As you know, sensitive data such as personal information, financial transactions, and business communications are transmitted over the Internet, and securing them is necessary. Ensuring that this data is protected from eavesdropping, tampering, or unauthorized access is a challenge that the Transport Layer Security (TLS) protocol was designed to address. TLS was created in 1999 by the Internet Engineering Task Force (IETF). TLS refers to a cryptographic protocol created to provide secure communication over a computer network.
It guarantees that data transmitted between a client and a server is encrypted and makes it difficult for unauthorized parties to read or alter the information. TLS builds on SSL by addressing its vulnerabilities and enhancing security through stronger encryption algorithms, improved certificate validation, and protection against attacks like POODLE and BEAST. It also introduces features like forward secrecy and session resumption. It aimed to provide a more secure way to protect online communication.
Older versions of TLS, such as TLS 1.0 and TLS 1.1, had security flaws that made them vulnerable to attacks. These flaws could allow attackers to steal sensitive data like credit card details, passwords, or other personal information. For example, healthcare providers using these outdated protocols could make patient records vulnerable to unauthorized access and put private medical histories at risk. This is why TLS needed constant improvements to make it stronger, safer, and more reliable for securing online communication. Later, TLS 1.2 and TLS 1.3 were introduced. It improved security by using stronger encryption, fixing vulnerabilities, and improving performance for a safer online experience.
The National Institute of Standards and Technology (NIST) mandates that all government TLS servers and clients must support TLS 1.2 configured with FIPS-compliant cipher suites. Additionally, support for TLS 1.3 is required, starting from January 1, 2024. This directive is detailed in NIST Special Publication 800-52 Revision 2.
TLS 1.2 and Its Handshake
TLS 1.2 is a version of the TLS protocol that provides secure communication over the Internet. It was introduced in August 2008 as part of the IETF’s RFC 5246. It was designed to address the limitations and vulnerabilities of earlier versions like TLS 1.0 and TLS 1.1. This protocol is commonly used to secure activities, including online banking, email communication, and file transfers. Compared to earlier versions, it introduced stronger encryption algorithms, better performance, and enhanced security features.
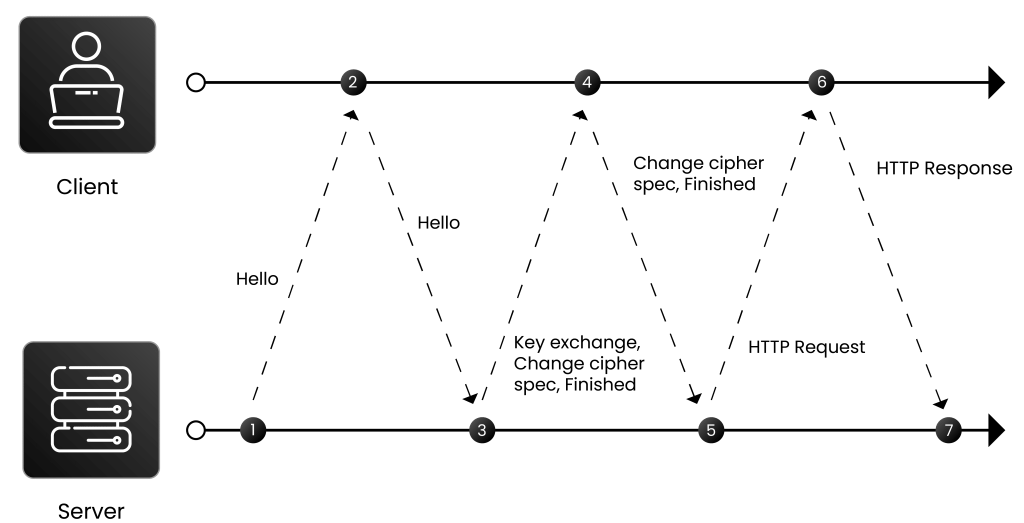
The TLS 1.2 handshake establishes a secure connection between a client and a server through two message exchanges or round trips (2-RTT).
- It begins with the client sending a “Client Hello” message, which includes its supported TLS versions, cipher suites, a random number for encryption key generation, and an optional session ID to resume a previous session.
- The server responds with a “Server Hello” by selecting a TLS version and cipher suite from the list provided in the “client Hello” message, providing its own random number and including a signed certificate with its public key. If the client included a session ID, the server checks for a cached session. Otherwise, it generates a new session ID. After sending a “Server Hello” message, the server waits for the client to proceed.
- The client then validates the server’s certificate to ensure it is trusted by a Certificate Authority. If mutual authentication is required, such as in enterprise environments, the server requests a client certificate. The client sends its certificate, which is validated by the server using a trusted CA. This confirms the client’s identity.
- Public key cryptography is used in the handshake process to securely exchange the session key, which guarantees confidentiality. Once authentication is done, the client sends a “Key Exchange” message with a pre-master key encrypted using the server’s public key. Even if an attacker intercepts the message, they cannot decrypt the pre-master key without the server’s private key. Only the server can decrypt this key because the private key corresponding to the public key is securely stored on the server and cryptographic devices like – Hardware Security Module (HSM) and key vaults and is never transmitted. Both the client and server use this pre-master key and their random numbers to generate a shared master secret. Then, the shared master secret is used to generate session keys.
- Finally, the client and server exchange “Change Cipher Spec” and “Finished” messages. It confirms that they are ready to switch to symmetric encryption using the session key. From this point onward, all communication is securely encrypted, and the session keys only last for the duration of the session.
Key Features of TLS 1.2
TLS 1.2 brought several enhancements to secure communications over computer networks. Key features include:
-
Enhanced Hashing Algorithm
The combination of MD5 and SHA-1 used in the finished message hash was replaced with more secure options like SHA-256 and SHA-384. However, the finished message hash must still be at least 96 bits in size.
-
AES Cipher Suites
TLS 1.2 introduced Advanced Encryption Standard (AES) cipher suites, which offer stronger encryption options by supporting 128-bit and 256-bit keys. It also protects data in transit and contributes to overall improved security.
-
Support for Authenticated Encryption
TLS 1.2 expanded support for authenticated encryption ciphers, notably Galois/Counter Mode (GCM) and Counter with CBC-MAC (CCM) modes of the AES. It provides better data integrity and confidentiality.
-
Improved Client and Server Negotiation
Both clients and servers can specify acceptable hash and signature algorithms during the handshake process, which enhances flexibility and security. This ensures compatibility while mitigating vulnerabilities associated with outdated or weak algorithms. For instance, if a specific algorithm becomes insecure (e.g., SHA-1), clients and servers can opt for stronger options like SHA-256 or SHA-384.
TLS 1.3 and Its Handshake
TLS 1.3 is the latest version of the TLS protocol, and it is designed to improve security and performance over its predecessor. TLS 1.3 was officially introduced in August 2018 with the publication of RFC 8446 by the IETF. The protocol is a result of the increasing need for stronger encryption, faster connection setups, and enhanced privacy features. TLS 1.3 introduced major improvements in security, speed, and privacy. It streamlined the handshake process, removed weaker cryptographic algorithms, and enhanced encryption methods. These changes provide a more secure and efficient communication framework for modern Internet protocols.
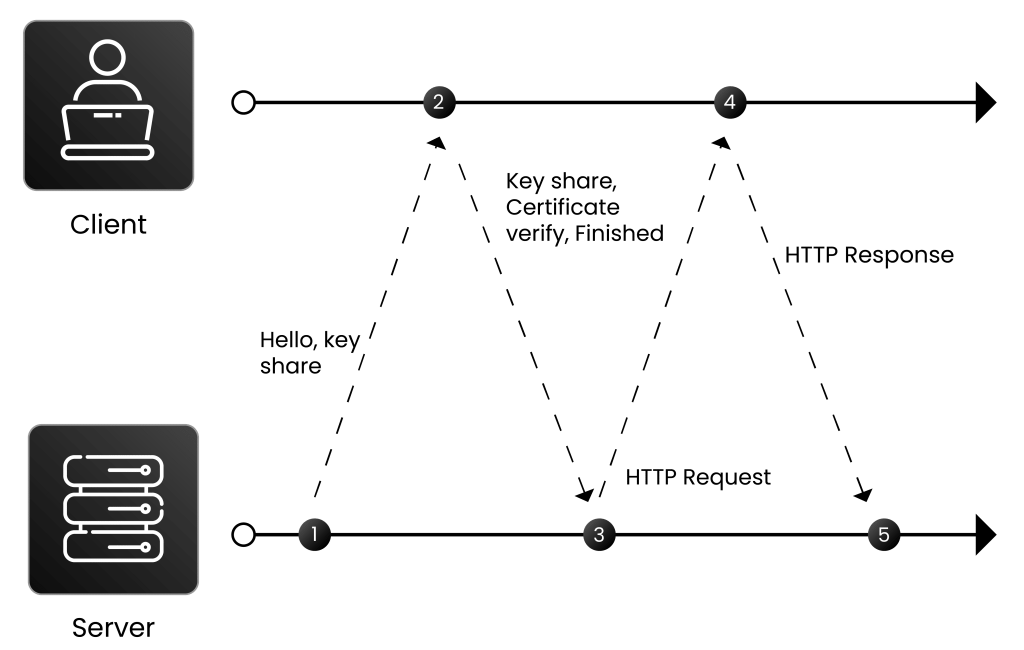
The TLS 1.3 handshake process happens in just one round-trip (1-RTT), which makes it faster than previous versions. The reduced latency of 1-RTT in TLS 1.3 is important for industries that require real-time communication. In online gaming, it provides smooth gameplay with less delay. Live-streaming platforms rely on fast connections to deliver content without interruptions. Financial applications including online banking and trading, benefit from quicker transaction speeds. Additionally, voice and video communication platforms, like VoIP and video conferencing, need low latency for seamless interactions.
- It starts with the client sending a “Client Hello” message. This message includes important information like the version of TLS the client supports (in this case, TLS 1.3), the list of cipher suites and key-exchange methods it supports, a random number generated by the client, and any extra extensions the client wants to include. The client sends its certificate if client authentication is enabled. The server can validate this certificate against the list of trusted CAs. This proves that the client is legitimate.
- In response, the server generates the master secret using the “ClientHello” random number, its own generated random number, client parameters, and selected cipher suites. The server then sends a “Server Hello” message along with a “Server Finished” message. This includes the protocol version selected by server, the cipher suites, the key exchange method, the server-generated random number, the SSL/TLS certificate, and any optional parameters.
- Once the client receives the server’s response, it verifies the server’s certificate against its list of trusted CAs to ensure it is communicating with the legitimate server. The client generates a master secret using its random number and the information from the server. After that, both the client and server send a “Finished” message to confirm they are ready for secure communication. At this point, both the client and the server share the same secret and can begin exchanging data securely, using encryption to protect their communication.
Key Features of TLS 1.3
TLS 1.3 introduces several key features that improve security, speed, and efficiency compared to previous versions.
-
0-RTT Data
TLS 1.3’s 0-RTT (Zero Round-Trip Time) data feature allows clients to send data during the handshake, reducing connection setup latency. This is beneficial for real-time applications like video streaming and gaming. In such applications, fast connection establishment is critical for smooth user experiences. It can also be useful in scenarios where repeated connections to the same server occur, such as in IoT devices that frequently reconnect to a central server. However, it is vulnerable to replay attacks and should be used carefully in sensitive scenarios when replay attacks can be effectively prevented. This is a concern because 0-RTT data is not protected by the same session keys as the rest of the communication.
-
Eliminates the RSA Key Exchange
In TLS 1.3, the RSA-based key exchange method has been removed in favor of stronger methods like ECDHE (Elliptic Curve Diffie-Hellman Ephemeral), which provides better security and performance.
-
Forward secrecy
It is a key security feature in TLS 1.3 and assures that the session keys are never transmitted or stored over the network and are discarded once the session ends. Even if a server’s private key is compromised in the future, past communications remain secure and cannot be decrypted. This feature protects long-term communication by ensuring that each session is independently encrypted using unique session keys that are generated for that specific session and prevents the compromise of one key from affecting the confidentiality of past data.
Comparison between TLS 1.2 and TLS 1.3
The transition from TLS 1.2 to TLS 1.3 represents a significant leap in terms of security, performance, and protocol efficiency. Below is a tabular comparison presenting the key differences between TLS 1.2 and TLS 1.3.
| Feature | TLS 1.2 | TLS 1.3 | Challenges |
|---|---|---|---|
| Handshake Process | Two round-trip times (2-RTT). | One round-trip time (1-RTT). | High latency in TLS 1.2 and TLS 1.3’s 0-RTT data increases the risk of replay attacks if not implemented securely. |
| Cipher Suites | Supports a wide range of cipher suites, including weaker ones. | Only AEAD (Authenticated Encryption with Associated Data) cipher suites are allowed, ensuring stronger security. | Legacy systems relying on weaker cipher suites require updates for TLS 1.3 compatibility. |
| Key Exchange | RSA, DHE, and ECDHE supported. | Only ECDHE supported. | RSA and DHE removal in TLS 1.3 complicates integration for systems relying on these methods. |
| Forward Secrecy | Optional. | Mandatory and forward secrecy is enforced by default. | Legacy systems not configured for forward secrecy need reconfiguration, potentially increasing migration efforts. |
| Encryption Algorithms | Includes outdated algorithms like RC4 and CBC. | Requires stronger algorithms like AES-GCM and ChaCha20-Poly1305. | Transitioning from deprecated algorithms requires updating libraries and applications. |
| Session Resumption | Uses session IDs or session tickets for resumption. | Supports session resumption with 0-RTT data, reducing latency. | TLS 1.3’s 0-RTT data risks replay attacks, while session tickets in TLS 1.2 may not be securely managed. |
| Security Improvements | Vulnerable to attacks like BEAST, POODLE, and Heartbleed. | Enhanced security with encrypted handshake messages and eliminates insecure protocols. | Migrating securely requires identifying and mitigating vulnerabilities in older TLS versions. |
| Certificate Validation | Supports certificate validation but can expose certain handshake details. | More secure, as handshake messages are encrypted. | Updating existing infrastructure to handle encrypted handshakes without compatibility issues is essential. |
| 0-RTT Data | Not supported. | Supported and allowed data to be sent during the handshake (but susceptible to replay attacks). | 0-RTT data risks replay attacks and requires careful validation and limited use in sensitive scenarios only. |
| Performance | Slower due to 2-RTT handshake and additional processing steps. | Faster due to a streamlined handshake and optimized key exchange. | High-latency networks benefit more from TLS 1.3, but the implementation must ensure proper support for optimized flow. |
TLS 1.3 is widely considered a better protocol compared to TLS 1.2 due to several key improvements in security, performance, and efficiency. First, TLS 1.3 enhances security by eliminating outdated and vulnerable algorithms (RC4, DES, MD5, and SHA1) and enforcing forward secrecy. It allows past communication to remain secure even if a server’s private key is later compromised. Meanwhile, TLS 1.2 supports weaker cryptographic methods and does not mandate forward secrecy. In terms of performance, TLS 1.3 offers a faster connection setup by reducing the handshake process to just one round-trip time (1-RTT), compared to the two or more RTTs required by TLS 1.2. This faster handshake significantly improves latency, especially for applications like online gaming.
Additionally, TLS 1.3 reduces computational overhead by simplifying the protocol as it streamlines the key exchange process by using Ephemeral Diffie-Hellman and eliminating the need for separate key exchange mechanisms like RSA, which were used in TLS 1.2. This reduction in complexity not only improves efficiency but also decreases the chances of implementation errors. TLS versions prior to 1.3 supported compression, but this feature was vulnerable to attacks. In TLS 1.3, compression is removed by sending a null byte in the legacy_compression_methods field. These factors make TLS 1.3 the preferred choice for modern, secure, and efficient web communications.
As of May 2024, a scan by Qualys SSL Labs shows that TLS 1.2 continues to maintain widespread adoption. This means that 99.9% of sites support version 1.2, while TLS 1.3 is used by 70.1% of sites, up from 67.5% in January 2024. The consistent rise in TLS 1.3 adoption reflects its enhanced security and reduced latency, which makes it the preferred choice for modern applications.
Migrating from TLS 1.2 to TLS 1.3 involves several significant challenges. Many legacy systems and devices are incompatible with TLS 1.3 and may require costly upgrades or replacements to support the newer protocol. This can be particularly difficult for industries relying heavily on older infrastructure. TLS 1.3 removes certain cryptographic features, such as RSA key exchange, which forces organizations to reconfigure systems to adopt more secure methods like Elliptic Curve Diffie-Hellman Ephemeral key exchange. This can disrupt applications depending on algorithms that are no longer supported by the new protocol.
TLS 1.3 introduces changes in the handshake process and session resumption mechanisms. These changes require updates to application logic, especially in systems with complex authentication or connection flows. Testing and validation become critical to guarantee that the migration does not break existing workflows or lead to performance issues. These challenges demand significant time, effort, and coordination among IT teams to provide compatibility and smooth integration.
Vulnerabilities
Though TLS 1.2 and TLS 1.3 are able to mitigate many of the risks associated with their predecessor. But no protocol is entirely perfect, and they both have their vulnerabilities. TLS 1.2 does not mandate the use of MD5 or SHA-1, but it supports them for backward compatibility. The protocol allows for their use if a server or client explicitly chooses them. TLS 1.2, while widely adopted, is vulnerable due to its support for weaker cryptographic algorithms like MD5 and SHA-1. These are prone to collision and brute force attacks.
TLS 1.2 has been exploited through various high-profile attacks that target its vulnerabilities. The BEAST (Browser Exploit Against SSL/TLS) attack exploited weaknesses in the Cipher Block Chaining mode and allowed attackers to decrypt portions of intercepted encrypted traffic. Similarly, the Heartbleed vulnerability in OpenSSL’s implementation of TLS allowed attackers to extract sensitive information, like private keys and session data, from server memory using malicious heartbeat requests. The POODLE (Padding Oracle on Downgraded Legacy Encryption) attack leveraged flaws in CBC mode padding and exploited scenarios where servers supported fallback to less secure protocols like SSL 3.0.
Additionally, the Raccoon attack targets the Diffie-Hellman key exchange process by using timing-based side-channel techniques to measure slight variations in the computation times of the key exchange. This can allow attackers to recover parts of the session key and compromise the confidentiality of the communication. Maintaining backward compatibility and strong security is difficult.
TLS 1.3 addresses many of these weaknesses by removing outdated cryptographic algorithms and simplifying the handshake process, but it is not entirely immune to implementation-specific vulnerabilities. These vulnerabilities often arise from how various libraries, servers, or applications implement the protocol. For example, flaws can occur if nonces— random numbers or initialization vectors (IVs)—which are used to initialize certain encryption algorithms like CBC or AES-GCM—are not properly randomized. It can lead to predictable encryption patterns that could be exploited. Improper handling of key exchange mechanisms can expose private keys if parameters are weak or reused. Misconfigurations, such as choosing weak cipher suites or not properly setting up forward secrecy, can also reduce security.
To mitigate risks associated with TLS 1.3 implementation-specific vulnerabilities, it is important to ensure the use of strong cryptographic parameters. Configurations like selecting high-quality elliptic curves, using secure key rotation, proper random number generation, and avoiding weak or deprecated cipher suites like RC4 and DES are vital. It’s also crucial to disable fallback to older protocols like TLS 1.2 or SSL, which could expose vulnerabilities. Regular patching and updates of TLS libraries should be prioritized to fix newly discovered flaws. Detailed security audits and continuous vulnerability scanning are essential to detect misconfigurations, weak keys, or outdated components and ensure that TLS 1.3 implementations remain secure and up to date.
The NIST has highlighted a vulnerability in the Cisco Firepower Threat Defence (FTD) Software’s TLS 1.3 policy with URL category functionality, which could allow unauthenticated remote attackers to bypass configured URL blocking policies. This situation is caused by a logic error in Snort’s handling of TLS 1.3 connections and can be exploited using specially crafted TLS 1.3 requests. It allows access to restricted URLs that would typically be blocked.
How Can Encryption Consulting Help?
At Encryption Consulting, we help organizations to address the challenges in transitioning from TLS 1.2 to TLS 1.3 by providing customized encryption solutions. These solutions help to meet the unique security needs of our clients. Our team of highly skilled experts offers a wide range of services, including in-depth assessments, audits, strategy planning, and implementation of a smooth migration process. We assist clients in identifying compatibility issues, configuring dual protocol support, and optimizing encryption settings to enhance security. By offering personalized guidance throughout the transition, we ensure that the migration to TLS 1.3 aligns with the client’s specific security objectives while minimizing risks and disruptions.
Conclusion
TLS is important for keeping data safe when it travels across networks. It uses public key encryption and a handshake process to secure communication between clients and servers. While TLS 1.2 is still widely used because it works well with many systems, TLS 1.3 is becoming more popular. This is because TLS 1.3 offers faster connections, better security, and a simpler design. It reduces delays, makes websites quicker, and improves user experience. It also removes weak features and fixes vulnerabilities from earlier versions, making it much harder for hackers to exploit.
Organizations transitioning from TLS 1.2 to TLS 1.3 should first assess their infrastructure for compatibility and ensure critical systems support the new protocol. A phased approach should be taken, initially enabling TLS 1.3 in a testing environment and removing outdated protocols. Security teams should be trained on TLS 1.3 best practices, and backward compatibility with TLS 1.2 should be maintained temporarily until full migration is achieved. Backward compatibility is required during the migration period because it ensures that systems and clients that do not yet support TLS 1.3 can still communicate securely by using TLS 1.2. This guarantees that users and services continue to work smoothly during the transition while reducing interruptions.
Without backward compatibility, organizations can face risks of breaking connections with older systems, devices, or clients that rely on legacy protocols, which could lead to service disruptions or security problems. Moreover, regular testing and vulnerability assessments are essential throughout the process. TLS 1.3 is not directly backward compatible with TLS 1.2, meaning that it cannot be directly used with systems that rely on older versions of TLS. Because of this, businesses are advised to support both versions during the transition. This approach ensures secure data transactions for older systems while allowing the adoption of the improved and more secure TLS 1.3 protocol for newer applications and websites.




