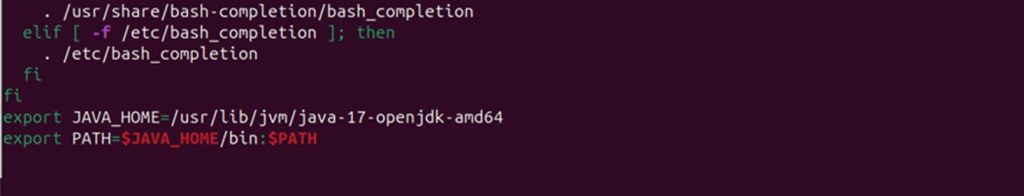
Step 4: Set Java 17 as the active version.
Run: nano ~/.bashrc
After running the above command, add these lines at the end of the file:
export JAVA_HOME=<Path of Java 17 bin folder>
export PATH=$JAVA_HOME/bin:$PATH
Press Ctrl + X, then Y to confirm, and then Enter to save.
Step 5: Reload the bashrc file
Run: source ~/.bashrc
Step 6: Check is the variable has been set
echo $JAVA_HOME
If not, then open a new terminal and try again.
Step 1: Change the working directory of the terminal to the folder that contains your “ec_pkcs11client.ini” and “pkcs11properties.cfg” files.
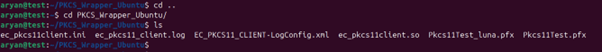
Step 2: Run the signing command from this directory.
<Path of Jarsigner tool> -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg <Path of pkcs11properties.cfg> -signedjar <Path of the file after signing> <Path of the file to be signed> <Key alias of the signing certificate> -tsa http://timestamp.digicert.com
A sample command is provided below:
jarsigner -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg pkcs11properties.cfg -signedjar helloworld_signed.jar helloworld.jar gpg2 -tsa http://timestamp.digicert.com
Step 1: For Verification, run the following command:
<Path of Jarsigner tool> -verify <Path of the file after signing> -certs -verbose
Step 2: A sample command is provided below:
jarsigner -verify helloworld_signed.jar -certs -verbose
Before we look into the process of using Jarsigner Tool and our PKCS11 Wrapper on a Windows machine, ensure the following are ready:
Step 1: Go to EC CodeSign Secure’s v3.02’s Signing Tools section and download the PKCS#11 Wrapper for Windows.
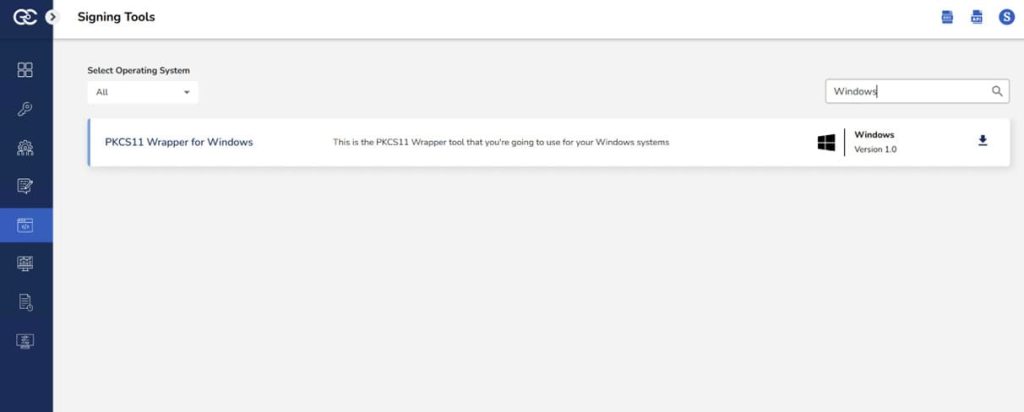
Step 2: After that, generate a P12 Authentication certificate from the System Setup > User > Generate Authentication Certificate dropdown.

Step 3: Go to your Windows client system and edit the configuration files (ec_PKCS#11client.ini and PKCS#11properties.cfg) downloaded in the PKCS#11 Wrapper.
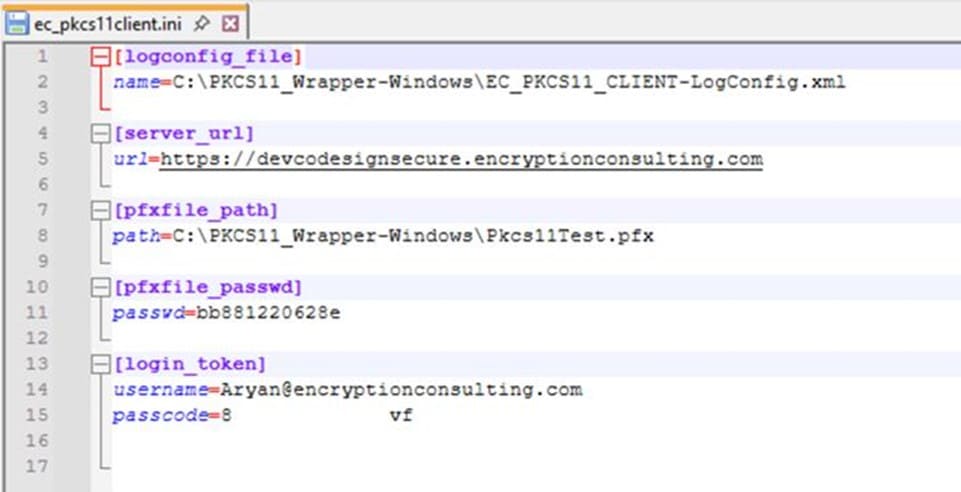
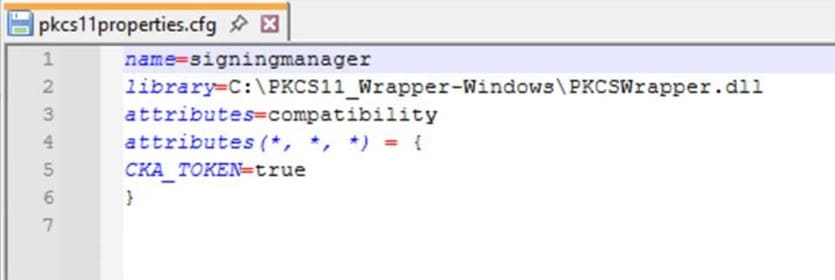
You will also need to install Java (Java 8-22) on your Windows machine for Jarsigner to work with our PKCS11 Wrapper.
Step 1: Install Java 22 (.exe installer) on your Windows machine from Oracle’s official site.
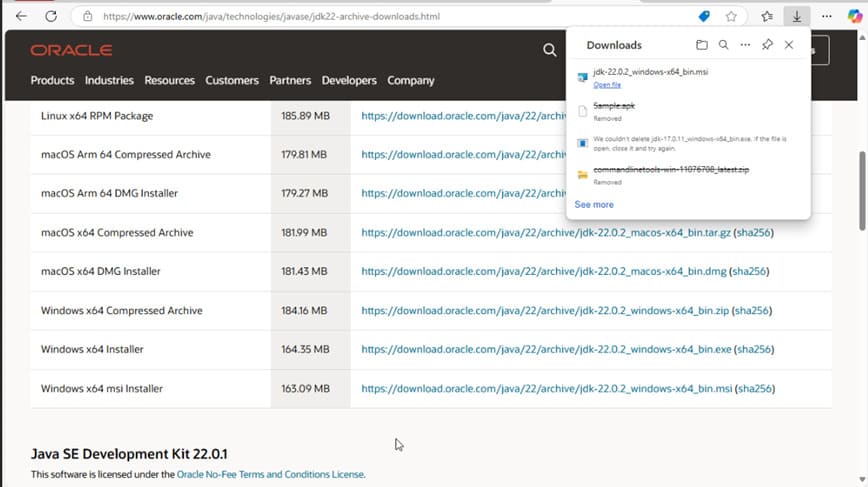
Step 2: Follow the instructions to install Java 22 on your machine.
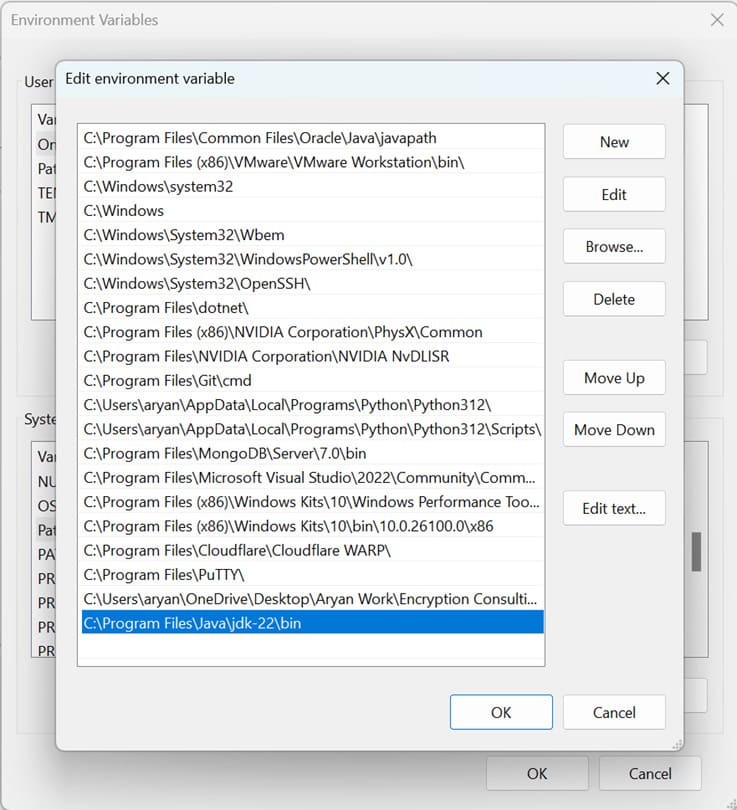
Step 3: Set Java 22 as the active version by storing the bin path in the PATH variable.
Step 1: Change the working directory of the terminal to the folder that contains your “ec_pkcs11client.ini” and “pkcs11properties.cfg” files.
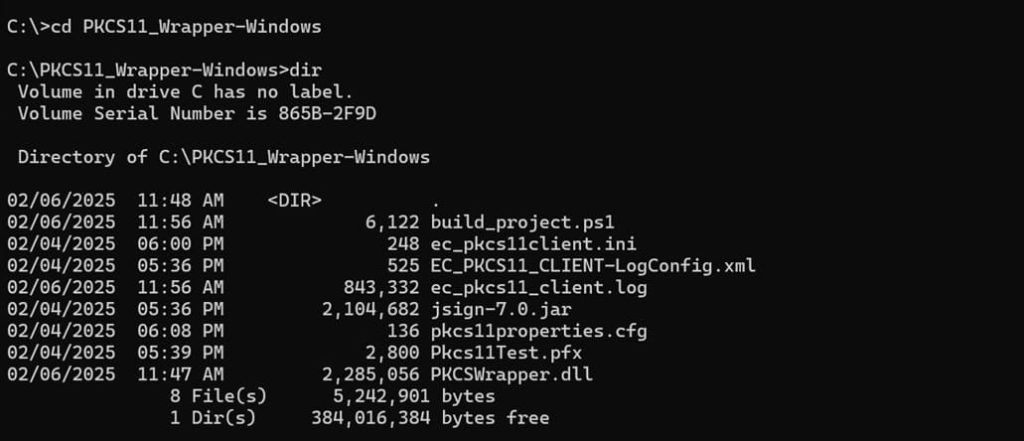
Step 2: Run the signing command from this directory.
<Path of Jarsigner tool> -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg <Path of pkcs11properties.cfg> -signedjar <Path of the file after signing> <Path of the file to be signed> <Key alias of the signing certificate> -tsa http://timestamp.digicert.com
A sample command is provided below:
jarsigner -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg pkcs11properties.cfg -signedjar helloworld_signed.jar helloworld.jar gpg2 -tsa http://timestamp.digicert.com
Step 1: For Verification, run the following command:
<Path of Jarsigner tool> -verify <Path of the file after signing> -certs -verbose
Step 2: A sample command is provided below:
jarsigner -verify helloworld_signed.jar -certs -verbose
Before we look into the process of using Jarsigner Tool and our PKCS11 Wrapper on a MacOS machine, ensure the following are ready:
To install the dependencies, run the following commands
Step 1: Go to EC CodeSign Secure’s v3.02’s Signing Tools section and download the PKCS#11 Wrapper for MacOS.
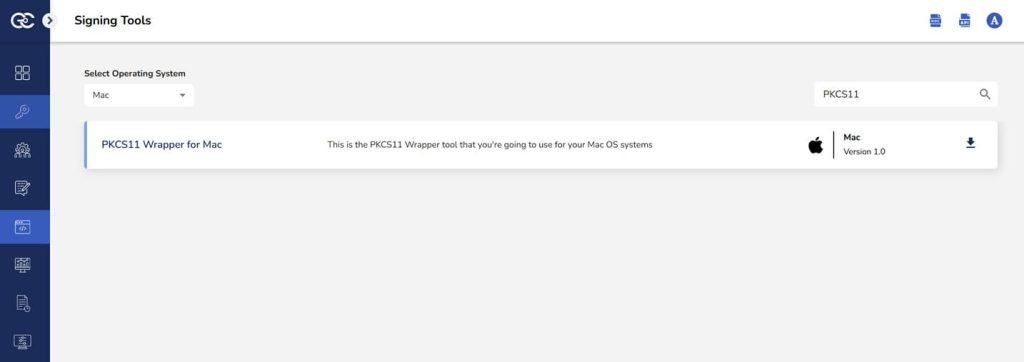
Step 2: After that, generate a P12 Authentication certificate from the System Setup > User > Generate Authentication Certificate dropdown.

Step 3: Go to your MacOS client system and edit the configuration files (ec_PKCS#11client.ini and PKCS#11properties.cfg) downloaded in the PKCS11 Wrapper.
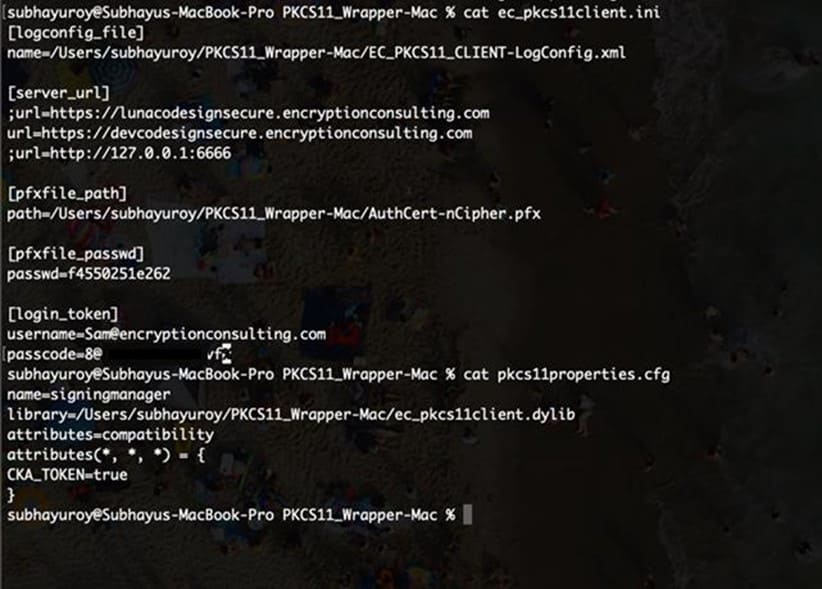
Install Java on your MacOS machine.
You will also need to install Java (Java 8-17) on your MacOS machine for Jarsigner to work with our PKCS11 Wrapper.
Step 1: Install Java 17 on your MacOS machine.
brew install openjdk@17
Step 2: Find the location where Java 17 is installed on your machine
brew info to openjdk@17
Step 3: Set Java 17 as the active version.
For Zsh: nano ~/.zshrc
For Bash: nano ~/.bash_profile
After running the above command, add these lines:
export PATH=<Path of Java 17 bin folder>:$PATH
export JAVA_HOME=<Path of Java 17 bin folder>
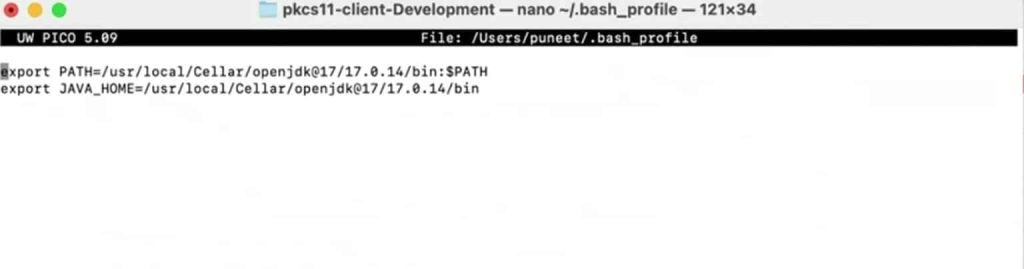
Step 4: Reload the environment variables
For Zsh: source ~/.zshrc
For Bash: source ~/.bash_profile
Step 1: Change the working directory of the terminal to the folder that contains your “ec_pkcs11client.ini” and “pkcs11properties.cfg” files.
Step 2: Run the signing command from this directory.
<Path of Jarsigner tool> -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg <Path of pkcs11properties.cfg> -signedjar <Path of the file after signing> <Path of the file to be signed> <Key alias of the signing certificate> -tsa http://timestamp.digicert.com
A sample command is provided below:
jarsigner -keystore NONE -storepass NONE -storetype PKCS11 -sigalg SHA256withRSA -providerClass sun.security.pkcs11.SunPKCS11 -providerArg pkcs11properties.cfg -signedjar helloworld_signed.jar helloworld.jar gpg2 -tsa http://timestamp.digicert.com
Step 1: For Verification, run the following command:
<Path of Jarsigner tool> -verify <Path of the file after signing> -certs -verbose
Step 2: A sample command is provided below:
jarsigner -verify helloworld_signed.jar -certs -verbose
Encryption Consulting’s CodeSign Secure takes code signing to the next level by offering a comprehensive platform that not only streamlines the signing process but also significantly bolsters organizational security. By leveraging advanced features like Hardware Security Module integration, client-side hashing, and virus scanning, CodeSign Secure ensures that signing keys remain safeguarded and that signed applications are free from malware.
CodeSign Secure integrates effortlessly into CI/CD pipelines, making it ideal for organizations aiming to automate and scale their development workflows while adhering to strict security policies. With detailed audit trails and policy enforcement, it provides transparency and accountability, helping businesses meet compliance requirements and build trust with their users.
By integrating seamlessly with Jarsigner, Encryption Consulting’s PKCS#11 library simplifies the configuration and execution of signing tasks, providing a consistent and secure experience regardless of the platform. Whether you’re developing on Windows, deploying on Ubuntu, or testing on macOS, this library empowers developers to maintain high security standards with minimal complexity.