- What are machine identities in Kubernetes?
- What is the Zero Trust Environment?
- Necessity of machine identities security for organizations
- Machine Identity Management Platforms
- HSMs and TPMs
- How can machine identity management aid in meeting compliance standards?
- Future of machine identity security
- Best practices
- How Encryption Consulting strengthens machine identity security
- Conclusion
In today’s fast-changing digital world, the way you deploy and manage applications has transformed with the rise of cloud-native technologies. Platforms like Kubernetes make it easier for you to efficiently manage containerized applications by providing flexibility and scalability for your systems. When you adopt Kubernetes, securing your machine identities becomes critical—especially in a Zero Trust environment. Here, you will learn why securing machine identities in Kubernetes is a necessity and how using a Zero Trust approach can remarkably strengthen your security. It also helps you stay ahead of modern threats and protect your most valuable resources.
What are machine identities in Kubernetes?
In Kubernetes, machine identities refer to the unique identifiers assigned to various components that include nodes, pods, services, and users. You can think of cryptographic credentials, digital certificates, and tokens as examples of machine identities. These identities are important because they help you authenticate and authorize access to the resources in your cluster. With Kubernetes environment’s scaling, the management of these identities becomes increasingly complex. And it has become more crucial than ever to implement strong security measures.
Also, machine identities outnumber human identities by a great margin. Machine identities are always in high demand due to the growth of microservices, cloud computing, IoT, and containerized environments. Machine identity management is required and can also become a huge challenge for your businesses. By using machine identity management platforms, you can automate the whole process of managing machine identities in complex systems.
What is the Zero Trust Environment?
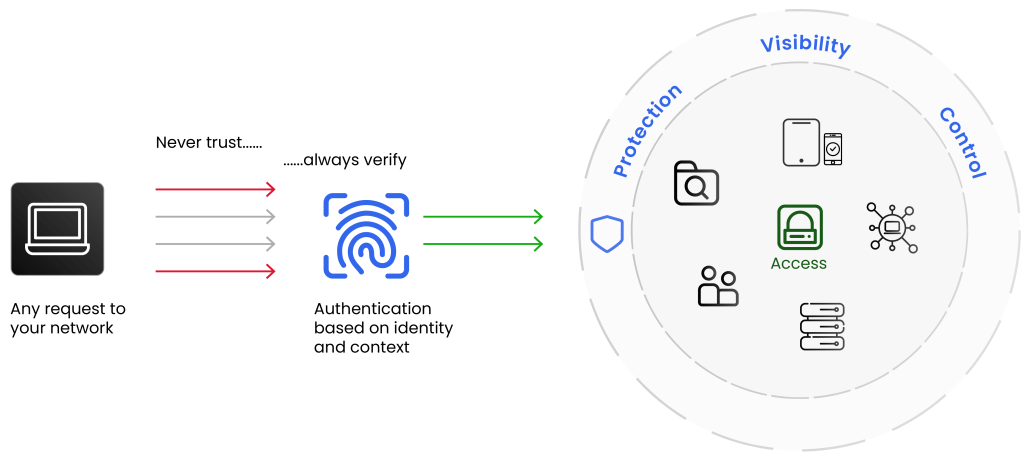
The idea behind a zero-trust environment is simple: “Never trust, always verify.” A threat can be there in an unrecognizable form, and you should always be ready for it. Every incoming request to access your system should be considered a potential threat and should be inspected. This means you need to have stricter access controls and constantly check who is trying to access your system. It is not like traditional methods where you trust the identities inside the network. Here, you need to understand that these security measures are uniform for identities trying to access from inside or outside the network perimeters. It is all about staying cautious and making sure only the right people get access.
According to Gartner, by 2025, over 60% of organizations are expected to adopt Zero Trust frameworks as a core element of their cybersecurity strategy.
Granularity control in a zero-trust environment refers to the ability to enforce security policies at a very detailed level, such as per user, per device, per application, or even per session. It ensures that access to resources is not granted based on broad trust assumptions. Some factors based on which access is granted are the user’s role, device health, location, time of access, and the sensitivity of the resource being accessed.
Granularity control is important to minimize the attack surface by ensuring that only the precise level of authorized access is granted. It also limits the potential damage caused due to a compromised account or device. It allows organizations to apply the principle of least privilege more effectively, enhance security, and reduce the risk of lateral movement or unauthorized access to the system.
Necessity of machine identities security for organizations
Machine identity security is essential because machines (including servers, applications, containers, and IoT devices) are a critical part of the modern digital world. These machines communicate with each other in high-volume and sensitive environments autonomously. Ensuring their identities are secure is necessary to maintain trust, prevent unauthorized access, and safeguard data. Without proper machine identity management, malicious actors can exploit vulnerabilities, impersonate trusted machines, and launch attacks such as data breaches, ransomware, or distributed denial-of-service (DDoS).
Strong security of machine identities prohibits the unauthorized access of threat actors. By securing these identities, organizations can prevent unauthorized access, data breaches, and potential exploitation by malicious actors impersonating legitimate systems. Attackers increasingly target machine identities to impersonate trusted devices or services. Implementation of these security measures results in a reduction of several attacks that include man-in-the-middle attacks, API abuse, and other cyber threats that exploit vulnerable identities to gain access to sensitive systems. Machine identities are key to maintaining the trustworthiness of organizational data and systems. Secure identities help ensure data integrity by allowing only verified machines and applications to access or modify sensitive data.
In DevOps environments, speed is critical, and many IT leaders agree that automated management of machine identities is essential for supporting continuous delivery while maintaining security. Therefore, machine identity security is crucial to secure your data and comply with regulations. A zero-trust environment also ensures that your company’s sensitive identities are not lost, misused, or accessed by unauthorized users.
Machine Identity Management Platforms
The problem that you need to address here is managing machine identities. It can be resolved by using the right tools, which automatically make sure everything runs smoothly and stays secure. MIM platforms are designed in such a way that they help you take control of the entire lifecycle of machine identities. It does so by keeping your infrastructure safe. Here is how they can make a difference for you:
-
Create and Issue
These platforms allow you to securely create and issue machine identities, including tokens and digital certificates. This ensures that only trusted machines and devices can access your system and maintains your overall security. MIM platforms simplify management for you as you can easily create, update, or revoke identities. This makes it easy for you to deal with any potential risks.
-
Auditing
You also need regular audits to prove compliance with security rules. MIM platforms provide you with detailed audit logs that give you clear visibility into every action taken with machine identities. It helps you to stay on top of industry regulations.
-
Monitoring
Another important feature is the ability to monitor your system for suspicious activity. These platforms continually keep an eye on your machine identities and alert you about any unusual behavior. If something looks wrong, then you can take action right away and stop potential threats before they cause any harm.
-
Management
This feature ensures effective handling of machine identities and covers key tasks like provisioning, access management, revocation, and rotation of machine identities.
HSMs and TPMs
HSMs (Hardware Security Modules) and TPMs (Trusted Platform Modules) are both physical devices used to protect sensitive information, such as cryptographic keys, certificates, and passwords. They are important for ensuring the security of machine identities, especially in systems like Kubernetes that manage multiple machines or services.
HSMs are specialized devices that store and manage private keys securely, ensuring that unauthorized users cannot access them. They also help with important security tasks like digital signing and secure boot, which verify the authenticity and integrity of machine identities. TPMs are hardware chips built into devices that secure identity credentials and perform checks to ensure the system hasn’t been tampered with before allowing access to Kubernetes clusters. They help verify that the device is trustworthy by performing attestation or integrity verification.
HSMs and TPMs help organizations comply with industry standards such as FIPS 140 Level 3, PCI DSS, SOC 2, ISO 27001, and GDPR, ensuring secure key management, cryptographic operations, and data protection. In cloud environments, cloud services with HSMs (e.g., AWS Cloud HSM, Google Cloud HSM, and Azure Key Vault HSM) offer scalable, highly available key management solutions that integrate seamlessly with Kubernetes. These HSMs enable secure service-to-service communication, encrypted secrets, and identity federation across multi-cloud environments. According to this report, the HSM market size is expected to reach USD 2.84 billion by 2030, driven by the increasing demand for secure, reliable solutions for machine identity management.
To further strengthen security, Certificate Authority (CA) and Public Key Infrastructure (PKI) systems integrate with HSMs and TPMs to generate, manage, distribute, and recover machine identities efficiently, ensuring secure communication between machines and services. Additionally, Machine Identity Management (MIM) platforms leverage HSMs and TPMs to automate credential issuance, revocation, and rotation, reducing the risk of human error. These technologies enhance compliance, simplify management, and support granular access control, strengthening the overall security posture.
How can machine identity management aid in meeting compliance standards?
Machine Identity Management (MIM) is central to organizational strategies to achieve compliance with regulations such as HIPAA, PCI-DSS, and GDPR through secure access control, data encryption, and automated identity management in a digital space. Now, let us understand MIM in relation to these compliance requirements:
-
Enforcement of secure access control and authentication
Machine Identity Management allows access to sensitive information only to the machines that are allowed by certain policies that assist compliance with HIPAA, PCI-DSS, and GDPR. The use of access management policies to ePHI (Electronic Protected Health Information) is mandatory under HIPAA compliance for health institutions, where access to protected information systems is limited to authorized personnel only. In addition, equipment used in processing payment transactions falls under the scope of the Payment Card Industry (PCI) due to the sensitive nature of the data handled. Hence, MIM facilitates strong authentication-based platforms for the management of certificates and digital keys so that compliance is met.
-
Data encryption and protection
MIM assists organizations in managing the deployment of encryption technology so that the relevant provisions of the data protection laws in the GDPR, HIPAA, and PCI DSS can be achieved. The GDPR’s main principles highlight guidance on the processing, storage, and transport of PII through encryption. In the case of HIPAA, there is also guidance that informs organizations on encrypting any ePHI information stored in their systems to reduce the chances of it being accessed by malicious users, and PCI DSS requires the storage of confidential payment information to be encrypted. MIM enforces encryption policies and reduces the risk of data loss by incorporating a system for managing encryption keys and certificates throughout all machinery used for communication.
-
Monitoring, auditing, and reporting
Machine Identity Management simplifies the monitoring and auditing of machine identities, helping organizations meet the rigorous logging and reporting requirements of PCI-DSS, HIPAA, and GDPR. PCI-DSS requires detailed logging of access to cardholder data, while HIPAA and GDPR demand comprehensive audit trails to document all access and processing of sensitive data. MIM provides centralized logging of machine identity activities, allowing organizations to generate audit-ready reports and demonstrate compliance with these standards by maintaining a traceable record of machine interactions.
-
Automated identity lifecycle management
Identity Lifecycle Management for machine entities is needed in as much as the security controls of the policies that include HIPAA and PCI-DSS and GDPR stipulate the need for timely issuance and withdrawal of digital certificates. MIM automates the processes of certificate issuing, renewing, and revoking. Instead, the risk of having poorly managed credentials that may be very weak and cause security threats is significantly mitigated. By virtue of mechanizing the process, MIM also takes care of the concerns relating to the risk of machine identities remaining outdated and insecure, helping the users of these services adhere to the above reasons without inducting the manual control of certificates.
Future of machine identity security
The future of securing machine identity will prioritize scalability, automation, AI integration, and resilience to address the expanding IoT, cloud, and hybrid environments. With the increased number of connected devices, lightweight cryptographic protocols like Elliptic Curve Cryptography (ECC) will ensure secure communication for resource-constrained devices. Automation will streamline certificate lifecycle management, which includes issuance, renewal, and revocation. It reduces human error and ensures continuous protection.
Artificial intelligence (AI) and machine learning will enhance threat detection by identifying anomalies in machine behavior and automating real-time remediation, making security more adaptive. Zero trust architectures will enforce strict authentication and continuous verification of machine identities and reduce the attack surface across networks.
Quantum-resistant cryptography, such as lattice-based algorithms, will protect against future quantum computing threats, ensuring the integrity of machine identities. For containerized applications and microservices, technologies like Service Mesh will enable secure identity management for ephemeral workloads, ensuring encrypted communication between dynamic services. Blockchain-based solutions may also provide decentralized, tamper-proof records for managing identities.
These advancements will create more robust, scalable, and adaptive systems to safeguard against cyber threats and ensure compliance with standards like GDPR, HIPAA, and PCI-DSS while securing interconnected ecosystems.
Best practices
These practices ensure secure and reliable communication channels, block unauthorized access, and prevent excessive permissions from being misused. By using role-based access control (RBAC), secure service accounts, service meshes, continuous monitoring, and regular security checks, organizations can improve their security. These measures protect machine identities and make the entire system stronger and more trustworthy.
-
Adopt role-based access control (RBAC)
You should use RBAC to define and enforce permissions for users and service accounts. This ensures that each entity has the minimum level of access necessary to perform its functions and limits potential attack vectors. Regularly auditing and reviewing RBAC policies is essential to adapt to changes in your Kubernetes environment, especially when combined with a zero-trust strategy.
-
Use service account security policies
You should assign each application or microservice its own service account to limit permissions to only what is necessary. This helps reduce the risk of privilege escalation and keeps access tightly controlled.
-
Utilize service mesh
Implementing a service mesh (such as Istio or Linkerd) to manage communication between services is a good practice. Service meshes provide features like traffic encryption, visibility, and policy enforcement, which improve the security of machine identities. You can also implement mutual authentication and authorization for all inter-service communication within the service mesh to enforce stronger security policies.
-
Monitoring and auditing machine identities
Continuous monitoring of machine identities and their associated activities is essential. Tools like Kubernetes audit logs can help detect anomalous behavior and potential security breaches. You must set up alerts for unusual access patterns or attempts to access unauthorized resources, enabling proactive incident response.
-
Conduct regular security assessments
You must perform routine security assessments to identify vulnerabilities in your Kubernetes environment. Penetration testing and vulnerability scanning can help uncover weaknesses related to machine identities. To minimize the risk of exploitation, promptly addressing any identified issues is important for you.
How Encryption Consulting strengthens machine identity security
Encryption Consulting strengthens machine identity security by offering an effective solution that simplifies the management and protection of machine identities within Kubernetes environments. CertSecure Manager automates the entire lifecycle of machine identities and makes their issuance, renewal, and revocation seamless. This approach addresses common certificate-related challenges and resolves them by reducing manual intervention and downtime. It provides a unified dashboard for managing machine identities across on-premises and cloud-based Certificate Authorities (CAs). This way, visibility and control over the lifecycle of certificates, CRLs, and renewals is centralized.
Our solution, CertSecure Manager, enforces strict policies for machine identity issuance and management, including approval processes, CSR reuse restrictions, and role-specific access to certificate templates. These controls enhance compliance and security. Leveraging the principle of least privilege, Encryption Consulting enables role-based permissions through CertSecure Manager, ensuring users have access only to tasks necessary for their roles, reducing the risk of unauthorized activities.
It also integrates with platforms like Teams, email, and ServiceNow to provide real-time alerts for expiring certificates or PKI issues. Organizations can save time, reduce risks, and improve compliance by automating certificate management, connecting it with existing workflows, and keeping track of everything with proper monitoring. Integration with AD groups simplifies the onboarding process by automating the certificate lifecycle management.
Conclusion
To summarize, machine identity management in Kubernetes solutions is extremely important in a zero-trust architecture. As Kubernetes is implemented more frequently for the deployment of cloud-native applications, the agile nature of its deployments, characterized by short-lived workloads and microservices, requires continuous user authentication and access controls. The use of additional authentication protocols between pods, nodes, and external services eliminates the possibility of unsecured communication and unauthorized access.
Having implemented least-privilege access and utilizing such techniques as service meshes, as well as Identity and Access Management (IAM), is important for the proper security of machine identities. In addition, such tools provide very restrictive access control, as permission to talk to each other in the Kubernetes domain is granted only to specific services, which is an additional layer of security. Also, the continuous verification of all machine-side identities without any implicit trust ensures that the attack surface is limited.
- What are machine identities in Kubernetes?
- What is the Zero Trust Environment?
- Necessity of machine identities security for organizations
- Machine Identity Management Platforms
- HSMs and TPMs
- How can machine identity management aid in meeting compliance standards?
- Future of machine identity security
- Best practices
- How Encryption Consulting strengthens machine identity security
- Conclusion

