You must have come across a situation where you had to download or send some personal information through the web. According to recent research, about 52% of organizations send confidential and sensitive data to public clouds, and 28% plan to do so in the next 12-24 months.
But have you ever had doubts about the security of your data, such as your access credentials or file transfers over the internet from another remote machine? There might be some attackers trying to get their hands on the personal information that you share via the unprotected network. As per a report by Rapid7, 41% of incidents happened due to unenforced or missing multi-factor authentication (MFA), particularly on VPNs and Virtual Machines.
To prevent such scenarios and attacks like credential stuffing, brute force, and key thefts, SSH or Secure Shell protocol was invented in 1995 by Tatu Ylönen so that you can easily identify and establish a secure connection with the server. SSH works on a client-server model, which allows you to create a safe tunnel between your machine (client) and the server to prevent unauthorized access to your information. There are many use cases of SSH, mainly focusing on the remote management of services and servers, such as remote access and command execution, file transfer, VPN implementation, and many more.
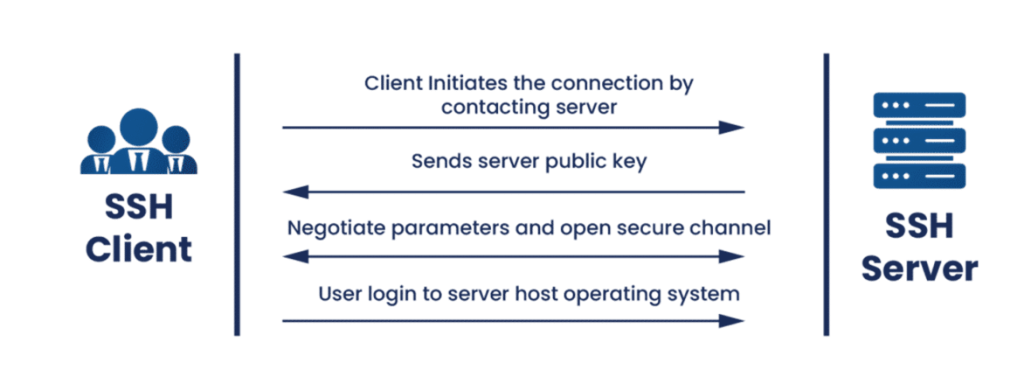
SSH provides several modes of user authentication, but the most common ones are password and public key authentication. Now, before we jump into SSH key sprawl and key management, let’s understand the basic process of SSH protocol using the figure below:
SSH Keys
SSH keys are a secure method for authentication and are used in many services. For instance, cloud platforms such as AWS, Azure, and Google Cloud use SSH keys to access virtual machines and other cloud services. These keys are also used by many developers around the world to access their GitHub repositories and to automate their CI/CD pipelines.
SSH keys rely on asymmetric keys, public and private, that make the SSH key pair. These key pairs are generated using strong cryptography algorithms such as Rivest–Shamir–Adleman (RSA) and Elliptic Curve Digital Signature Algorithm (ECDSA). These algorithms used different methods and combinations to ensure the strength and integrity of the key pair against any malicious activity and attacks. RSA is widely established but has limitations in performance and efficiency. ECDSA has smaller key sizes, resulting in faster operations and less resource consumption, making it a more viable option for modern computations.
Now, you might be thinking that since SSH keys are used for authentication mainly, why would you want to change from the traditional username and password authentication method?
Digital security is everything when dealing with unsecure networks. Passwords were a decent choice, but as technology evolves, this method is losing its credibility. They offer slow accessibility and are easily stolen. According to a survey conducted by GoodFirms entitled- “Top Password Strengths and Vulnerabilities: Threats, Preventive Measures, and Recoveries,” 45.7% of people use the same passwords for multiple accounts, and 52.9% of people share their passwords with their friends and family. Password security depends mostly on human factors that make this type of authentication vulnerable to cyber-attacks, which is a major concern.
SSH keys are a better and more convenient solution for remote access and operations. They allow faster connections and automation as you will not have to remember or enter any password for different client systems. Furthermore, incorporating Multi-factor Authentication (MFA) alongside SSH key authentication can greatly enhance the security and resilience of your system.
However, password authentication is not bad; it’s just unsuitable for remote access. You can still use passwords to protect your SSH private key for additional security.
| Password Authentication | SSH Key-based Authentication |
|---|---|
| Relatively less secure and prone to attacks. | It is more secure as it is extremely difficult to crack the private key. |
| Easier and quicker to set up. | Requires generating key pairs and configuring the server initially. |
| Not efficient for automation. | Good support for scripting and automated services. |
| It is less flexible when working with large teams. | Relatively more scalable and convenient in large organizations. |
SSH Key Sprawl
Now that you have an idea of why you should prefer using SSH keys, there can be some consequences of poor SSH key management. Organizations generate, share, and issue a huge number of key pairs for all their devices, making it difficult to handle and manage them. This accumulation of many unmanaged SSH keys is called SSH Key Sprawl. In large businesses, various factors like rapid infrastructure growth, frequent employee turnover, scaling operations, lack of centralized key management solution, using legacy systems, and many more primarily drive the SSH Key Sprawl situation.
SSH key sprawl directly contributes to significant organizational risks, particularly in relation to compliance violations with regulations like GDPR, CCPA, PCI DSS, HIPAA, and many more. Unmanaged SSH keys can allow unauthorized individuals to access data, violating the principle of least privilege and potentially exposing sensitive information, which conflicts with these regulations.
In October 2015, NIST introduced the IR 7966 (Security of Interactive and Automated Access Management Using Secure Shell) which includes specific guidelines to help organizations securely manage and operate SSH protocol. It mentions the vulnerabilities in SSH-based access and also provides the best practices that you should follow to protect your personal data.
Organizations must ensure that only certain users can access systems to prevent key sprawl situations. According to a 2022 survey report, around 57% of the respondents believed managing SSH keys was painful and difficult. However, as people have become more aware of this issue, this number has significantly reduced to 27% in 2024.
Now, despite such a major decline, SSH keys still pose a threat if not handled responsibly. But before we discuss the best practices for handling SSH Keys, let’s understand several factors that lead to SSH Key Sprawl.
-
No centralized key management
Many businesses tend to handle SSH keys that may be stored in a lot of different locations without proper management. Without a proper system, you can lose track of the keys and compromise the security of your access system.
As per the 2023 State of Machine Identity Management report, 54% do not have a centralized system and use manual processes such as spreadsheets to handle SSH keys. These methods of manual key management are prone to human errors and are time-consuming. They offer limited scalability and are susceptible to inconsistencies, which lead to increasing security risks.
-
Ad-hoc key generation
SSH keys can be generated relatively easily, and many users may generate keys on an ad-hoc basis without following any formal procedures. Imagine a developer who quickly generates an SSH key on their personal laptop for a quick test connection to a server without following any established key management guidelines and using a weak passphrase.
This will result in an increased risk of compromise and impact the overall security of your system. Strict oversight and policies are required by the organization to control the usability and accessibility of these keys.
-
Unsecure key rotation practices
SSH keys do not expire by default, so they can remain active for years even if they are no longer needed. Sometimes, old keys from former employees can still be active, or keys created for specific projects might stick around even after those projects are done. This can lead to security risks, as it can be hard for administrators to keep track of and remove these inactive SSH keys. Regularly managing these keys is crucial to maintaining a secure environment.
Situations such as Key Sprawl can have some serious consequences for the organization and pose a threat to user’s data. SSH Key Sprawl increases the risk of data breaches and unauthorized access. Attackers can also move laterally within a network, meaning that they can access more systems and sensitive data.
For example, if an attacker gets his hands on a valid SSH key-pair, not only will he gain access to the remote machine, but he can also install an information steeler program that will track and capture all the keystrokes, extract files, steal browser data, cookies, session data, and many more. As per the Cyber Threat Trends 2024 report by Cisco, Information Steeler programs had an average monthly block of around 246 million.
SSH keys never expire and need to be revoked explicitly. This can be easily exploited, for instance, by an ex-employee or an attacker, if not handled responsibly. You can also face legal action and financial penalties due to data breaches resulting from key sprawl that can damage your business’s reputation and erode customer trust.
| Category | Description | Impact on Organization |
|---|---|---|
| Data Breaches | Compromised SSH keys can lead to unauthorized access to sensitive data, resulting in data breaches. | Financial Penalties: Fines from regulatory bodies like GDPR, CCPA, and PCI DSS. Reputational Damage: Loss of customer trust, negative media coverage, and damage to brand image. Legal Action: Lawsuits from affected individuals and regulatory agencies. |
| Lack of Accountability | Poor key management hinders the ability to track and audit access to critical systems and data. | Difficulty in Compliance: Inability to demonstrate compliance with regulations that require accurate records of data access and security measures. Increased Audit Risk: Increased scrutiny from auditors and regulators, potentially leading to findings and recommendations that require significant remediation efforts. |
| Insufficient Data Protection | Unmanaged SSH keys can lead to situations where data is accessible to individuals who should not have access, violating the principle of least privilege. | Non-Compliance: Violation of data protection regulations like GDPR and CCPA. |
| Operational Disruptions | Compromised keys can disrupt critical operations, such as server access, application deployments, and network connectivity. | Business Interruption: Loss of productivity, revenue, and customer service. Financial Losses: Costs associated with incident response, system recovery, and business disruption. |
To understand the risks of having SSH Key Sprawl better, let’s take the help of a recent vulnerability discovered in April 2024, CVE-2024-31497, with the PuTTY SSH client. It allowed an attacker to recover a user’s NIST P-521 secret (private) key by capturing and analyzing approximately 60 digital signatures. This vulnerability is due to a bias in the way PuTTY generates ECDSA secrets when using the NIST P-521 elliptic curve. Now, for instance, if an organization is dealing with a Key Sprawl and has to revoke the existing SSH keys to deal with CVE-2024-31497 vulnerability, taking a quick response and remediation will be a time-consuming job.
Vulnerabilities like this are often discovered by security researchers through various methods, including code audits, fuzzing, and penetration testing. Researchers often look for security flaws or unexpected issues in software. When they find something, they usually let the software company know about it. The company then checks out the problem, works on a fix (or patch), and gets it out to users. How quickly this happens can depend on how serious the issue is and how fast the company can react. For serious vulnerabilities, companies usually make it a priority to release patches promptly to protect users from potential exploitation.
Best Practices
SSH keys play a crucial role in both identity management and authentication for secure remote access. IAM, or Identity and Access Management, provides the foundational security controls in any business, i.e., access and control, and there is no better way to provide access to users than by using SSH keys. This approach simplifies key management, reduces the risk of human error, and provides a more secure and efficient way to manage access to critical systems and data.
You can effectively avoid the SSH key sprawl situation by adhering to industry-preferred standards, which improve SSH key visibility, control, and security. This ultimately reduces the risk of cyber-attacks. Let’s explore the best practices to protect your SSH keys and systems.
- Management: You should implement a dedicated SSH key management solution that will help you manage, generate, store, distribute, and revoke SSH keys and improve the overall efficiency of your business. Using such automated systems for key generation and distribution will reduce manual errors and inconsistencies.
- Monitoring: Enforcing regular key rotation, such as monthly or quarterly, will minimize the impact of compromised and stale keys. You should delete and replace the untracked SSH keys with newly generated ones.
- Accessibility: Controlling the permissions of SSH keys is very important, as only authorized and specific user groups should have the privilege to access the remote servers and machines.
- Auditing: You must conduct regular security checks and audits to review SSH key usage patterns that will help your organization identify any anomalies or suspicious activity.
- No Hardcoding: Avoid using default passphrases and hardcoding SSH keys in application code and files, as this can create a backdoor for attackers.
- Key Mapping: You can also map SSH keys to a particular individual and not to an account. By doing so, it will prevent multiple users from accessing the same SSH key and help you monitor the key more effectively.
Conclusion
SSH key sprawl can lead to some challenges for organizations, such as potential data breaches, inefficiencies, and disruptions in operations. It can also negatively impact the organization’s reputation. When key management isn’t well-controlled, it becomes harder for businesses to monitor and manage access, which can increase the risk of unauthorized access and the loss of personal information. Taking steps to manage key sprawl is essential, as it helps protect organizations from possible legal and financial issues down the line.
SSH Keys are also used as signing keys which are crucial for verifying the integrity and authenticity of data. They ensure that data, such as code commits, remain unaltered and originate from the claimed source. For instance, SSH keys enable Git commit signing on GitHub, verifying the authenticity and integrity of commits by confirming their origin from the authenticated user.
Encryption Consulting’s CodeSign Secure solution will provide you with a robust platform for managing the entire lifecycle of SSH keys, automating key management processes, improving audibility, and significantly reducing the burden on security teams.
We provide expert advisory services to help your organization manage SSH keys effectively. Our team will help you develop a secure strategy to manage SSH keys, conduct regular audits and vulnerability assessments, and threat intelligence that will mitigate the risks associated with SSH keys.




